What Is a Digital Signature? A Look at Digital Signatures in Cryptography
How do you spot fake software, emails, and files among the colossal amounts of data consumed every year (e.g., more than 100k exabytes in 2022 alone, according to IDC)? Explore how digital signatures can help your organization to guarantee the security, integrity, and authenticity of products and data in the digital world
2023 has barely started and we’ve already witnessed several big names data breaches. From T-Mobile’s latest incident that affected 37 million accounts to PayPal’s 35,000 hacked accounts, it really seems that cybercriminals aren’t resting on their laurels this year.
How can you protect yourself and your organization in such a dangerous environment where every action could be potentially harmful? How do you know that the email you’ve just received from your boss is really from him? And how can you prove to your customers that the software they’ve just downloaded from your website is authentic and harmless?
The answer? You can check these things through digital signatures. Discover in this article:
- What digital signatures are,
- How they work,
- Where they’re used, and
- Why they’re a key element of every organization’s cybersecurity plan and reputation.
Ready to learn something new? Let’s go!
What Is a Digital Signature in Cryptography?
A digital signature (i.e., a public key signature) is an enhanced and secure digital identifier. It’s part of the electronic signature family (more on that in a moment), but it’s more secure than a digital version of a handwritten signature. That’s because it uses cryptography to confirm the origin, authenticity, and integrity of a digital asset (e.g., a document, an email, or a piece of software) to show that the signer created it.
How? During one of my trips to Japan, I bought a hand-made ceramic tea bowl from a talented craftsman in a small village in the Japanese highlands. I remember turning the bowl over and noticing a mark on its foot ring, followed by what looked like a signature.
When I asked him what it was, he told me it was how Japanese artists were used to authenticating and signing their works. By applying his personal name seal (i.e., hanko) and his handwritten signature somewhere on the item, he was confirming that he really made it (origin and authenticity) and that it hadn’t been modified by somebody else (integrity).
Digital signatures are more complex, but they work more or less the same way. Instead of using a manual seal and a handwritten signature, they rely on:
- Public key infrastructure (PKI). A security system using asymmetric encryption (i.e., a process using a public key for encryption and a private key for decryption), and
- A digital certificate. A file issued by a trusted certificate authority (CA) confirming the identity of the owner.
Once a message or file is digitally signed, the recipient can be sure that:
- The message has been sent by the real sender (authentication).
- The message hasn’t been modified (integrity).
- The sender can’t deny he sent the message (non-repudiation).
These three tenants — authentication, integrity, and non-repudiation — are the three vital uses of a digital signature. We’ll further explore these three security elements in our next article (stay tuned for that).
Now, before moving on to find out in detail how a digital signature work, there’s still something we need to point out. A moment ago, we said that a digital signature is a form of electronic signature. But what if I also tell you that all digital signatures are electronic signatures, but not all electronic signatures are digital ones? Confused? Let’s clarify this.
Digital Signatures vs. Electronic Signatures. What’s the Difference?
Many people use the terms “digital signature” and “electronic signature” interchangeably. They think that, as digital signatures are a form of electronic signature, there is no difference between the two. Wrong. It would be like calling all birds chickens. We all know that chickens are birds, but not all birds are chickens, right?
Applying this logic to the topic at hand, how does a digital signature differ from an electronic signature? Let’s check out the comparison table below:
| Features | Digital Signature | Electronic Signature |
|---|---|---|
| Purpose | Proves the authenticity and integrity of a document, just like a notarized signature. | Confirms the intent of signing a document. |
| Identity Validation | Performed by a trusted certificate authority (CA) through the release of a digital certificate. | No identity validation. |
| Level of Security | Highly secure thanks to the use of hashing and encryption. | Vulnerable to tampering and man-in-the-middle attacks. No encryption used. |
| Visual appearance | Looks like a digital fingerprint. | Looks like an electronic copy of a handwritten signature. |
| Uses | Secure documents, codes, emails, and files. | Documents verification. |
In summary, even if there are some overlaps (e.g., they’re both utilized to authenticate a digital document by a signature), a digital signature is used to secure documents and other digital assets like software or emails. On the other hand, the electronic signature is used to sign a digital document like a contract, just as you’d sign it with a pen.
