Which Cyber Security Coding Skills Do You Need for Your Career?
According to Fortinet’s report, 80% of organizations worldwide suffered one or more data breaches due to a lack of cyber security skills and/or awareness. Do you have the right know-how to avoid this happening to your company? Find out which cyber security coding skills you need and become the most wanted cyber security expert in the market
Job roles in the cyber security industry appeal to many nowadays. And with nearly 600,000 job openings in the U.S. alone, there has never been a better time to take the leap for those interested in pursuing a career in this sector. Being at the forefront of the war against cybercriminals can be an exciting adventure. However, lacking the core technical skills can be a real showstopper (and we don’t mean that in the good way!) for any cyber security professional’s career. This is where having strong cyber security coding skills comes into play.
This first piece in a series of two articles will explore the appropriate coding skills for your cyber security job role. Find out the top programming languages you can’t do without. Get ready to rise to the challenge of mastering the basics and add some programming fundamentals to your expertise. Your time to thrive in the cyber security sector is now!
Why Should I Care About Cyber Security Coding?
When I started my career as a cyber security professional, I had no idea about programming and, frankly, I had no interest in learning it. At the time, coding was the exclusive domain of software developers and engineers. They were creating the applications, and we were dealing with security issues. A few years later, I’m addicted to bash, pretty good at JSON, and very familiar with nearly all the cyber security coding languages listed in this article.
Times have changed and so have the skillsets and expertise required to be successful in such a constantly evolving environment. Cyber security experts have to adapt with the rise of cloud computing, artificial intelligence, and cyber-attacks becoming more prolific. Having a basic understanding of programming is no longer just a nice to have skill; it’s become a must for many professions.
Having strong cyber security coding skills enables you to identify malicious code and evaluate its severity and impact. Automating tasks and testing applications for vulnerabilities isn’t an issue anymore. You can do all this and more with some level of coding abilities.
However, with so many programming languages available, choosing which cyber security coding languages you should learn isn’t an easy task. Your choice should depend on which field and role you’ll be focusing on. Don’t be afraid, though. We’re here to help you make the right choice! That’s why we put together a list of the best matching coding skills related to five cyber security roles. So, grab your pen and paper and get ready to grow your skillset!
How Developing Your Coding Skills Can Boost Your Cyber Security Career
“99 bottles of beer on the wall, 99 bottles of beer.
Take one down and pass it around, 98 bottles of beer on the wall.
98 bottles of beer on the wall, 98 bottles of beer.
Take one down and pass it around, 97 bottles of beer on the wall…”
And on it goes. Did you know that this is a traditional reverse counting song that has been coded in 1500 different programming languages? Yup! Every single one of them generates the lyrics of the song. This gives you an idea of how many coding languages exist out there. It’s simply amazing, right? OK, enough singing. Let’s find out which coding skill goes with your job role:
| Cyber Security Role | How Secure Coding Languages Fit in With This Role | Alternative Cyber Security Coding Language |
|---|---|---|
| Security Operation Center (SOC) Analyst | Python is a popular coding language for this role because writing a script in Python might help you analyze data more accurately and quickly | Bash, PowerShell, and SQL would also be good additional languages to know. |
| Software Security Lead | Java is a good language to start with. Because when you work day in and day out with the developer team, you must speak their “language” to earn their trust. | PHP, C, and C++ are also good additions. |
| Penetration Tester | Java is, once again, a good choice if you want to transform this passion for breaking things into a profession. It’ll help you understand the code behind the software and learn how to break it. | Software programs are built in many different ways and languages. Make sure to also add C, C++, and Python to your learning list. |
| Auditor | C+, C++, Python, Ruby, and JavaScript are all languages that’ll help you ensure you ask the right questions and interpret the answers you get correctly. | SQL and shell scripting can also be useful if you need to query databases or automate some tasks. |
| Chief Information Security Officer (CISO) | As you’re the ultimate security and data protection expert for your organization, the more languages you are familiar with, the better it is. | JavaScript, Python, PHP — you name it. |
Your job role isn’t included in the list? No worries. There are so many different positions in cyber security that it would’ve been impractical to list them all. Keep on reading. In the next section, we’ll present to you the best programming skills to learn for any cyber security professional.
