How to Become a Verified Publisher with Microsoft
Get verified: discover how to become a verified publisher with Microsoft. Learn how to boost customer trust, revenue and adoption of your products while protecting your organization from data breaches and malware
Over the last couple of years, we’ve witnessed an exponential increase in apps usage in every aspect of our daily life: work, leisure, travel, shopping, you name it, there’s always an app for it. And people are using them, now more than ever, reaching an average usage of 4.8 hours per day in the top mobile markets, as stated in App Annie’s State of Mobile Report 2022.
However, while applications have become an integral part of our lives and even facilitated remote working through collaboration, they’ve also become attractive to attackers trying to gain access to valuable data. And the same can be said for desktop applications since 42% of users still use laptops and desktop devices.
How? Have you ever heard of consent phishing? Basically, rather than stealing a user’s password, an attacker fools the user to grant a malicious app permission to access its systems and sensitive data. To prevent these kind of attacks, Microsoft has implemented a verification process for application publishers.
In this article, we’re not only going to dig into this process, but also explore how you can become a verified publisher with Microsoft even when publishing third-party software like kernel-mode updates, driver packages and more. You’re going to learn:
- The meaning of publisher verification.
- How becoming a verified publisher helps you protect customers from software-based attacks while fostering their trust in your products.
- How to become a verified publisher with Microsoft, step by step.
What Does Being a Verified Publisher Mean?
Before we can answer the question of how to become a verified publisher with Microsoft, we first need to at least understand what it means to be a verified publisher in the first place. In this digital age, trust is an essential ingredient of every successful business. For developers it’s even more important: gaining customers’ trust boosts your reputation, adoption rates, and, as a result, augments your revenue.
Publisher verification is an effective way to establish trust. This enables you, as a verified publisher, to confirm to your customers on the backend that the app, code, or driver package you developed came from an authentic source. That’s because when you’re a part of the Microsoft Verified Publisher Program, your digital identity is tied to your app’s registration through the tech giant’s identity platform.
The first time a user runs an application tied to your Microsoft verified publisher profile, they’ll receive a message that confirms your digital identity and confirms that the app came from you. This is particularly useful for helping their organization’s IT admins mitigate risk by verifying the application’s authenticity. They can set app consent policies that specify which programs (e.g., only those released by Microsoft Verified Publishers) their organizations’ users can install and use.
From multi-tenant apps to third-party software, from Microsoft kernel-mode updates to driver packages, every developer can (and should) take advantage of publisher verification and enjoy all the benefits that come with it. But why is being a Microsoft verified publisher so important? Let’s find out!
Why Becoming a Verified Publisher Matters
We’ve already talked about trust, but that isn’t the only advantage of becoming a verified publisher. In fact, it can be beneficial in many ways:
- Warranted authenticity. Customers will be able to immediately spot that the app/code/driver package is coming from an authentic and trusted source. How? In case of a multi-tenant application, for example, the customer will visualize a “verified” badge on the Azure AD consent prompt. That’s the little blue star with the checkmark inside.
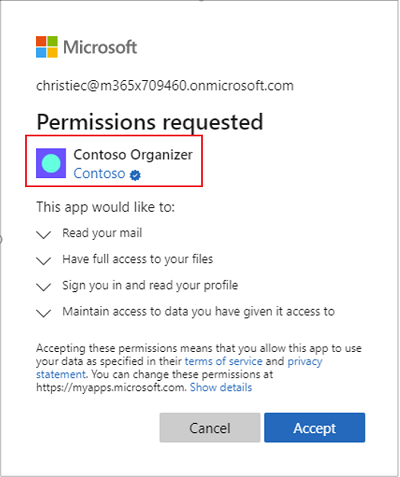
An example of a verified badge on the Azure AD consent prompt. Image source: Microsoft.
- Increased reputation. If you were to choose between two Twitter news accounts — one has the verified badge and the other one hasn’t — which one would you trust and follow? Our guess is that you’d choose the verified one, right? Why? Because if it’s verified, it automatically looks reputable. This is exactly what happens when you become a verified publisher: the customers see your badge, know that your code/app is safe (because you’ve been validated), and your reputation, reliability and credibility as a software vendor or developer go up.
