10 Application Security Best Practices to Have Under Your Belt
You can’t be too careful when it comes to the security of your applications. Put these 10 best practices to use to keep your business safe
Cybersecurity has become an increasingly hot topic in the business and tech world. With an increase in users and the complexity of applications, it’s virtually mandatory to ensure that your app is secure when released into the wild. As a cybersecurity professional, no matter what programming language or platform you’re working with, there are some key application security best practices that everyone should keep in mind throughout the devops lifecycle.
Application security is everyone’s responsibility in the software development life cycle (SDLC) — it’s just that people are responsible for different aspects of it in their specific roles:
- Developers write secure code.
- DevOps engineers work to optimize the development process and are typically in charge of things like continuous integration/deployment, testing suites, release management, etc.
- IT professionals are responsible for setting up servers, firewalls, etc.
This article will explore 10 of the most important application security best practices that can be incorporated into any software or web application. We’ll also share examples of different tools that can be used for specific functions. (Note: the tools we mention are examples and should not to be considered endorsements or recommendations.)
1. Adopt a Secure DevOps Approach
Securing your applications means adopting a secure approach to the development and operations lifecycle (devops). What this entails is ensuring that whenever there’s a change, everyone involved in the SDLC is immediately aware of it and can analyze how or if it impacts the organization’s overall security. It also requires people from both teams to work closely together at every step of the process, rather than just being part of the same project or team but working separately in silos.
By using a secure devops approach, you help reduce the risk of introducing new security issues to your application. (This is why we made this #1 on our list of application security best practices.) You also give yourself more flexibility in deciding what can or can’t be done without first having to review it.
Of course, secure devops requires a shift in attitude, mindsets, and approaches for both teams involved. Helping them to align their efforts with a common objective helps them achieve the best security possible. A few ways to go about doing this include:
- Implementing security-as-code and secure build approaches to integrate security into your devops tools, practices, and workflows to mitigate vulnerabilities and risks
- Integrating threat modeling into your devops process
- Adopting security automation tools that can streamline tasks
2. Implement Internal Monitoring, Security Testing & QA Checks
In order to ensure the security and quality of your software, it’s important to implement regular monitoring, security testing, and quality assurance checks. These practices will help you identify any potential vulnerabilities or errors in your codebase along with other problems. By catching these issues early on, you can save yourself (and your users) time and hassle down the road.
Some specific examples include:
- Static code analysis — This is a process of analyzing your code without actually running it. This can be helpful for catching potential errors, such as syntax errors or unused variables.
- Dynamic code analysis — This involves running your code and observing its behavior. This can be used to identify runtime errors or security vulnerabilities.
- Unit testing: This is a type of testing that focuses on individual units of code, such as functions or modules. This can help you ensure that your code is behaving as expected.
- Integration testing — This is a type of testing that focuses on how different units of code work together. This can be used to catch errors in communication or data flow between different parts of your system.
- Security testing — This is a type of testing that focuses on identifying security vulnerabilities in your code. This can help you ensure that your system is safe from attack.
By implementing these various types of testing, you can be confident that your software is secure and error-free.
Consider Implementing a Bug Bounty Program
As cybersecurity professionals, we understand how difficult it can be to find and fix bugs in your web application. That’s why you may want to consider seeking the help of one or more white-hat hackers (i.e., ethical hackers) through a bug bounty program. Of course, this approach isn’t for everyone, and it should never be used to replace the internal security testing and monitoring processes mentioned above.
A bug bounty is a program that offers rewards or payment to skilled individuals who find vulnerabilities or exploits within your software, website, or other systems. Bug bounties allow you to take advantage of people’s natural desire to “break things” and use those skills for good. By implementing this program, you can spend more time finding and fixing bugs for your applications while rewarding those who help you with the process.
Just be careful about how you approach hosting a bug bounty competition — if you decide to go this route at all. (There’s debate within the industry about whether these programs are a good idea or if they’re too risky.) HackerOne’s 2020 Hacker Report shows that nearly two-thirds of survey respondents indicate that they withheld sharing security flaws they discovered due to “‘threatening legal language’ posted on the organization’s website regarding the discovery of potential vulnerabilities.” Their research also shows:
- One in five ethical hackers didn’t share their discoveries because companies lacked obvious methods for reporting said issues.
- 15% of companies don’t bother responding to bug reports.
With all of this in mind, be careful about how you phrase things, be sure to provide a clear way for participants to report bugs, and be responsive to bug reports. There’s no point in having pen testers look for bugs if you aren’t going to bother fixing them once they’re reported.