8 Essential Cyber Security Coding Languages You Should Learn
Have you ever had to go through your device’s log data to troubleshoot an issue? If you do it manually, it can take ages and you may never find what you’re looking for because you get lost in all the “noise.” But if you use an SQL query to break down your logs into smaller chunks (log parsing), you’ll get what you need in a matter of seconds. This is an example of how useful cyber security coding languages can be in your daily job. Now, let’s see the characteristics of these versatile languages one by one.
Too busy to read through the full section for each programming language? Check out our summary table below for the highlights:
| Cyber Security Coding Language | What’s Used For? (Examples) | Why Is It Useful to Cyber Security Professionals? (Some examples) |
|---|---|---|
| 1. Python |
|
|
| 2. C and C++ |
|
|
| 3. JavaScript |
|
|
| 4. Hypertext Preprocessor (PHP) |
|
|
| 5. Structured Query Language (SQL) |
|
|
| 6. Ruby |
|
|
| 7. Assembly (ASM) |
|
|
| 8. Shell Scripting (PowerShell, Shell, and Bash) |
|
|
1. Python
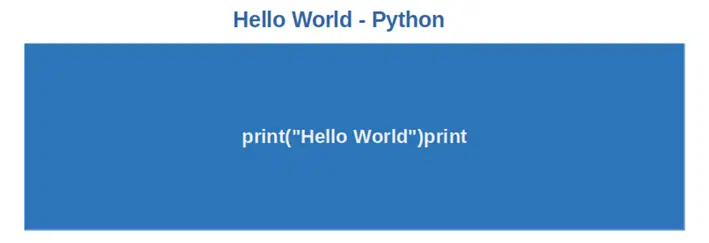
Python is considered the most popular of all programming languages as of May 2022 and the second most popular language in the first quarter of the same year, according to the Tiobe index. This language has more than 15 million users worldwide and is widely used for:
- Penetration testing. Looking to speed up and expand the scope of your pen-testing? Use Python to write and customize scripts to perform attacks, network, and web application scans. Still, learning? Check the examples available on GitHub like brute force passwords attacks or URL redirection.
- Malware detection and analysis. Do you want to scan files, processes, or strings for malware? Tools like Pyew, Yara-python, and Clamd are all based on Python. They’ll enable you to automatically detect, classify, and analyze malware without effort.
- Secure socket layer/transport layer (SSL/TLS) certificates validity check. As a cyber security professional, you must ensure that your organization’s applications are secure. SSL/TLS certificates are part of the game. Wouldn’t it be wonderful if you could automatically check their validity? You can do that by writing a Python script that checks the certificate’s digital signature’s validity and format, the size of its public key, and if the hashing algorithm used in the signature is strong enough.
Why Is Python a Useful Cyber Security Coding Language?
Python can be a powerful ally against attackers for several key reasons:
- Python is easy to learn and implement. Based on English syntax, it’s a good option for beginners.
- It has an extensive library and is open source. Thus, several cyber security tools and modules are already available for free.
- Python is a general-purpose and versatile language. Therefore, it can be used both for basic and complex cyber security tasks (see examples above).
- Programs can be executed directly from the source code.
- It’s one of the preferred languages to hack web servers.
2. C and C++

Created between the 70s and early 80s, C and C++ are old language programs that are part of the same family (C++ is the enhanced version of C). C is ranked as the second most used language in Tiobo’s list. We’ve grouped them together as organizations often prefer candidates with a high-level knowledge of both languages. They’re used for:
- Spot programming errors and bugs. Stay one step ahead of the hackers and discover bugs, inconsistencies, programming, and technical errors before an attacker finds them. How? With Lint, a tool that’ll check multiple C-language source files and/or library definitions for errors.
- Detect vulnerabilities and weaknesses. If your organization has integrated security into its development process (secdevops or devsecops), you can’t do without scanning tools like Klockwork, Cppcheck, or Flawfinder. They’ll enable you to automate your C++ code analysis and get reports on vulnerabilities ranked by severity.
