What Is Hashing Used For? A Look at the Purpose of Hashing
Do you think that the purpose of hashing is limited to password security? Think again — hashing is much more than that. Discover how, in a world where 82% of breaches involve human elements like errors and misuse, the power of hashing can boost your organization’s security posture in multiple ways
€600,000 (more than $637,000 in U.S. dollars). This is the price the major French energy provider Électricité de France (EDF) had to pay for failing to secure more than 25,800 customers’ passwords.
What happened? The company was fined in November 2022 by the French data protection regulation group Commission Nationale de l’Informatique et des Libertés (CNIL) for hashing 25,800 passwords using the insecure MD5 hashing algorithm. As if this wasn’t enough, the regulator found out that more than 24 million additional passwords were hashed without being salted!
When used properly, hashing (i.e., transforming any given data into a fixed-length hexadecimal string) is a fundamental tool that can help any organization secure sensitive data. But what is hashing used for in cybersecurity other than for protecting passwords? What is exactly the purpose of hashing?
Let’s find it out!
What Is Hashing Used For? A Quick Overview of the Purpose of Hashing
Everyone has a purpose in life. A teacher prepares his students for their future life and work, pets give us unconditioned love, and cybersecurity organizations help prevent data breaches and threats. But what’s the main purpose of hashing in cryptography? To help us verify the integrity of data or files. But that’s not all — hashing has several different (and useful) applications.
Ready to check them out in detail? If you’re too busy for an in-depth look but still want to answer the question “what is hashing used for?” be sure to check out our short answer summary table:
| Hashing Application | Examples |
|---|---|
| 1. Secure Password Storage | The password’s hash value is saved on databases instead of the plaintext password. |
| 2. Password Verification | To get access to a website or app, the hash of the password typed at the login is compared with the hash value of the password saved in the database. |
| 3. Data Integrity | Documents, files, and email hash values are compared to spot any change made to the original data. |
| 4. Website Security | Hashing is used to verify the authenticity of web certificates used to establish encrypted connections. |
| 5. Data Retrieval/Searches | Hashing helps you narrow down searches to quickly find data. |
| 6. Blockchain | Hashing is a fundamental part of any blockchain based secure transaction and it’s primarily used to generate public keys and block hashing. |
If you’ve got a bit of time to spare or simply want to learn more about the purpose of hashing, then keep reading.
1. Secure Password Storage
From June 2021 to June 2022, 45% of organizations interviewed by Thales suffered a data breach or didn’t pass an audit involving data/applications in the cloud. That’s 10% more than the previous 12 months. Saving only the hash of your passwords will ensure that, even in case of a data breach, it’ll be nearly impossible for the bad guys to determine the original input.
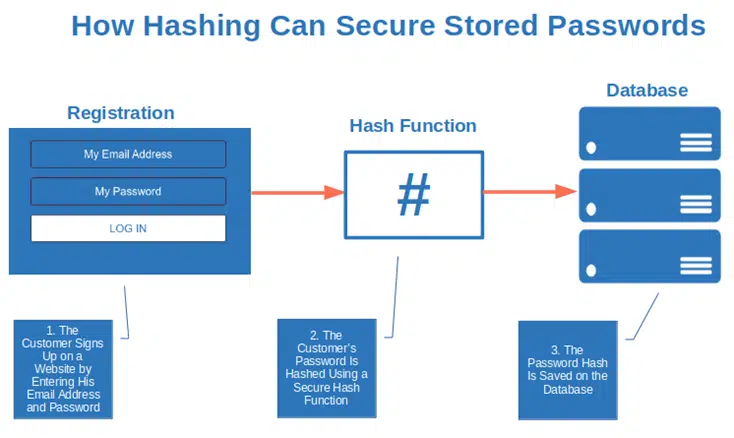
The graphic above is a basic overview that’s missing a key step: salting and/or peppering.
Let’s start with salting. A randomly generated string is added to the password before hashing. So, if your password is password123, once salted, it’ll become $4er5llpassword123. Why is it important? Check it out by yourself. Try to do a search in google for 482c811da5d5b4bc6d497ffa98491e38 (the MD5 hash of password123). You’ll be surprised to find out how many results will come up saying that the hash you looked for is equal to password123.
How could this happen? Thanks to rainbow tables: these are massive lists of password-hash combinations with their respective hashes available to cybercriminals and on the internet.
Now, try to do the same search for d2f33be9fcce1afd626c96ac91f5d5c5 (the MD5 hash of $4er5llpassword123. Nothing came up suggesting the salted password behind the hash? You’re safe from rainbow attacks!
Want to be even safer? Add some pepper, too. Another random string is added to your password before hashing that, instead of being stored with your password in the same database, it’s saved somewhere else. Why is it important? If the attacker manages to get access to your salted, hashed password, he still won’t be able to decipher it until he gets a hold of the pepper, too.
