What Are Three Uses for Digital Signatures?
Authentication, integrity, non-repudiation. Three magic words that could help your organization save an average of $18,000 in case of a cyberattack. Learn everything about three digital signature uses and find out how, together, they can boost the security of your digital assets
From October 2021 to September 2022, Zscaler analyzed billions of encrypted traffic threats. The outcome? 89.9% of those threats were involving malware. Yup! Nowadays, encryption alone isn’t enough to protect your data in transit.
In our previous article, you’ve learned what digital signatures are, how they work, and how they can help verify the authenticity of a product and its creator. Today, we’ll dig deeper into the three digital signature uses that can:
- Shield your organization, customer, and other users from menacing malware and dangerous data breaches,
- Help your organization achieve a successful digital transformation,
- Increase trust in your brand and improve your reputation as a result.
How? Keep on reading to find it out!
Digital Signatures: A Definition
Did you know that the world’s oldest signature was found on a Sumerian clay tablet dating back to 3100 BC? A scribe, Gar Ama, signed his list of 41 common professions in Sumeria (modern day Iran).
Fast forward thousands of years, and we find digital signatures replacing handwritten ones on several occasions, taking the whole signature concept to the next level. But what is a digital signature, exactly? It’s a digital identifier that uses the power of cryptography (i.e., hashing algorithms and keys) to prove that a digital asset (e.g., file, email message, or software) is legitimate and hasn’t been modified after it was signed.
In the digital, interconnected world, a digital signature is used to:
- Help organizations and users to prove that they’re really who they say they are (i.e., authentication).
- Guarantee that the information exchanged between the parties hasn’t been modified (i.e., integrity).
- Ensure that the person who signed the asset can’t deny that he has signed it (i.e., non-repudiation).
Got it? OK. We’re not going to go into the technical details of how a digital signature works, as we’ve already covered this in our previous article (linked above, in our introduction). However, if you have a few spare minutes, you may want to satisfy your curiosity by checking out this excellent Computerphile explainer video featuring Dr. Mike, where the whole digital signature process is explained in simple words:
Examples of How You Can Use Digital Signatures Within Your Organization
There are several public key infrastructure (PKI) based digital signatures you can implement within your company or organization that have different uses:
- Code signing certificates — You can use these small data files to digitally sign your code, containers, and other executables.
- Email signing certificates — You can use these digital certificates to digitally sign outbound emails. They’re also known as S/MIME certificates. S/MIME, which stands for secure/multipurpose internet mail extensions, is a secure protocol for sending and receiving digitally signed and encrypted emails.
- SSL/TLS certificates — You can use these website security certificates to secure data transmitted via website sessions.
- Document signing certificates — You can use these digital certificates to attach your digital identity to Microsoft Office documents and Adobe PDF files (in the case of some document signing certificates).
Now, time to get down to business and explore the three digital signature uses we’ve just mentioned.
What Are the Three Uses for Digital Signatures?
Every time my cats see me with something different, like a new hat or gloves, they stop and check the unknown object from afar before coming over to me as usual. While they know me well and trust me, they still prefer to verify that it’s really me under that hat before doing anything.
The same verify “before you act” concept can be applied to the digital world. How? Let’s imagine for a moment that you work in the accounting department of a big organization and you’ve just received an email from your boss. The message urges you to quickly pay a vendor’s invoice by transferring $5,000 to a certain bank account.
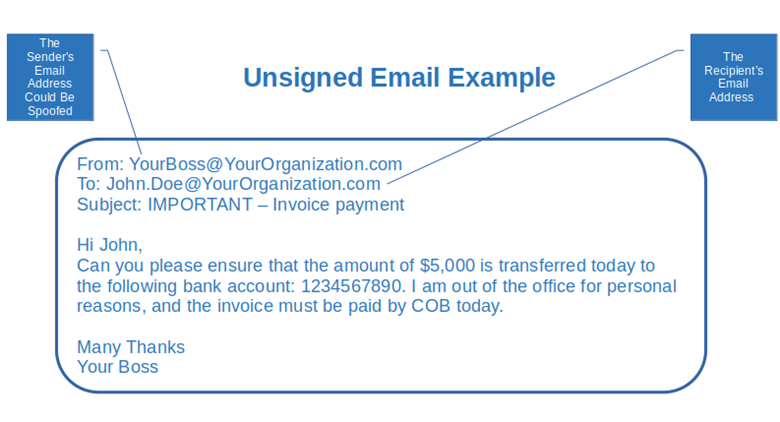
Now, how can you (John) be sure that the email you’ve just received from your boss is really coming from him, isn’t an impersonator, and hasn’t been modified during transmission? You can (and should) call him on his official work phone or, if you’re in the office, walk down the hall to go check with him directly. But what about having a way to digitally verify that the email is authentic and really came from him?