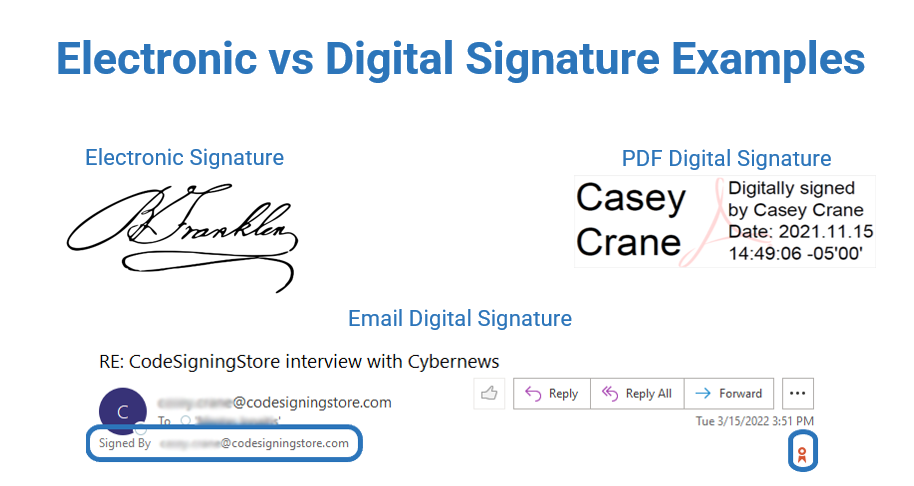
Got it? So, from now onward, no more calling all birds chickens!
How a Digital Signature Is Created and Verified
As we already know, digital signatures use PKI. A public key and a private key (key pair) are generated through a mathematical process using a public key cryptographic algorithm (e.g., Rivest-Shamir-Adleman – RSA algorithm). The digital signature is created using hashing and encryption cryptographic functions. Of course, you also have the option of adding a timestamp, which provides a verifiable way to show when the document was first signed.
Here’s the important note: The resulting encrypted hash value is your digital signature. The digital signature is then appended to the data. Et voila’ — the data is signed and ready to be verified by the recipient using the certificate’s public key and by generating a hash value to see if it matches the one provided.
Let’s take a closer look at these processes.
How to Create a Digital Signature
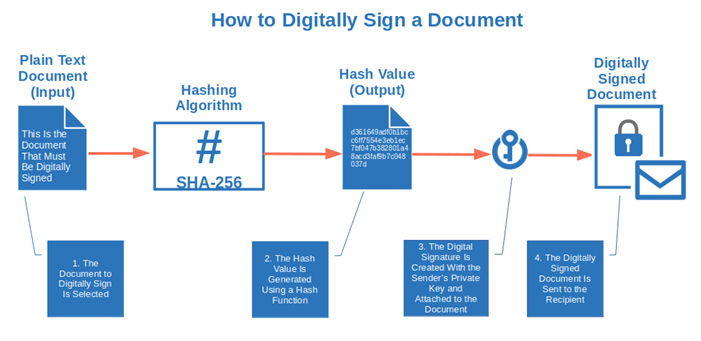
Let’s see a practical example of how to create a digital signature. Let’s say you’ve just created a Microsoft Office document and you want to send it to your boss. To make sure the document reaches your boss without any tampering by a malicious party, you decide to digitally sign it. How?
- Hash the file. After selecting the file you want to sign (input), apply a cryptographic function (i.e., hash algorithm) to it. In this example, we’ll assume you used the secure algorithm SHA-256. As a result, a unique 256-bit hash value (output) is generated in the form of a fixed-length string of 64 hexadecimal characters.
- Create your digital signature by encrypting the generated hash value. It’s now time to add another layer of security to the hash value. Remember when we talked about PKI and the digital certificate? This is where you’re going to use them. The hash value is encrypted using your private key. Your PKI digital signature is created, ensuring the integrity of your file.
- Send the signed document. Now that you’ve signed your file, you can send it to your boss with a copy of your public key. He’ll then be able to use that key to verify that the file really came from you (authentication) and that it hasn’t been modified (integrity). On top of this, as the file has your signature, it makes it nearly impossible to deny that the file has been signed by you (non-repudiation) so long as your private key hasn’t been compromised.