- Develop desktop and mobile apps. C++ is used nearly everywhere. In operating systems, games (e.g., World of warcraft), game consoles (e.g., Xbox and PlayStation), IoT devices, databases, web browsers, and machine learning tools, you name it. Developers use them to build the software, you use them to fix it. If you want to start a career in cyber security, they’re languages you should get familiar with.
Why Are C and C++ Useful Cyber Security Coding Languages?
- C and C++ are great to do reverse-engineering and finding flaws.
- Several cyber security tools (e.g., Nmap, a network mapper tool) are written in C++.
- Many Windows, Linux, and iOS programs use C.
- Hackers love C++: they use it to write their malware, reverse engineer software, and get easy access to system infrastructure.
- When a system is compromised, it can get you low-level access to its memory and processes.
- C is often used to simulate library hijacking attacks.
3. JavaScript
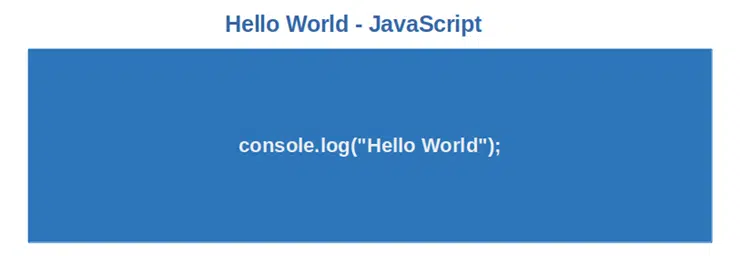
Used by 98% of websites for cookies, animations, interactions, user activity tracking, and more, it mustn’t be confused with Java. Learning this language is a must if your job focuses on websites and/or web application security. It’s used by cyber security professionals to:
- Prevent cross-scripting attacks (i.e., malicious scripts injected into websites). JavaScript is so popular that websites and applications using it are juicy targets for attackers. Protect your organization’s application and web pages by ensuring that they’re coded securely to avoid XSS attacks.
- Foster secure coding. No matter in which industry you’re working, you’ll want your applications, API, and websites as secure as possible. Knowledge of JavaScript will help you promote and implement secure coding best practices that’ll avoid malicious codes being used to run a program.
- Identify security exploits. Did you know that hackers can use JavaScript to track the data entered into a web form, redirect users to a fraudulent website or analyze your users’ browsing habits? With data breaches in the U.S. showing a 14% increase in the first quarter of 2022, you don’t want your organization being included in that percentage. Learn it so that you can make sure you’re able to understand the difference between a good and bad script.
Why Is JavaScript a Useful Cyber Security Coding Language?
- It enables you to design secure websites, forms, APIs, and applications by mitigating the risk of potential XSS attacks.
- With JavaScript, you can work with cookies or manipulate and exploit event handlers (e.g., a form is sent when the user clicks on the submit button).
- Hackers use XSS attacks to spread malware and Adware.
- It can be used to simulate server or client-side attacks.
4. Hypertext Preprocessor (PHP)
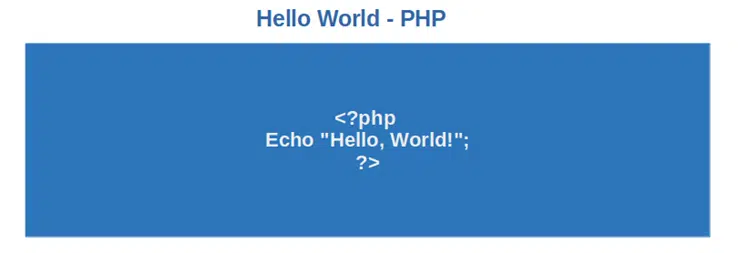
PHP is an open-source programming language that’s also vital script for websites. It’s a server-side code (i.e., applications run on a webserver) that’s great if you want to display tailored information based on user preferences. It’s used by many social networks, including Facebook. Cyber security professionals like it because it:
- Makes it easy to update a website. Web developers and designers often use PHP to facilitate website updates by connecting the database with the web pages.