Authentication, integrity, and non-repudiation are three characteristics of digital signatures that can help you do precisely that. Let’s explore them one by one and find out how they can help you.
1. Authentication
Let’s go back to the email example above. The “From” field indicates that the email was sent from “[email protected]”, or so it seems. Have you ever heard about email spoofing?
With this technique, attackers can use scripts (command line or PHP, for example), or online tools to configure the sender address to whatever email address they want. Then they just need to add a credible text and/or a malicious link, et voila’, a perfectly credible phishing email is ready to be sent to their victims.
How dangerous is it? According to Acronis, 76% of all email-based attacks analyzed between July and November 2022 were phishing messages. Want another example? Check these two email addresses:
[email protected] and [email protected].
Did you notice the difference? The first one (the real Amazon email address) says “auto-confirm”. The second one, (that I’ve made up just now) says “auto-confirmed.” It also has a slightly different domain name — amaz0n.com instead of amazon.com. The question is: would you have checked the email address and, thus, spotted the difference when you received the order confirmation email? Unfortunately, not enough people check, and many realize too late the huge difference that those three characters can have when it comes to email security.
So, how can authentication, one of the three digital signature uses, enable you to verify if somebody is really who they say they are?
In our previous article, we’ve learned that when you digitally sign a message, the recipient will see a verification logo (e.g., a tiny red ribbon in the case of Outlook) and the signatory’s email address following the sentence: “Signed by” and the verified email address it came from.
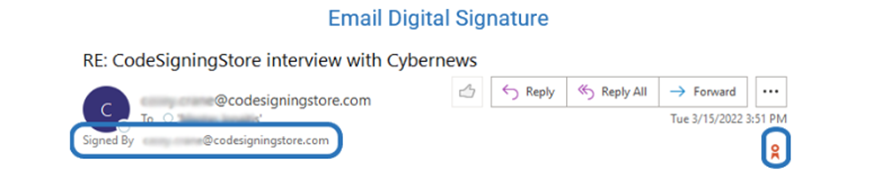
These two signals will confirm to the recipient that the email has really been sent by the person indicated in the From field. Why? Because to digitally sign his email, the sender had to:
- Use an email signing certificate that was issued by a trusted certificate authority. This is important because the sender only could have received the certificate from the CA after undergoing a thorough, rigorous vetting process.
- Use their private key (more on that later) that’s linked to the certificate and the email address they control that’s associated with it to sign the message.

OK, so now you’re certain that the email has really been sent by your boss. This is what authentication does. But how do you know that the text hasn’t been modified? This is where verifying data integrity, the second digital signature usage, comes into play.
2. Integrity
The last time I went to buy a new headset, I noticed that the last box left of the model I wanted was open. I checked inside and noticed that the USB adapter was missing. Of course, I didn’t buy it and went to another shop.
This was easy. It was something tangible — I knew how it was supposed to look and what it was supposed to contain when unopened. But how can you spot a modification in case of something intangible like an email, if you don’t know what it looked like originally? For example, how do you know that the bank account indicated in the email you’ve just received from the vendor you’ve bought something from, hasn’t been replaced with another one by a malicious third party? Once again, the digital signature comes to your rescue by providing a way to verify data integrity.
Let’s go back once again to our email example. In the text, your boss asked you to transfer $5,000 to the bank account indicated in the email. But could you really swear that the body of the message wasn’t changed during transmission? What if somebody intercepted the email (i.e., a man-in-the-middle attack) and replaced the original bank account with his own? It could cost you dearly.
