Best Practices of Code Signing Time Stamping: What Is It? Why It Matters?
Time Stamping Your Code – An Important Detail in the Software Signing Process
If you’re a software publisher or a developer, then you know that the success of your software often depends upon the number of downloads, which depends in part on how much trust users have in it. So, to assure users and avoid unnecessary warning messages upon download or installation, you‘ve taken proactive steps like signing your code using a trusted code signing certificate.
When you sign your code, if you’re not using the time stamping option, you could run into some big problems a few months or years down the road.
Simply put, time stamping is an optional part of the signing process, which allows users and software to recognize whether an applied code signing signature is valid–even after a code signing certificate expires.
Why Time Stamping Is Important: A Real-Life Example
Let’s look at a real-life situation to understand the importance of a code signing time stamp. Let’s say you sign and publish your software. All is well until your code signing certificate expires a year later. Now your installer is showing warnings about an untrusted signature. Sure, you can resign and republish the installer package, but you won’t be able to update the installers that are already out there in cyberspace.
Or let’s take another example, where you’re using code signing to verify software updates. What happens if you push updates, but a client doesn’t install them until after the certificate expires. Will your software stop running abruptly due to the expiration of the code signing certificate? Think about how much impact it’ll have on your software users and how you’ll be able to provide immediate help for it. Will it be possible for you to update your software, or will the updates be broken due to an expired signature? Also, what will be the cost of developing and deploying this emergency patch? How much will your user’s business suffer if the software doesn’t work?
You might be thinking: those are all issues caused by the code signing certificate expiry. Yes, and time stamping is the solution for such scenarios.
Time stamping also offers another benefit: if you have to revoke your code signing certificate due to a situation like loss of the private key, then this time stamp will save you by keeping all your signed executable files and software packages functioning as long as they were signed before the date of revocation. However, any new signature done after the certificate was revoked will be considered invalid.
Let’s cover the background of time stamping in the code-signing process and also understand some best practices that should be followed for ensuring that you don’t run into any problems due to software signature.

Budget-Oriented Comodo Code Signing Certificate to Sign your Software/App Codes.
What’s Time Stamping?
Time Stamping is a feature that preserves the signature you apply to a software package. It allows your software (signature) to be accepted by the operating system and other client software even after your code signing certificate expires.
Whenever the signed software is executed, its signature is verified, for example by the user’s operating system. If you’ve time stamped your software, the users’ computer will verify the signature based on the time it was signed, rather than the current time when the software is executed.
Of course, if the software isn’t time stamped its signature is assessed based on the current time. You might have distributed your signed software months or years ago, and in that case, the code signing certificate used for signing that software package may have expired, and the signature might no longer be considered valid. For example, a code signing certificate you used for signing had a validity period of the entirety of 2019 (1/1/2019 to 12/31/2019), and you signed and time stamped your software in November 2019. Now, a user downloads your signed software package and tries running it today – if it wasn’t time stamped, the user will get an error. In this scenario, the OS will use the time stamp to evaluate whether a code signing certificate was valid at the time of signing instead of today’s date while accepting the signature.
Last but not least, the time stamp is signed and protected by the CAs, which stops tampering or any other malicious activity while keeping it cryptographically secure.
A Brief Look at the Technology Used in Code Signing Time Stamping
A time stamp is provided by a certified Time Stamp Authority (TSA), which uses a series of encryption and decryption techniques based on PKI (Public Key Infrastructure) technology to apply verifiable time stamps. In code signing, time stamping is used while signing the program to verify the date and time it was signed. Time stamping is done with a time stamping server via a URL. CAs like Sectigo and DigiCert run their own time stamping server their customers can use.