How to Verify a Digital Signature
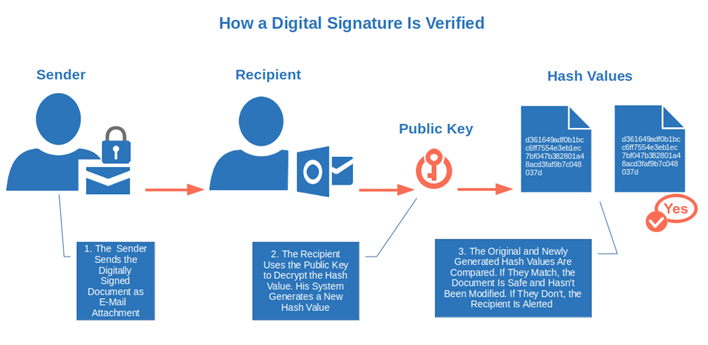
So, what happens when your boss receives the file?
- The received hash value is decrypted. Once your boss downloads the file, their system uses the public key to decrypt the hashed value. Note that this happens in the background in a fraction of a second. Your boss won’t even notice.
- A new hash value is generated and compared with the document hash value. This is when the integrity of the data is validated. The system generates a new hash value of the downloaded file and compares it with the original hash value. If they match, the file is legitimate and hasn’t been modified since it was signed. If they don’t, your boss will get an error message warning him that the file has been compromised.
Isn’t this a clever way to create trust and protect your organization, users, and customers from unwanted malware infections and data breaches? If you want to protect your users and/or customers and help them spot fraudulent emails or malicious files and software, then be sure to use digital signatures to assert your verified digital identity.
Want to know more about the relationship between PKI and digital signatures? Check what the Cybersecurity and Infrastructure Agency (CISA) has to say about it!
Now that you know how this whole mumbo-jumbo works, why don’t we have a look at how, and where digital signatures are used?
Four Ways Digital Signatures Protect You in the Digital World
Anyone using a computer has surely already encountered (and used) digital signatures, often without even knowing it. Let’s explore a few situations where digital signatures protect you from malware and from the bad guys lurking out there.
1. Email Authentication
Have you ever heard of business email compromise (BEC)? It’s a type of scam targeting big and small organizations. Attackers impersonate a CEO or a company executive to trick employees to share sensitive information or transfer huge amounts of money to their accounts.
How do they do that? Often through emails. How popular is it? The latest Expel report shows that in 2022, BEC was their customers’ top threat, representing 50% of the incidents. The FBI’s Internet Crime Complaint Center (IC3) shares that BEC-related complaints had reported losses of nearly $2.4 billion in 2021.
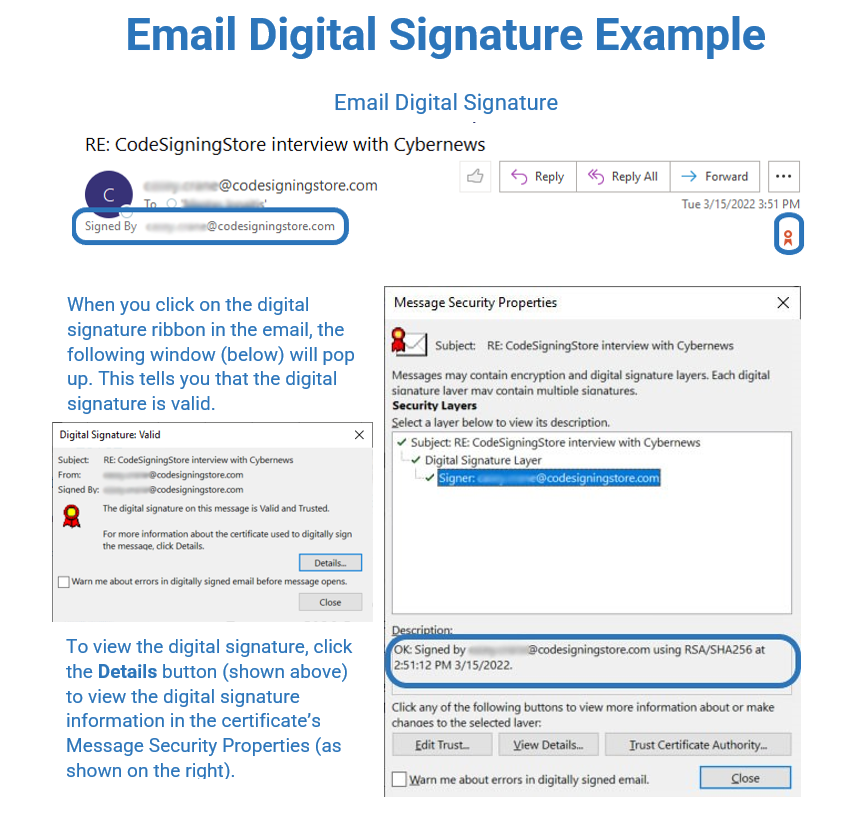
If you want to protect your organization from it, then add a digital signature to your emails and attachments. Your recipients will always be sure that what they receive from you is really coming from you and hasn’t been modified.