2022 was full of examples that demonstrate the consequences of maliciously modified messages:
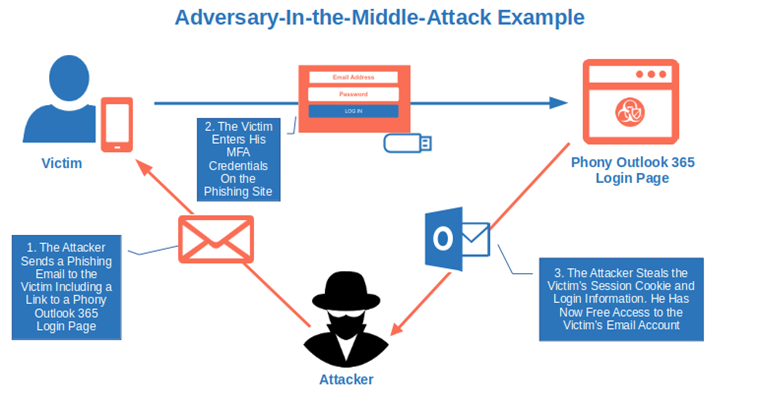
- In July 2022, Microsoft announced they identified a large-scale, sophisticated phishing campaign targeting more than 10,000 organizations using Office 365. The cybercriminals were using an adversary-in-the-middle attack to steal credentials and multi-factor authentication (MFA) information. Once done, they accessed the victims’ finance-related emails and tried to get them to unknowingly transfer money to their bank accounts under the guise of invoice payments.
- Hornetsecurity’s latest report, based on the analysis of more than 25 billion emails, shows that 39.6% of the email attacks identified in 2022 were phishing, making it the number one attacking technique in the analyzed period.
Scary huh?
How an Email Client Signs an Email
The first thing the sender’s email program does to sign an email is generate the message’s hash value using a hashing algorithm (i.e., a cryptographic function). It’s kind of like a fingerprint of the document that’ll uniquely identify it.
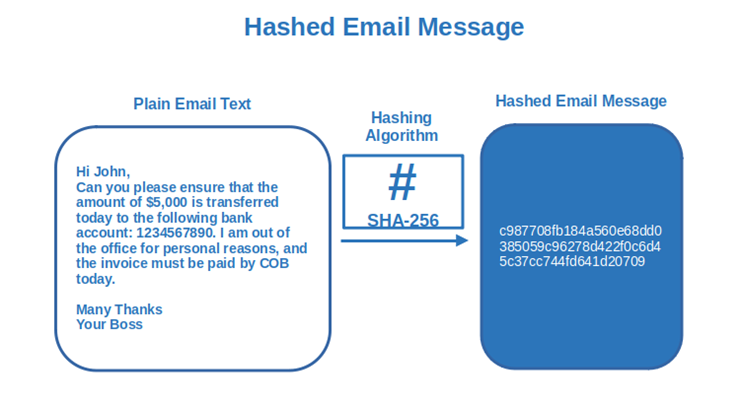
The file hash is added to the message. Once the receiver opens it, its email program will generate a new hash value of the message and compare it with the original hash value. If they match, it means that the email’s body hasn’t been changed and its integrity is in check. Your boss really did ask you to transfer $5,000 to that very bank account.
But what would happen if an attacker replaced your company’s legitimate bank account information with info for an account they control? The hash value calculated by the recipient’s email program would be totally different from the original one, even if the attacker had only changed just one number in the whole bank account. Here’s a quick visual example to demonstrate what we mean:
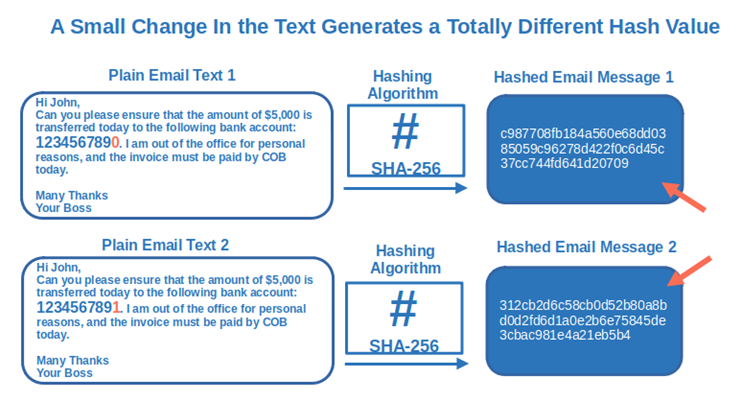
The email client will alert you that something is wrong. As a result, this security mechanism will probably save your neck (i.e., prevent you from getting fired because you transferred your organization’s $5,000 to a hacker’s account).