Learn about the advantages of salt and pepper in this short, four-minute video:
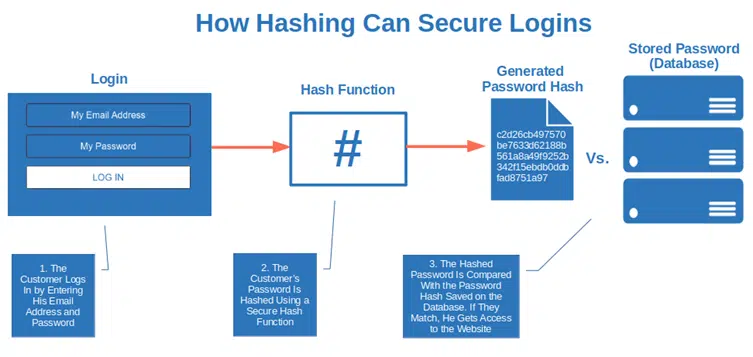
2. Password Verification
Did you know that the majority of websites don’t save your password in their databases? Yup! They usually save only the password hash (ideally, salted and/or peppered). This way, when you go to your online banking site and enter your username and password to authenticate, the hash of the password you typed is compared with the hash value of your password saved on the database.
If they match, you’re logged in. If not, the login is unsuccessful. Why bother with all this? It’s a much more secure process for password verification. No risk of sniffing during the login process! Did the bad guys manage to hack the database? Yup, and that’s the bad news. The good news is that they’ll get a bunch of gibberish hexadecimal characters — not your customers’ plaintext passwords.
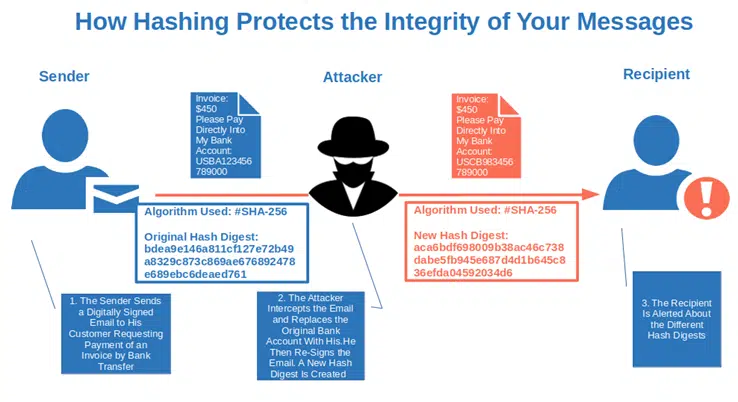
3. Data Integrity
Let’s say you write an email to your customer, providing them with your bank account details for payment of services or goods. You sign the message with your email signing certificate and send it. During the transmission, a cybercriminal intercepts your message (i.e., carries out a man-in-the-middle attack — more on that in a minute) and replaces your bank account details with his.
This video shows an example of man-in-the-middle attack:
Let’s go back to our story. Once the customer receives the email, its client uses your email signature’s hash value to re-generate the hash to compare the two values. Since the message text has been changed (i.e., the message’s integrity has been compromised), it alerts the customer. Once again, hashing comes to the rescue. And you know what’s best? It alerts you even if something very tiny, like an exclamation mark or a comma, has been changed! Isn’t that cool?
And it gets better. The same trick will help you protect from tampering, malware insertions, and other unauthorized changes to some of your other digital assets, including:
- Software, containers and codes (with the hash generated with your code signing certificate),
- Microsoft Office documents and PDF files (with your document signing digital certificate‘s hash).
Does it mean that hashing is like checksum? Not quite. Why are they different? Find it out in the table below.
| Hashing | Checksums |
|---|---|
| Used to identify other malicious changes (e.g., malware or malicious scripts. | Used to help you identify accidental changes to data/files (i.e., errors). |
| Larger in size. | Smaller sizes. |
| Can be used as a checksum, too. | Can’t be used as a hash value. |
4. Website Security
Do you want to ensure your customers’ sensitive data (like their payment information) are securely transmitted through your website? You’ll need a website certificate that’ll enable you to establish an encrypted connection (HTTPS). How can hashing help you?
When you use an SSL/TLS certificate, every time your web server receives a request from a client, the server certificate is sent to the user’s browser. An SSL/TLS certificate is generated using a hashing algorithm as part of the digital signature process. (Every SSL/TLS certificate is signed by the certificate authority that issues it.) The server sends this certificate to the connecting client to validate the server’s identity; this is done by the client checking the certificate’s hash digest information along with its public key.
Once the client authenticates the server’s legitimacy, the encrypted connection is established. Et voila’ — another purpose of hashing.
Want to know more about hashing contributes to protecting your data in transmission? Check out this brief video:
5. Data Retrieval/Searches
Struggling to find specific customer records in a huge database? Another purpose of hashing is to help you narrow down searches and quickly find data. Want an example? Imagine you have put all your customers’ records (i.e., full postal address, email address, payment details, telephone numbers, and more) into a table. Want to find a specific customer’s telephone number? As it is, it’ll be time- and labor-intensive task.