- Protects your databases. If you know PHP, you’ll be able to identify websites’ vulnerabilities and address them before your organization becomes a victim of a denial of service (DDoS) attack.
- Easy to learn. Are you already familiar with C or C++? then you’ll have no problem working with PHP. And if you have issues, there are several developer communities and tons of documentation waiting for you.
Why Is PHP a Useful Cyber Security Coding Language?
- With Research and Innovation to Promote Security (RIPS) tool, a PHP security scanner, it’s really easy to identify vulnerabilities in PHP scripts in real time.
- PHP applications are platform-independent; therefore, they can run on any operating system of your choice.
- Being an extensively used language makes it easier for cyber security professionals to implement the same hacker-proof solution to all PHP-based web applications available in their organization’s portfolio.
- It helps you combine cyber security with your organization’s websites, thereby reducing the frequency of attacks.
5. Structured Query Language (SQL)
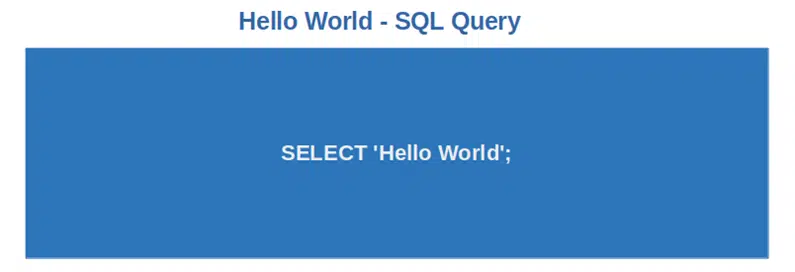
How do you stop an attack on your organization’s databases without having a strong knowledge of SQL? You can’t. Therefore, if you’re dreaming of a career in cyber security, get ready to learn the ins and out of this programming language because SQL is used to:
- Build machine learning modules. I managed a similar project when working as an application security product manager. The data scientists in my team collected and analyzed millions of data in a wink using SQL queries. Once done, they built a few machine learning modules to automatically identify, classify, and sanction anomalies in log-in activities.
- Find, add or delete information stored in a database. Database administrators, security analysts, developers, and even end-users can perform actions on a database through SQL queries. For example, when a user attempts to log in to a website, the hash of the password (not the password itself) stored in the database is compared with the hash of the password the user just typed in. If they match, the user has access to the website. If not, their login attempt will be denied.
- Eliminate unused IDs and passwords. Regularly querying your SQL database for inactive IDs (and deleting them) helps prevent unauthorized access to your organization’s internal tools.
Why Is SQL a Useful Cyber Security Coding Language?
- Knowing how to work with SQL queries and their uses will enable cyber security professionals to identify and protect websites and applications from SQL injection attacks.
- Kibana and Elastic search are popular threat analysis tools used by many organizations. With SQL, it’s possible to search across billions of data and get real-time results.
- For email providers finding freshly opened fraudulent or spamming accounts, it’s easier when using an SQL query to look for known suspicious usernames (i.e., the info before the @ sign) like bankofamerica, PayPal, and IRS.
6. Ruby
Ruby’s syntax is pretty similar to Python and it’s used by many well-known websites like Airbnb, GitHub, Hulu, and Kickstarter. It’s a web-oriented language easy to use and learn. Ruby is mostly used for:
- Web development. Have you ever heard of Ruby on Rails? It’s one of the most popular web application development frameworks based on Ruby. This framework enables developers to spend less time writing codes thanks to its code generators. It’s often a popular choice by startups as it allows them to build large applications quickly and with limited resources.
- Static website creation. Are you looking to build a website that is fast, secure, and easy to deploy? You can do it with Ruby. All pages are generated in one go and deployed to a server. When a user visits your website, they view a static HTML page.
- Automate tasks. Applications like Heroku, Chef, and Puppet enable development teams to automate and simplify many tasks while ensuring security and compliance. Thus, your devops colleagues will have more time to focus on more important duties.