3. Non-Repudiation
Let’s say that you’re 100% positive that the email you received from your boss came really from him. You, therefore, proceed with transferring $5,000 to the bank account indicated in the email. But what you don’t realize is that your boss is an unscrupulous individual who is trying to steal money from the company using an account he controls. (Not saying this is the case with your real boss — we’re just using this as a hypothetical example here!)
A few days later, you’re summoned by your chief financial officer (CFO) and human resources (HR). They want to know your version of the story, as they discovered that the $5,000 have been transferred to a fraudulent bank account. And what makes things look even worse for you is that your boss denies having sent you that email!
If the email wasn’t digitally signed, it would have been your word against your boss’s. Even worse, you wouldn’t have had any way to prove he was lying through his teeth. Thus, you probably would have ended up paying the consequences.
But what if your boss had indeed digitally signed the message? In that case, you’d have pretty strong proof that he sent the email. And, as a digital signature is legally binding (remember, your digital signature is linked to a digital certificate issued to a specific individual or organization by a trusted certificate authority), the proof could have been used in a court of law, too. Yup! It would have saved your bacon. Why?
Because non-repudiation enables you to prove that something did happen, no matter what anybody else says. Even your boss.
The 3 Basic Requirements of Non-Repudiation
OK, let’s explore another possibility. In our example, it could have also occurred that an attacker managed to steal your boss’s key pair and send the infamous signed email. But, if this was the case, he would have immediately informed IT security to get his key pair revoked to prevent them from being used again, right?
This takes us to the four basic requirements to fulfill to achieve non-repudiation. Such as:
- Safe key storage. Did you know that 50% of organizations interviewed by Keyfactor in 2021 don’t have access control process in place for managing code signing keys? Non-repudiation requires that the key pair is stored somewhere safe, tamper- and copy-resistant, and that only the owner can access it. An example? USB tokens or smart cards.
- Identity proofing. In the physical world, you need to use your passport or ID to confirm that you’re really who you say you are when you have to sign a legal document in front of witnesses. The same happens in the digital world. In this case, upon issuing your key pair and digital certificate, your organization’s identity is verified by a third-party authority.
- Revocation process. Last but not least, there must be a key management process in place that also describes how you can revoke your keys (and/or digital certificate) in case they’re stolen. This way, if a message is sent using those stolen keys, the recipient will be alerted when their email client tries to verify the message’s digital signature.
- A public key infrastructure (PKI). This process enables the sender to sign the message using his private key, and the recipient to verify the signature using the sender’s public key.
Got it? Now the signed email message, code, or document is pretty bulletproof. All this is thanks to the three uses for digital signatures: authentication, integrity, and non-repudiation.
Why Authentication, Integrity, and Non-Repudiation Are Key to Your Digital Transformation
“It’s a matter of trust
It’s always been a matter of trust
It’s a matter of trust
‘Cause it’s always been a matter of trust”
These are words to stand by from singer/songwriter Billy Joel in 1986. And he was right. It’s always a matter of trust — both in the physical and digital worlds.
According to the Boston Consulting Group, 60% of the companies interviewed at the end of 2022 said they’ll increase their investments in digital transformation in 2023. To put it simply, they’re planning to shell out some cash to integrate digital technologies into all areas of their organizations. Why? To deliver more value to their customers, thus increasing sales and customer satisfaction.