- Maximized adoption. Regarding multi-tenant apps, admins are able to configure user consent policies in a way that user consent is allowed only for those applications that have been issued by a verified publisher. They can also set application control policies that restrict access or use of verified applications. This won’t only boost adoption, but also reduce the risk of data breaches. The same will happen with driver packages: as they’re verified, customers will feel safer and will be keener in downloading them.
- Higher revenue. Releasing verified apps and codes will enable you to increase customer trust that, in turn, will boost downloads and increase revenue. In addition, since Nov. 8 2020, unverified multi-tenant apps are being blocked by Microsoft. Microsoft has also become the unique provider of production kernel-mode code signatures, implementing a new process for signing kernel-mode driver packages since June 2021. This means that if you’re developing apps or codes for Microsoft’s environment, you’ll have to abide Microsoft’s processes and get verified.
- Helps reducing phishing attempts. It doesn’t seem a coincidence that since Microsoft implemented the new processes we’ve just mentioned, the number of attempts to steal personal information through phishing attacks against its brand have dramatically dropped. As a matter of fact, Check Point’s 2021 research data on the most imitated brands, reflect this new trend. According to Checkpoint’s research, Microsoft, which was always the top impersonated brand by phishers, dropped from 45% of all brand phishing attempts globally in Q2 2021 to 29% in Q3. It then dropped to a surprisingly low 20% in Q4 2021. For the first time in a long time, the most targeted brand wasn’t Microsoft — this time, it was DHL.
Don’t get me wrong, there are many other factors that contributed to this result. However, it looks like Microsoft’s new approach paid off and, somehow contributed to this trend change. Here’s a quick look at the breakdown of brand impersonation according to Check Point’s Brand Phishing Report Q2 2021 research on the top phishing brands in Q2 2021:
- Microsoft — 45% (this number relates to phishing uses globally)
- DHL — 26%
- Amazon — 11%
- Best Buy — 4%
- Google — 3%
- LinkedIn — 3%
- Dropbox — 1%
- Chase — 1%
- Apple — 1%
- PayPal — 0.5%
Now, let’s compare this to how these rankings matched up in Checkpoint’s Q4 2021 data:
- DHL — 23% of all phishing attacks globally
- Microsoft — 20%
- WhatsApp — 11%
- Google — 10%
- LinkedIn — 8%
- Amazon — 4%
- FedEx — 3%
- Roblox — 3%
- PayPal — 2%
- Apple — 2%
How to Become a Verified Publisher with Microsoft
If you’re a developer and want to take your reputation and adoption of your codes/apps a step further, you’ll definitely want to become a Microsoft verified publisher. Throughout the rest of the article, we’ll show you how to do so in a few, easy steps.
It’s important to highlight that the process will be slightly different depending on what you’re planning to develop. In this article, we’ll describe the procedures for the following two main use cases, and a bonus one:
- Multi-tenant applications. Where a single application (and database) is shared by multiple customers (tenants) but each tenant’s data is isolated.
- Kernel-mode updates. This includes critical items such as driver packages.
- Third-party software. Learn how to certify the authenticity of non-driver software and non-kernel mode driver packages.
Microsoft Multi-Tenant Applications Process
Say, you’re developing a food delivery multi-tenant app for Microsoft environment and you aren’t a verified publisher yet. How can you become one? It’s easy as pie! And, if you already meet the requirements listed below, you’ll get it sorted in a flash.
Microsoft Verified Publisher Requirements
Before you can become a verified publisher, you’ll have to make sure that you meet certain prerequisites:
- Own a verified Microsoft partner network ID (MPN ID). This first requirement is that you have a valid and verified MPN account. The account must be the Partner global account (PGA) for your organization.
- Register your app and add a publisher domain. You’ll need to register your application in an Azure Active Directory (Azure AD) tenant and add a configured Publisher Domain.
- Use an email address matching your app’s publisher domain. You’ll have to ensure that the email address’ domain used for the MPN account verification matches the publisher domain configured on the app. Alternatively, it can otherwise match the DNS-verified custom domain name included in the Azure AD portal.
- Be an authorized admin able to make changes in Azure AD and in Partner Center. You must be authorized to make changes to both the app registration in Azure AD (as Application Admin, Cloud Application Admin, or Global Admin) and the MPN account in Partner Center (as MPN Admin, Accounts Admin, or Global Admin).