Why Is Ruby a Useful Cyber Security Coding Language?
- Tools like Bcrypt-ruby (a Ruby binding for OpenBSD bcrypt password hashing algorithm) allow hashed password storage, protecting users from identity theft.
- It supports large code projects.
- Ruby enables developers to build programs from scratch with less code and quickly. Less code often equals fewer errors and vulnerabilities to manage.
- Vagrant, a tool based on Ruby, allows organizations to reduce costs and time associated with bug fixes. How? By mirroring different production environments through virtual machines. This enables developers to make sure that the codes will work flawlessly on all operating systems (Linux, Microsoft, you name it).
7. Assembly (ASM)

With the amount of identified malware in the first five months of 2022 already surpassing the total malware detected in the whole previous year, understanding how it works is a key skill for any cyber security professional. So, is that the only thing that Assembly can do? Of course not.
- Assembly allows you to communicate directly with a device’s hardware. It’s a low-level programming language (i.e., more difficult to understand by humans but more memory efficient) that’s used to give direct instructions to devices’ processors.
- It helps you take malware apart before an attacker takes your career apart. Hackers are clever little buggers. And when they write malware, they ensure that it can’t be easily read or understood (obfuscation). Programs like OllyDbG and IDA Pro will break down the suspicious program into assembly components. From there, discovering how the malware works will be as easy as pie.
Why Is Assembly a Useful Cyber Security Coding Language?
- Allows you to take a piece of malware and figure out what it does (reverse engineering). You can do that easily if you master Assembly. But be forewarned: this is not an easy language to learn or master, and many colleges and universities no longer teach it.
- Helps you find security flaws in a program (vulnerability research).
- Enhances your cyber attack analysis capabilities because you can use it to run some memory forensics to find out what happened.
- It can help you simulate operating system hackings, stack smashing (stack buffer overflow attacks), hardware device attacks, and application usage restrictions.
8. Shell Scripting (PowerShell, Shell, and Bash)
Have you ever opened a terminal session on your machine? Then there are high chances that you’ve already used some basic shell scripting. Depending on your operating system, you may want to focus on one of them:
- Bash (i.e., bourne again shell) for Linux and Mac
- PowerShell or Shell for Windows
But what are these cyber security coding languages used for?
- Automate routine tasks. Extracting IP addresses from files to detect suspicious ones, gathering system information, and aggregating data. These are all typical tasks in a cyber security professional’s day that can be automated with a shell script. Ready to say goodbye to that tedious, time-consuming manual work?
- Account management. A new hire has just joined your team and you need to give him quick access to systems and tools? Write a couple of scripts and he’s ready to go.
- Collecting information about devices. With PowerShell, performing advanced tasks with less work isn’t a problem anymore. Desktop settings, installed hotfixes, local users and owners, or login information. All this will be at your fingertips just by using the right scripts.
Why Are Shell Scripting Useful Cyber Security Coding Languages?
- They enable developers to sign executables using Microsoft Signtool, boosting security and customers’ trust.
- Shell scriptings allow anyone to compare file signatures, protecting devices from dangerous downloads and corrupted files.
- Because PowerShell and Shell are installed by default on Windows devices, they’re popular language choices among attackers.
- They let you analyze malware with various techniques such as reverse engineering, interfacing with VirusTotal API, and examining executables.
- They’re helpful in many penetration test tasks, e.g., reconnaissance (gathering information about a target) or script obfuscation (making it difficult to understand).
- They allow you to control user permissions ensuring that users get only the ones necessary to perform their job (principle of least privilege).
How to Start Learning Cyber Security Coding Languages
Did you pick the programming language of your choice and want to start learning it? Let’s check what kind of options are available out there.
Online Courses
There are thousands of online coding courses, covering all levels of knowledge. The most popular are:
- Coursera. It offers more than 2,000 programming courses set up by respected Universities like Johns Hopkins University, Princeton, and major IT companies. For example, the course Code yourself! Introduction to Programming could be a good starting point. Did you choose to learn C and C++? Coding for Everyone: C and C++ is the course for you.
