What Is Code Signing? An In-Depth Look at This Secure Coding Process
Discover what code signing is, how it works, why it’s important for businesses and users alike, and why you should use it as a software developer or publisher to protect your brand
Trust, authenticity, integrity are three important concepts in a digital world where people download software and apps nearly every day. From installing software updates to existing programs to downloading new tools needed to complete specific tasks, downloading software and updates has become more commonplace within organizations and for individuals on personal devices.
However, as a user, how can you be sure of the authenticity and integrity of the software or app you are planning to install? As a publisher or developer, how can you prove to your users that your software is legitimate and that your code can be trusted? What kind of technology can enable trust through authenticity and integrity, and at the same time, increase security? This is where code signing makes all the difference.
But what is code signing? In this article, we will answer these questions and explore in detail how a code signing certificate can help users, developers, and businesses be more secure in a connected world. We will learn what code signing is, how it benefits you as a user or developer/publisher, and how code signing works.
What Is Code Signing? It’s Like Tamper-Proof Packaging for Software and Executables
When you buy a new smartphone, the device usually comes in a branded box sealed with one or more security stickers that cannot be altered as a guarantee of authenticity and integrity. This tamper-proof packaging is a way for customers to know that the product is new, authentic, and has never been opened or otherwise messed with.
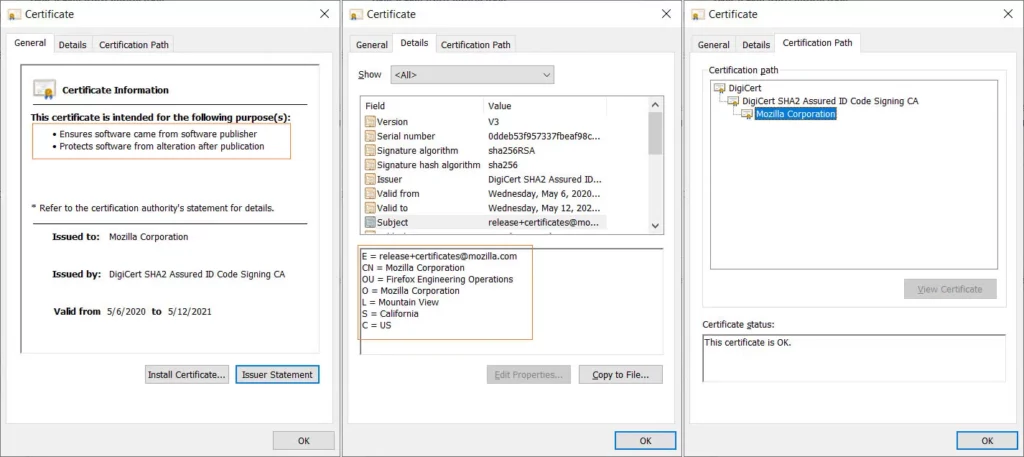
In this way, a code signing certificate is very similar. A code signing certificate is a small digital certificate file that developers and software publishers use to digitally sign their software, code, and other executable files. By digitally signing a code or an app with a private key, it certifies that:
- The software or app available to download is authentic,
- It comes from a trusted vendor and has not been tampered with (i.e., users will know that the product is safe to use and download).
According to the National Institute of Standards and Technology (NIST) Security Considerations for Code Signing whitepaper:
“A wide range of software products (also known as code)—including firmware, operating systems, mobile applications, and application container images—must be distributed and updated in a secure and automatic way to prevent forgery and tampering. Digitally signing code provides both data integrity to prove that the code was not modified, and source authentication to identify who signed the code.”
Both the physical security seals you find on the tamper-proof packaging of smartphones and the code signing have the same goals: to increase trust and guarantee the integrity and authenticity of your products.
Code Signing Certificate Types, Features, And Differences
Code signing certificates are typically issued by publicly trusted certification authorities (aka certificate authorities or CAs). Prior to issuing a certificate, the CA will always do a background check on the company or individual requesting it. The vetting process varies depending on the type of certificate (more on that momentarily).
Of course, you can also create self-signed code signing certificates, but those certificates should only be used within your dev and testing environments and should never be used to digitally sign code that is intended for external purposes (such as being used or shared on a public network).
There are two different types of publicly trusted code signing certificates (i.e., certificates issued by a public CA):
Let’s have a look at their different features and benefits:
| Standard Code Signing Certificate | Extended Validation (EV) Code Signing Certificate | |
|---|---|---|
| CA Validation Process for Certificate Issuance | This process involves a basic background check. | This process involves a rigorous background check following CA and Microsoft guidelines. |
| Where the Private Key Is Stored | Locally, in the developer’s workstation. | Externally, using a hardware token. This adds another layer of security preventing illicit use. |
| Message Visualized During the Download | A pop-up message will show the publisher’s organization details instead of an “Unknown Publisher” warning. | No warning message will be shown as the software publisher will be known and immediately trusted by all major operating systems and browsers. |
| Benefits of Using a Code Signing Certificate |
|
|
Time Stamping
There’s one tool that’s crucial to protecting your software in the long run — what is this code signing tool? Time stamping. Time stamping is an additional feature of code signing certificates. While it’s technically an optional step in the code signing process, it’s an interesting process that serves a crucial purpose in code signing.
Code signing certificates expire after a period of one to three years (depending on the length of validity you chose when you bought them). Once the certificates expire, you can’t sign your codes anymore, and all the signatures on the executables you’ve already signed lose their validity.
What this means is that all the codes and apps you published years or months ago and that are still available on the internet for download will have an expired certificate, so their signatures will be invalid. So, when a user goes to your website and from one day to the next, the same app or code that’s trusted is suddenly considered unsecure because it has an expired certificate. Needless to say, hosting software that’s signed by an expired certificate can tank your reputation level quickly!
This is where time stamping becomes a very useful feature because it alleviates this expired certificate invalidation issue altogether. A timestamp adds to your signature the precise date and time when the code was digitally signed. This process allows browsers and operating systems to compare the signature date with the validity period of your code signing certificate. If the signature’s timestamp info falls within the certificate’s validity period, then your signature remains valid for years to come, and the users won’t notice any difference! Isn’t it cool?
If you want to know more about time stamping, check out our article on code signing time stamping.
In any case, we will talk more about the benefits of code signing later on in this article. Let’s now move on and see what can be digitally signed with a code signing certificate.
How You Can Use Code Signing Certificates Within Your Organization
Code signing is becoming more and more popular. A report from Mordor Intelligence on the Certificate Authority marketshare, shows that the demand for digital certificates (a category that includes code signing certificates) will grow at a compound annual growth rate (CAGR) of 12.7% over the next five years.