This is great on the surface. You can have the best office locations, use the latest technologies and have the fanciest tools, but without your customers’ digital trust, you won’t go anywhere. And it doesn’t matter how much effort and money you put into it. Your digital transformation won’t bring you the results you were expecting.
But what does digital trust mean then? And why is it linked to the three uses for digital signatures?
Digital trust is made of all these elements that contribute to winning your customers’ trust in your brand and products. From processes to compliance, and security mechanisms, digital trust is based on the following:
- Authentication. Enabling your customers to verify your digital identity shows that you are really who you say you are. Authentication can be used for everything From emails to websites and code-related assets (e.g., containers, software, other executables).
- Data integrity. Your customers and other users can always verify that your data hasn’t been modified by unauthorized third parties. Think about the software they download from your website, or the emails and the attachments they receive from you, for example.
- Encryption. As your communication and data transmissions are encrypted, your customers can be confident that the sensitive information they share with you is secure during transmission.
Does it sound familiar? It should, as we’ve talked about these things before as critical elements in public key infrastructure, which makes digital certificates (like code signing certificates) possible.
In the era where data breaches are constantly increasing, and phishing kits can be bought for as little as $6, digital trust, authentication, integrity, and non-repudiation have become the critical elements that’ll help you win your customers’ trust.
Not convinced? Careful! You may end up with:
- Decreased customer trust. This is particularly true if you’ve suffered a data breach. In fact, 56% of organizations interviewed by Deloitte suffered a loss of trust in their brand and revenue following a data breach. And this takes us to the next point,
- Fewer sales. As confirmed by a McKinsey September 2022 survey. 40% of the customers affirmed to have often or always stopped buying a product from a company when it didn’t adequately protect digital data.
- An ineffective digital transformation. The Information Systems Audit and Control Association’s (ISACA) latest survey shows that 97% of respondents consider digital trust an important element of a successful digital transformation.
Before we wrap up, let’s not forget the huge impact these three digital signature uses can have on trust when talking about software security. Do you know what happens when your customers try to install unsigned software?
Their system will show them a warning like the one below informing them that the publisher of the software is unknown.
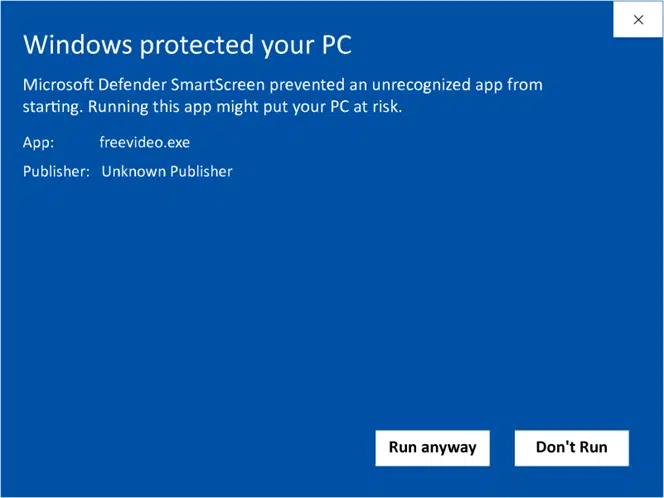
How would you think this will impact their trust in your brand and products? I’ll let you answer the question, but I guess that if you haven’t done it yet, you’ll start signing your codes soon.
This way, your customers will either see a less alarming pop-up (when you choose an organization validation – OV signing certificate), or nothing at all as your software will be immediately trusted by their system (when you go for the extended validation – EV signing certificate).
Final Thoughts on What Are Three Uses for Digital Signatures
Nowadays, more and more business agreements, transactions, and interactions are taking place online. Digital signatures are playing a key role in ensuring the
- authentication,
- integrity, and
- non-repudiation
of all digital assets exchanged online, guaranteeing a high level of security.
In the age of data breaches and malware, digital signatures can help you foster trust not only in your products and services, but also in your brand.
You can have wonderful products with fancy features. But if they aren’t secure and your customers don’t trust you, you’ll just be another business among millions and they’ll move on to find one that will earn their trust.
So, stand out from the crowd — sign your digital assets now, and watch your business and brand bloom like flowers in springtime.