- Codecademy. Basic courses are free and include peer support. You can start with their code foundation classes or take a short quiz and get course recommendations based on your answers.
- edX. This is another excellent online resource where you’ll find more than 60 coding languages courses. You can start with Programming for Everybody or, if you’re interested in Python, with Introduction to Computer Science and Programming Using Python.
- FreeCodeCamp. A collection of more than 8,000 free coding tutorials. What do you want to learn first? From basic JavaScript courses to Assembly there’s a course for everyone. They also have a YouTube channel.
- Google training. Google offers a lot of free learning resources and videos like learning basic JavaScript with the Grasshopper app or getting an introduction to coding. And if you’re a developer, you can improve your skills or learn to code with Grow with Google.
- W3schools. If you’re like me and enjoy learning by doing, this is the website for you. Its tutorials offer interactive online exercises and examples, providing you with real, hands-on experience. Do you want to learn SQL? The tutorial even includes an online SQL editor enabling you to edit SQL scripts and view the results in real time.
Free Video Tutorials on YouTube
You can surely do your own search and find a plethora of videos and channels on any cyber security coding language. The ones below are some of our favorites:
- CS50 channel. Harvard University’s computer science courses. All for free and including subtitles.
- Computer science crash course. 40 videos about computer science, for those who want to discover the basics of computers before immersing themselves in learning to code.
- Mike Dane’s tutorials. It has a lot of courses in several programming languages. Do you want to start learning Ruby? Check out Mike’s playlist.
Books and Ebooks
If you prefer reading a book to watching videos, you don’t want to miss O’Reilly publications:
- Head First Learn to Code. Learn how to think like a computer and how to write code to make the computer do exactly what you want.
- Learn to Program with Assembly: Foundational Learning for New Programmers. This may be a great option for those who want to learn the basics about Assembly.
- Learn to Code by Solving Problems. This is an interesting, interactive book. Discover how to solve problems with Python through finding solutions to real-life coding challenges.
Coding Bootcamps
If you really want to get serious with cyber security coding skills and are willing to invest the money into it (yes, they’re a bit on the expensive side), coding bootcamps may be for you.
- Fullstack Academy. Based in New York, it offers also online coding bootcamps. They also have info sessions where you can learn about their bootcamps offer before spending the money on it.
- Flatiron School. Offering several bootcamp options to accommodate any student’s busy schedule, it’s available in Denver, New York, and online.
- Brainstation. With locations in Canada, U.S., and United Kingdom, it also offers part-time or full-time bootcamps online. Some courses include hands-on experiences with real-life business cases and projects.
Online Communities
Last but not least, getting involved in a community will help you not only make connections with experts in the area, but it’ll also represent a powerful learning resource where you can ask questions and learn from others.
- GitHub. One of the most known and used active developer communities. It’s also a code repository for open-source projects.
- Stack Overflow. Got a question about programming? This is the forum for you.
- Learn Programming (Reddit). A subsection of Reddit that’s dedicated to discussions about programming-related everything.
That’s it for now. I know, it was a lot, but it should help you choose the right coding languages for your career. Interested in knowing more? Don’t miss our Ultimate Programming Best Practices Guide. Coming soon to this blog!
Final Thoughts on Which Cyber Security Coding Skills You Need to Learn for Your Career
Although not all IT security roles have cyber security coding at the heart of their skill requirements, having at least a basic understanding of programming fundamentals can get you ahead of the pack. Maybe you’ll never write your own code, but being able to understand what others have written can make your life easier and help you progress in your career.
In this article, we’ve listed the most used and wanted programming languages: Java, PowerShell, SQL, and PHP, just to name a few. We’ve explored their purposes and degree of complexity. Now it’s time for you to pick and choose the ones that best fit your job role and level of knowledge. If you’re a beginner, you may want to start with Python. If you’re a bit more advanced and want to understand how malware works, you could consider Assembly.
Code is the language of the future, and it’s here to stay. If you want to be part of the cyber security army and succeed in your profession, you must have some knowledge of at least one cyber security coding language. Become a cyber security hero. Start learning your coding now!