How do you do that? You just have to add an email signing certificate to your email client (e.g., Thunderbird or Outlook). Once done, enable the digital signing feature (the process may vary slightly depending on the client used). From now onward, every time you send a digitally signed email, a verification logo will appear on the email, confirming that the email has been signed and sent by you.
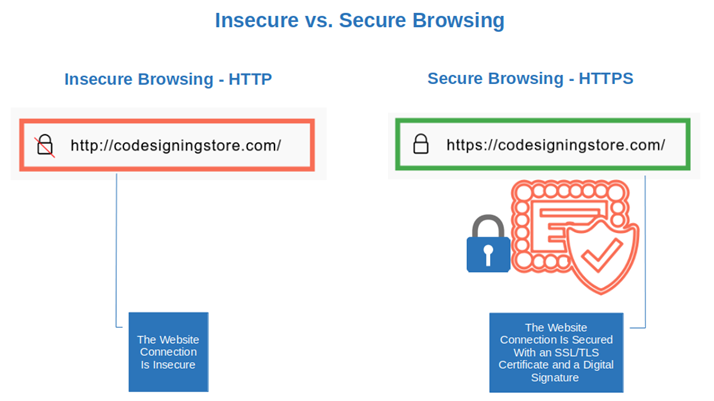
2. Secure Browsing
Did you know that in January 2023, 94% of the traffic of all Google websites used the hypertext transfer protocol secure (HTTPS) by default? Why? Because it’s much more secure than the insecure HTTP protocol as it also uses a digital signature and it encrypts your website traffic. Our website codesigningstore.com uses HTTPS, too, as you can see from the tiny padlock that displays in your browser’s web address bar.
How does it work? When you open an HTTPS-enabled website, the web server sends a secure socket layer/transport layer security (SSL/TLS) certificate to your browser. The certificate includes information about the website’s domain and the digital signature of the CA that issued the certificate. Once again, your browser verifies the digital signature during the SSL/TLS handshake process to create a secure and encrypted connection.
The advantage? Every single piece of information sent through that connection will be encrypted thus, safe from prying eyes. Want to ensure that when your customers use their credit cards to pay online for your services or products, their card details won’t be stolen by cybercriminals while in transit? Add a digital signature to your website to make the data as secure as possible.
3. Codes and Software Authenticity
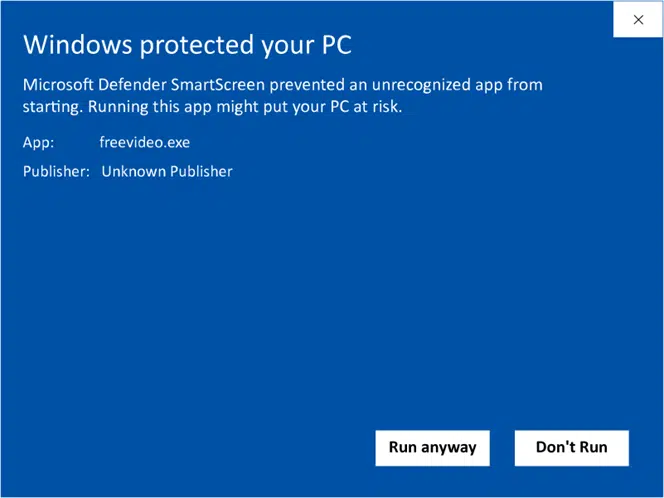
Are you a developer and want to boost your downloads by ensuring that you get rid of the “Unknown publisher” warning message that could scare off your existing and potential customers?