Once you’re the proud owner of a code signing certificate, you can sign many types of scripts and executables (i.e., .exe, .dll, .jar, .msi, .RPM…) regardless of the type of platform you’re using. Here are a few examples:
- Microsoft Windows: From Microsoft Office to Visual Basic applications and macros, from software to drivers updates and patches, the code signing certificate can be used to sign a high number of Microsoft applications.
- Mac OS (OS X): Developers of software, tools, and apps for Mac OS, can and should also use a code signing certificate to certify their codes.
- Microsoft Visual Studio: If you’re developing software in Visual Studio, you can (and should) sign it with a code signing certificate to avoid warning messages shown by the major browsers and operating systems. Check out this article to learn more about code signing certificates for Visual Studio.
- Java Applets: Java code applets (.jar files) can be digitally signed using the JarSigner tool included with the Java Development Kit (JDK).
- Adobe: Did you know that Adobe Air files don’t work if they’re not signed? If you’re planning to publish a code to use with an Adobe Air application, make sure you sign it!
- Mobile apps: Are you working on a new iOS, Android, Google or Amazon app? In this case, you’ll need to use specific code signing certificates issued directly by each store. Nowadays, all the most known and trusted app stores like Google Play Store, iOS AppStore, Amazon AppStore, Samsung Galaxy Apps, just to name some, accept for distribution on their websites only apps that are properly signed with their code signing certificates!
- IT companies: Code signing certificates keep all your internal apps and scripts used in your company safe from internal and external unauthorized modifications. This protects your users and your business from the risk of installing corrupted or infected software that may cause breaches or malware infection by giving them a way to verify the integrity and authenticity of your files.
- IoT: When companies have many devices that are connected 24/7, integrity and trust are paramount. Think about software updates for example: how can you ensure that the new versions of your software won’t be tampered with after release? Code signing will ensure trust and reliability throughout all products’ lifecycles!
We could go on and on, but we’re running out of time. In any case, what is important to remember is this: If you’re developing an executable file, you should use a code signing certificate to sign it. If you’re a user, you should only trust signed executable files. Why? The next two chapters will answer this question.
What Are the Benefits of Code Signing?
Based on the data from the McKinsey & Company survey of North American consumers on data privacy and protection, when asked about their level of trust by practices,
- 43% of customers are more likely to trust businesses that have a trustworthy brand.
- 32% would trust businesses that are considered trustworthy by friends and family.
- 31% of consumers trust those companies sharing their approach to protecting data.