- Verify your Microsoft Verified Publisher profile. Sign in using multi-factor authentication in order to get verified.
- Agree to the terms of use. Before you can become a Microsoft verified publisher, you must agree to the Microsoft identity platform’s terms of use for developers.
By the way, even if it looks like a bit of work, getting the requirements set up won’t cost you a penny and you can only gain from doing it.
Get Verified and Display Your Blue Badge!
Now that you’re all set, you can complete the publisher registration process and get your new app released as a publisher verified in a matter of minutes. To mark your app as coming from a Microsoft verified publisher, you’ll need to associate your MPN account with your app registration and follow Microsoft’s instructions.
That’s all! Once you’re done, your app will be ready for distribution. When the customers use the app for the first time, a consent pop-up will request them to give access to some of their data to the application. The Azure AD consent dialog box is exactly where the verified publisher blue badge icon like the one below will appear

In addition, your admins will be able to choose and set the consent policies of their choice, and even customize them in a few clicks. As a result, your reputation and revenue will skyrocket. Pretty neat, eh?
Before we move on to the next use case, don’t miss this cool, short video showing you exactly how publisher verification works for you and your customers in less than three minutes:
Kernel-Mode Updates and Third-Party Software
Multi-tenant applications are just a small part of the multitude of software and codes being developed today. Let’s find out how to become a verified publisher with Microsoft as a developer of kernel-mode updates, driver packages, third-party software, you name it.
Kernel-Mode Updates and Driver Packages—Requirements
Are you getting ready to distribute a new Microsoft kernel-mode driver package? Before you do that, you (or your admin) will have to:
- Sign in in your organization’s Azure active directory as a global administrator. If you don’t have an active directory, the registration process will guide you to create one free of charges.
- Register for the hardware program in order to get access to the Partner center. This will enable you to easily create and manage your driver-related submissions in a blink of an eye.
Important! Don’t forget that since 2021 you won’t be able to sign kernel-mode codes with an EV code signing certificate anymore.
Now that you’re registered, you can proceed to the next and final step.
Submit Your Drivers and Get Certified!
If you’re happy enough with your new drivers, it’s time to submit the final version through the Partner center and become a verified publisher. How? You just have to follow Microsoft’s updated hardware process for drivers submission and you’re done!
You’re ready to distribute your drivers with Windows update or publish them as a verified Microsoft publisher.
Third-Party Software (Non-Driver/Non-Kernel Codes)
What about third-party software? Is there a way to confirm to the users that your Windows executable is legitimate and, thus, ensure that it’s not identified by Windows browsers and operating systems as suspicious? Of course there is! You’ll just have to sign your executables using a code signing certificate via Microsoft Signtool.
Requirements
Before you go ahead, like all processes nowadays, there are some prerequisites to satisfy:
- You own a code signing certificate, ideally an extended validation (EV) one. Why? The extended validation code signing certificate is much more effective compared to the standard organization validation (OV) one. It gives you automatic trust with Windows browsers and operating systems bypassing Windows SmartScreen warnings. Remember that you can always purchase it from publicly trusted certificate authorities (CAs), and that EV certificates can only be used to sign non-driver code and non-kernel mode driver packages.
- You have Microsoft Signtool already installed on your machine. Usually included in your Windows software development kit (SDK), should this not be the case, you can download and install it in a few clicks.
Sign Your Executables With Microsoft Signtool and Get Ready to Shine
Are your ready to say goodbye to those annoying (and detrimental for your reputation) pop-up warnings? The signing process is quick and painless — you just have to follow it — and at the end, verify that your executable has been signed successfully.
From now onward, when a customer downloads your software, they’ll be able to install it immediately and trust you as a developer, knowing that your executables are trustworthy and safe to run. What more could you want?
Final Thoughts on How to Become a Verified Publisher with Microsoft
The growth of cloud computing, apps and remote/hybrid working will continue its upward trajectory. Thus, the importance of cybersecurity is paramount to better position your business in such a challenging and changing environment.
Given the rising trend of consent phishing attacks, organizations must now go beyond the traditional approaches and security measures. Becoming a verified publisher with Microsoft can be an effective defensive measure to protect your users and your reputation.
Take advantage of publisher verification and show your customers that your app or code is coming from an authentic source. Build trust, increase adoption, and protect your sensitive data!