Using a digital signature will help you here, too, and you even have two options to choose from:
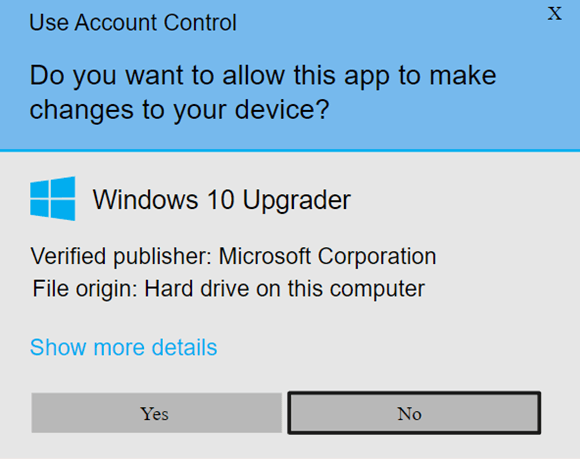
- Sign your software or code with an organization validation (OV) code signing certificate. This will allow you to display your organization’s information on the Windows Defender SmartScreen and User Access Control installation warning pop-ups. Also called a class two digital signature, it’s used for digital assets in moderate-risk environments.
- Take it to the next level and use an extended validation (EV) code signing certificate. Digitally signing your software ensures it’s automatically trusted by Windows browsers and operating systems. In this case, no warning will show for EV certificate signed software. Offering the highest level of security, these class three signatures are the best option for organizations and high-risk environments.
4. Confirm Files Authenticity
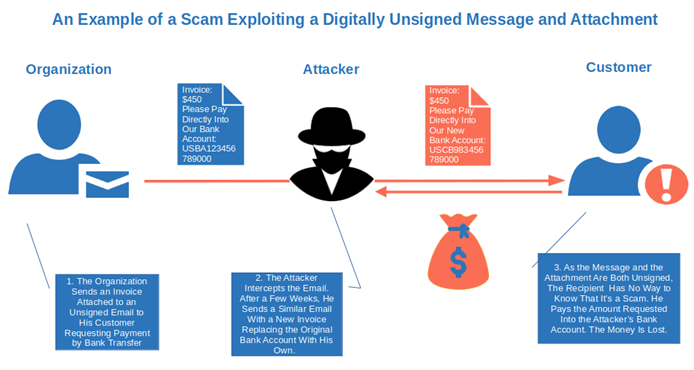
My best friend worked in the account payable department of a big company. I remember an interesting story he told me. One day, one of their customers called him to inquire about an invoice. He had just received a follow-up email from the company my friend was working for regarding a payment that was due the following week.
The second email included a new invoice with the same amount. However, the customer was requested to pay it into a different bank account due to some issues with the old one. As the customer got suspicious — and rightly so — he got in touch with my friend’s department to verify the email’s legitimacy. To keep the story short, it came out that both the second email and its invoice were fraudulent. That customer dodged a bullet and so did my friend’s company. Can you imagine what would have happened if he hadn’t double-checked with the company and just paid the invoice as requested?
A few days after the incident, my friend told me that the organization bought a document signing certificate and started adding a digital signature to all files. No exceptions allowed. This way, customers could always verify the authenticity of the invoices and documents received from the company instead of risking giving their money to scammers.
What we’ve seen so far are just a few examples of how digital signatures are used in the digital world. But there are more, depending on the industry and different needs. Here are a few examples:
- Government documents and forms. Digital signatures are often used by governments worldwide to process tax returns and manage contracts. The U.S. federal government for example, also uses them to publish budgets, laws, and bills. An updated digital signatures standard has just been published by the National Institute of Standards and Technology (NIST) beginning of February 2023.
- Cryptocurrencies. If you’re familiar with cryptos, you’ll probably know that digital signatures are used to authenticate the blockchain and manage transaction data.
- Legal documents and contracts. Digital signatures are legally binding, just like your handwritten legal signature. But they offer something more: they prove to the person signing the document/contract that it’s legitimate, and that it hasn’t been modified since it was created.
- Healthcare. In some countries, like Germany for example, when you go to the doctor, you use a card with a chip where an extract of your patient record and sensitive information is securely stored. The digital signature is included, too.
And the list could go on and on, but it’s clear now that digital signatures are pretty popular and are quickly becoming a key part of our daily life. This still didn’t win you over? Let me give you some more hints about the benefits digital signatures will bring to you as an organization or as a developer.
Why Should Your Organization Use Digital Signatures?
We live in a world where paper documents are largely being replaced by electronic files. Digital signatures enable you to show customers and users that your documents or codes are authentic and haven’t been modified by a malicious third party. But what are the other advantages introduced by the usage of digital signatures?