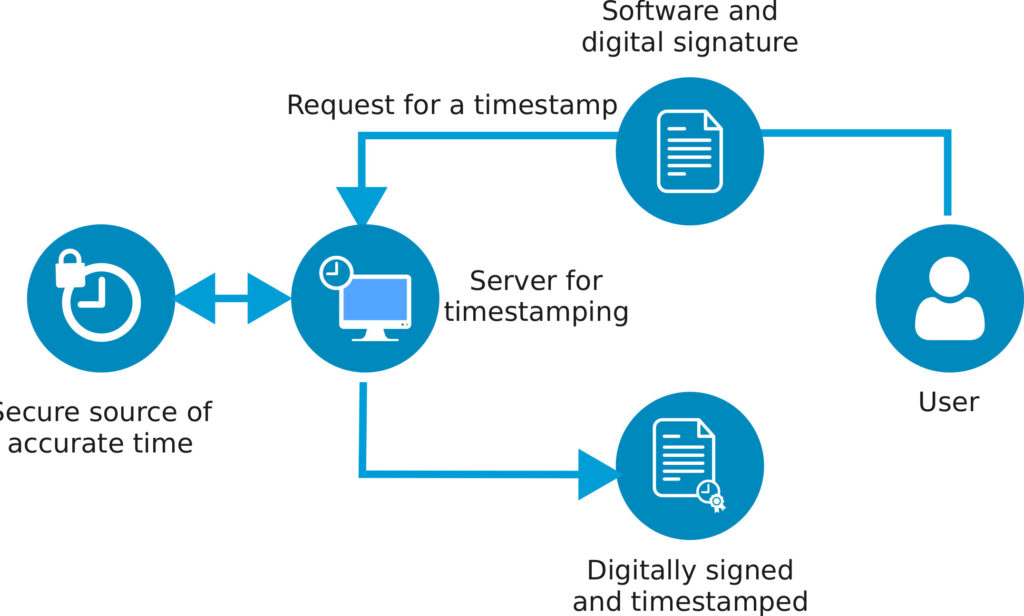
What’s Time Stamping Server?
When you sign and time stamp your software package, its hash is uploaded to the time stamp server. Next, the time stamp server does it’s part:
- Certifies that the software certificate is valid at the time of signing.
- Records the date and time the signature was applied.
- Signs the information using its own private key.
- Returns a timestamp (with digital signature) to attach to the file.
The client can now use the time stamp server’s signature to verify and trust the time stamp information.
Protocols of Time Stamping
Usually, two protocols are used for time stamping:
- RFC 3161
- Microsoft Authenticode.
Recently RFC-3161 was updated as RFC5035, which also allows using ESSCertIDv2. Authenticode is used for signing manifold formats like .ocx, .exe, .cab, and .dll.
Best Practices: Code Sign Time Stamping
- Turn on time stamping in your signing tool. Many code signing tools are available (for example, Microsoft Sign Tool) and time stamping is an optional setting. So make sure that you know how time stamping works with the development tools you use.
- Add timestamping to your standard process. Make time stamping a required part of your code signing process, because it’ll prove beneficial later on. For instance, it’ll help you avoid unexpected issues and errors with installing different versions of your software.
- Document your time stamp process. Time stamping needs additional commands and flags when you’re signing a file, along with a URL for retrieving the time stamp signature from your CA. And these steps will vary slightly depending on what tool you’re using. So, it’s best to document the entire process, which can make the time stamping process easier, especially for team members who are new or doing it for the first time.
- Remember, you can revoke your certificate if needed. Time stamping lets an operating system verify if a signed executable was issued before or after the revocation of a code signing certificate. So, if you’ve time stamped your software package and you have to revoke a certificate, you’ll be able to do so without the signature being invalidated. Because the time stamp will verify against the revocation date and if the file is signed and time stamped before the revocation of a code signing certificate it’ll be counted as valid.
| Certificates | Lowest Price | |
|---|---|---|
| Comodo Code Signing Certificate | $211.46/yr | More Info |
| Sectigo Code Signing Certificate | $211.46/yr | More Info |
| Comodo EV Code Signing Certificate | $277.71/yr | More Info |
Closing Thoughts
So, now you know: time stamping may be an optional step, but it’s really important.
In a nutshell, time stamps give surety that signatures will remain secure, trusted, and valid, even if a code signing certificate loses its validity or, at worse, gets revoked.