Increased trust is only one of the many benefits that both users and businesses can enjoy when an executable is signed:
- Validated code integrity: When a code is digitally signed, the users will get a warning message if the software has been modified, corrupted, or altered after it has been signed. This helps the publisher reduce the risk of tampering. Can you imagine what could happen if a tampered software update is installed on platforms managing power grids or medical devices that keep patients alive? It could be disastrous!
- Guaranteed authenticity: The user will immediately know that the code or app he’s downloading is really coming from you as your identity is linked to the public and private keys used to sign it. As an author and business owner, you will be able to protect your intellectual property and show the users that you care about them.
- Enhanced reputation: A digital certificate will show your customers that your code/app is safe to download, elevating your reputation in the industry. As a user, a business signing its codes and apps looks much more credible and reliable.
- Revenue increase: More and more app stores and software platforms are accepting only code signed software or apps. In fact, Windows Defender Application Control (WDAC) is a tool that enables organizations to create WDAC policies that restrict the types of software and code that can execute. For example, you could set restrictions that ensure only digitally signed software and operating systems can run. Releasing only digitally signed software and updates can help small businesses and developers to gain customer trust, which can help boost their download numbers and increase revenue.
- Multi-platforms integration: As previously highlighted, code signing is now available on many platforms like Windows, Apple iOS, Linux, Java, Android, Adobe Air… even browsers nowadays require code signing (i.e., Firefox add-ons). Trying to download or install unsigned software will trigger automatic security warnings in users’ browsers and operating systems.
- Higher trust reducing security warnings: Code signing enables a smooth and safer customer experience, reducing the number of security warnings, easily identifying the author of the software, confirming the authenticity and integrity of the code. All this contributes greatly to building mutual trust between the customers and the vendors.
Code Signing in Action: How It Looks When Someone Downloads Signed Software
Let’s imagine for a moment that you’re a user who is looking to install a new data modeling tool to help you create the structure of a database. You’ve searched the web, selected a few potential candidates, and now you’ve narrowed down your list to three data modeling tools available to download on three different platforms. They’re all compatible with your operating system and offer interesting features. Two are free to download, the third one is advertised as a paid tool, but you can test it for free for thirty days, so you decide to test all of them.
When you click on the first downloaded executable, this is what you visualize:

It looks like that, in this case, the publisher has code signed the software using a standard code signing certificate. This is already good news as you know exactly who produced the executable.
When you click on the second .exe a different pop-up message comes up:

Here, the software developer or publisher didn’t code signed their software at all. Would you trust and install something when you have no proof of the identity of the author and you have no way to check whether the file has been altered? Probably not — nor should you!
When you click on the third one, there’s no warning that pops up — nothing worrisome! Your operating system simply starts installing the tool. Based on what we learned so far, this is even better. It means that your operating system has immediately trusted the software. Why? Because the publisher signed the executable with an extended validation signing certificate.
Amazing right? Now that we know more about code signing certificates, let’s explore how they work.
How Code Signing Works: A Look at the Process From Certificate Purchasing to Signing
The procedure of buying and using a code signing certificate is very straightforward. You just have to follow this quick step-by-step guide:
1. Select the type of code signing certificate: Do you prefer the standard or the extended validation code signing certificate? This is up to you to choose, depending on your needs. However, if you’re looking for enhanced security features that will improve your customers’ experiences and increase their trust in your brand, it’s best to go for the extended validation certificate.
2. Purchase the certificate: Once you know which type of code signing certificate you want to buy, choose a CA, go to its website, pick the certificate, select for how long it should be valid, and finalize your purchase.
3. Identity verification: As you already know, the CA will have to run some background checks before releasing the certificate. The validation process may last between three and five days, depending on the type of certificate requested.
4. Install your code signing certificate: Once you have received the certificate, you can proceed with its installation. The process may differ from platform to platform, but it’s a quick and easy process.
5. Start signing your applications: Now, you can finally add your digital signature to your code or executable! Once again, every platform follows its process, but you just need to follow the related instructions.

6. Publish your application: After you’ve digitally signed your code, you can publish it on the platforms of your choice or send it to the users for download! It’s done!
After you’ve completed all these steps, your software or script users have a way to verify the integrity and authenticity of your software. Whenever they download your signed executable or application, their operating systems will use the public key on the back end to decrypt your code’s signature to verify your identity and check the integrity and authenticity of the code. Should the code, hash value, or signature not match, the users will be notified.

Are you a developer and want to learn more about the architecture of a code signing and more about how code signing works? Check out this article.
Final Thoughts Relating to the Question “What Is Code Signing?”
In summary, trust has always been fundamental to all business and personal relationships’ success. It’s even more important now when basically everything and everyone are connected 24/7. Code signing is essential to trust for software, scripts, and other executables.
Signing your codes and executables is one of the most effective and efficient ways to:
- Validate your organizational identity,
- Minimize software security risks by enabling users to determine if your product has been altered,
- Improve user experience by building long term digital trust, and
- Strengthen your brand name and relationship with your customers.
I hope this article provided you with the information you needed to understand what code signing is and why it’s so important for everyone concerned with security in today’s digital environment.
So, what are you waiting for? Now that you know how code signing works: develop it, sign it, seal it and then, only then, deliver it!