- Reduce the risks of phishing attacks, data breaches, and manipulation. Fraudulent communications tricking the recipient into revealing sensitive information like passwords or credit card numbers are on the rise. In 2022, Slashnext observed an astonishing 61% increase in phishing compared to the previous year. In Q3 2022 alone, the anti-phishing working group (APWG) identified more than 1.2 million phishing attacks. Signing your emails and documents is a simple way to avoid your employees and customers falling victim to a phishing attack.
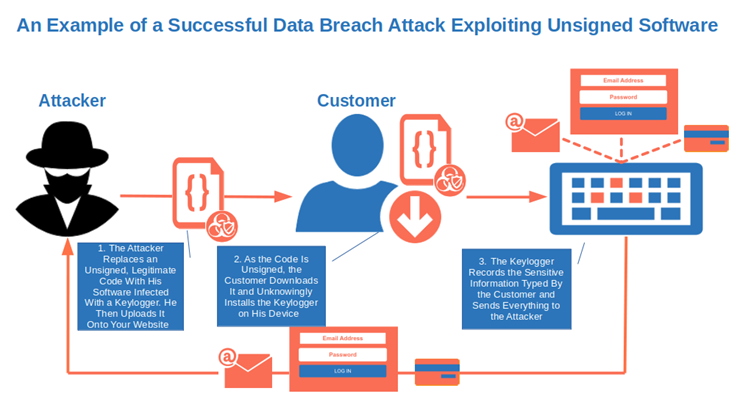
- Spot unauthorized modifications more quickly. Wondering how? Think back to when we talked about the digital signature process. The document that has to be signed is transformed into a unique hash value. Even the smallest change applied to the original document (e.g., adding a comma or replacing a character) will result in a totally different hash value. This means that if the document is signed and then modified by a malicious third party, once the recipient opens it, they’ll know something’s wrong as the hash value calculated by their system will be totally different from the document’s original hash.
- Increase the trust in your brand. DigiCert’s Digital Trust Report shows that 84% of consumers would take their money elsewhere if they lost trust in the organization they’re doing business with? Protect your data and show your customers you care about security with the help of digital signatures. They’ll trust you more and your business will benefit from it.
- Secure your communications and data transmissions. Yup! Some signing certificates like email and SSL/TLS include a security bonus: encryption. When applied, it ensures that your transmitted data are transformed into unreadable gibberish, making any attacker’s life much more difficult.
- Decrease cyber incident-related costs. Do you have an idea about how much a data loss due to a cyber incident could cost you on average? Dell did the math: more than $1 million in 2022! That’s enough to put many medium and small organizations out of business. Going digital will also help you save on paper, personnel, and storage. But that’s not all, as explained in the next point.
- Achieve compliance with standards and regulations will be easier. What happens when you are found not compliant with standards and regulations? You get fined. And when it happens, it can cost you more than an arm and a leg. To give you an idea, the European Union’s General Data Protection Regulation (GDPR) body issued 28 fines for a total amount of €395,718,240 in January 2023 alone. Many regulations require organizations to secure their communication and data transmissions. Hold on, this is something digital signatures can help you with, right?
So, now that you know what a digital signature is, how it works, and why it’s important, why don’t you start supercharging the security of your organization? Because until all of your code, emails, and files are digitally signed, nothing and nobody is safe. Not you, your customers, or your organization.
Final Thoughts on What Is a Digital Signature? A Look at Digital Signature in Cryptography
According to a report from Netskope, 44% of all malware downloads originated from the cloud in Q2 2022. In the same period, 92% of organizations surveyed by Cisco were using more than two public cloud providers.
Digital signatures are key to securing the information exchanged over the internet. From data to emails and software, digital signatures can effectively protect you as an individual and your organization from attackers and a lot of hassles.
Are you a developer? Next time you release a new code, don’t forget to add your digital signature to it to help:
- Increase downloads,
- Nurture trust,
- Improve your reputation, and
- Help you secure your software against modifications.
Are you a user? Make it a habit to check your emails, software, and the SSL/TLS certificates digital signatures of websites you visit to avoid becoming a victim of scams or malware.
And remember, no matter what you do, digital signatures are an excellent way to ensure the following about your software, scripts, emails, and files:
- Authenticity,
- Integrity, and
- Non-repudiation of data.
Want to know more about these three features? This is what we’re going to focus on in our next article. Don’t miss it!