But, if you convert every input in the table into a unique integer using hashing, your search will be much faster. The same look-up process is used by software developers in programming languages when using hash tables-based data structures (e.g., libraries).
Learn more about how hash tables work in this detailed video:
By the way, did you know that hashing is also used for cached data (i.e., saved data that you use all the time)? It helps reduce the time needed to retrieve and access the saved information.
6. Blockchain
Interested in blockchain technology (shared digital databases used to record information where data are stored in blocks linked together through cryptography) or cryptocurrencies? Hashing is a fundamental part of any blockchain-based secure transaction, as they play a crucial role in generating and validating the integrity of chained data blocks. (Blockchain data blocks are sequential; data from one block is tied into the next block’s header data, which has data from the second block tied into the header data of the third block that follows… so on and so forth. This is done for data validation purposes using hashing to prove the legitimacy of each new block that gets added to the chain.)
In addition to Bitcoin and cryptocurrencies in general, some organizations like IBM use blockchain (and therefore hashing) to help companies in the food industry track the journey of food products. Healthcare providers use it to securely store patients’ records. And we could go on and on. But I guess you got the picture by now.
Did these examples answer the question “What is hashing used for?” I hope they did. And we’ve more in store for you. We’ll now unveil the reason why hashing is such an important pillar of every organization’s cybersecurity strategy.
Why Is Hashing Important in Cybersecurity?
According to research from Accenture, organizations leveraging data for their business decisions (i.e., data-driven organizations) can enjoy an average growth of 30% year on year. But what if the data you’re basing your strategic decision on have been manipulated? That could be the end of your business. We’ve just learned that hashing can help you prevent that by validating data integrity. But is this the only reason why hashing is so important for cybersecurity? Of course not. Hashing can protect our organization also from other threats:
The Outcome of a Successful Man-In-the-Middle (MITM) Attack
An attacker managed to get hold of your email during transmission despite encryption? Like Coldplay’s song says, “Everything’s Not Lost.” Hashing is your second line of defense. Even if your message has been intercepted and modified by a malicious third party, your recipient can still spot the manipulation by comparing hashes (as explained at the beginning of this article). They don’t match? That’s a big red alert!
Malware
Let’s go back to the hijacked email we talked about in the previous point. The attacker didn’t only modify the email message itself. It also added an infected attachment — ransomware, for example — that, once downloaded, would infect your device and lock you out from all your files and documents. Thanks to hashing, though, you’ve still been warned that something wasn’t right. Thus, you didn’t open the infected attachment and dodged a bullet… a really big bullet, when you consider that IBM reported the average cost of a ransomware attack reached $4.54 million in 2021.
Unauthorized Change of Data
Have you ever heard of the CIA triad? It’s a model for those organizations who want successfully implement information security policies. It’s based on three main principles:
- Confidentiality,
- Integrity, and
- Availability.
Yup! Data integrity is one of them. Its goal? Ensure that the data hasn’t been modified, tampered with, or corrupted. How? Through hashing. Why is it important? Let me give you an example.
In 2021, a hacker managed to access a Florida water treatment plant’s control systems. Once in, he modified the level of sodium hydroxide in the water to a hundred times higher than the recommended level. Luckily for the people living in the area, the change was immediately spotted by a plant operator. But what if he didn’t catch it in time? It could have been a disaster as sodium hydroxide poisoning can be very dangerous for anybody’s health.
Curious about the CIA triad? Check out professor Messer’s four-minute video:
By the way, your organization handles customers’ payment data? Did you know that protecting their integrity with hashing will also help you be compliant with regulations like the Payment Card Industry Data Security Standard (PCI DSS)? They’ve just released a new version in March 2022 and file integrity protection is part of the requirements.
Password Stealing
In 2021, the volume of password attacks estimated by Microsoft increased by 74%, topping 920 attacks every second. At the beginning of this article, we’ve already learned how hashing can protect you from password stealing by storing only the hash of your passwords.
Let’s take this one step further. How? Adding some salt (i.e., a random string of characters appended to the end of a password that gets stored with the data) and a bit of pepper (another random string of characters added to the password but gets stored elsewhere) before the password is hashed. Try to find out the password behind the hash now, cybercriminal!
We’ve now reached the end of our journey. Now it shouldn’t be a problem for you to give an answer to the question “What is hashing used for?” Before you go, though, why don’t you have some fun and test how much you know about hashing now? Take the quiz!
Final Thoughts on What Is Hashing Used For? A Look at the Purpose of Hashing
Hashing algorithms have become an integral part of our digital world, helping to protect the integrity of our data. But as we’ve just learned, the purpose of hashing doesn’t stop there. Just a few of the uses of hashing include:
- Indexing,
- Data modification detection, and
- Malware protection
Beware, though! As EDF learned (at enormous expense), incorrect use of hashing can put you in serious trouble. This is why you need to ensure you always use the most secure hashing algorithms and, when needed, “flavor” your hashes with some salt and pepper (for password security). Now, you’re ready to start hashing!