3. Implement Secure Coding Best Practices & Standards
Security is not just about what we do when we’re building our application; it’s also about how we build it. When we talk about secure coding best practices and standards, we’re referring to a set of guidelines that you must follow when building an application. That way, every new line of code added follows secure standards, ensuring that your entire system is more secure from the start.
Secure coding standards aren’t just about having secure functions; they’re about improving how you implement security throughout your whole development process. An example of a resource to learn about these standards is through OWASP.
The Open Web Application Security Project (OWASP) describes itself as an “open community dedicated to enabling organizations to conceive, develop, acquire, operate, and maintain applications that can be trusted” — assuring security, privacy, and compliance with regulatory requirements. Following OWASP Application Verification Security Standards and ensuring that you’re keeping the top security risks in mind when designing your web application will help you prevent many common security issues from occurring. This includes SQL injections, cross-site scripting (XSS) issues, and other known vulnerabilities.
If you follow industry standards from the get-go, then you or your team will have to do less work on finding and fixing bugs or vulnerabilities after the release of your product.
4. Analyze Your Application for Vulnerabilities
Before adding new features or releasing an application into the wild, you should always analyze your creation to see what vulnerabilities exist in your existing code. This step is one of the most important things you should do before releasing an application because it reveals potential flaws and weak points in your program. Some of these vulnerabilities include:
- Cross-Site Scripting (XSS) — This is where a user injects client-side scripts in your web application or site to attack its users. These scripts are executed by the users in their browsers and can be used to infect users’ devices or steal personal information from them.
- SQL Injection — These bugs allow a malicious user to insert SQL commands into an application interface, giving them the ability to view or modify data. This is generally considered a server-side vulnerability.
- Information Leakage — Data leakages occur when a user can find out the information they are not supposed to know about through public interfaces, such as by exploiting error message vulnerabilities.
- Backdoors — These hidden entryways into your app allow attackers to access the backend of your application in unintended ways. This could open up security holes in your system that could result in data theft or manipulation as well as a litany of other concerns.
- Open Source Code — Integrating third-party code into your application is often considered common practice. However, these codes might have vulnerabilities that could be exploited by an attacker; this results in what’s known as an open-source vulnerability.
However, analyzing a single version of your application can be difficult, so we always recommend running automated scans on every build to ensure that vulnerabilities don’t get missed. Some useful tools would include:
- Burp Suite — a comprehensive security testing tool that can find a variety of vulnerabilities in web applications.
- Acunetix Web Vulnerability Scanner — a tool that scans for SQL injection, cross-site scripting, and other vulnerabilities.
- Web Application Firewall (WAF) — an appliance or software application that monitors and filters the traffic to your web applications. This can help protect your application from attacks that attempt to exploit known vulnerabilities.
By taking these precautions, you can ensure that your application is as secure as possible against malicious users.
5. Maintain a Secure Development Lifecycle with SecDevOps
One thing that developers could improve when it comes to security is the way they manage the different development lifecycle stages. Unfortunately, security typically takes a back seat in the traditional devops process. Developers have become accustomed to focusing on developing their program for a short amount of time and then releasing or sending updates without going back to review the code they created in the previous rounds. This means that applications can be released without them realizing that there are vulnerabilities that attackers can exploit.
Implementing secure devops (secdevops or devsecops, depending on whom you ask) means integrating security throughout all phases of the devops lifecycle. By putting security first, you can identify and address problems as you go, thereby reducing the number of issues you’ll have to deal with later before releasing your software.
External factors also can impact your application, such as requests from clients or internal developers. This could change how a function is used and that might mean you have to go back and review old code. This is why we always recommend maintaining a clear development lifecycle for everyone involved in the process so they can understand what to do during each stage of the development practice. Let’s take a look at a quick overview of what the lifecycle would look like for a typical secdevops process:
- Code development and coding practices — During this phase, developers should focus on creating the most secure code possible. This means using coding practices that will help to mitigate common vulnerabilities, such as input validation, output encoding, and proper error handling.
- Build process and integration — The build process is where you take all of the code that’s been written and turn it into a software application. This is also the phase where you want to start integrating security into your automated testing so you can catch any potential issues before they make it into production.
- Testing and pre-production — In addition to your traditional functional testing, this is also the phase where you’ll want to do some security testing. Penetration tests and static code analysis are two great options for testing your application from a security perspective.
- Release and post-production — After you’ve gone through all of the previous steps and your application is ready for production, you’ll want to have a plan in place for monitoring and responding to any security issues that might come up. This is also the phase where you’ll want to think about things like incident response, business continuity, and disaster recovery planning.
6. Use the Right Tools to Achieve Security in the Development Process
Alright, we’re officially half way through our list of application security best practices. Building security into a development process is a practice that all developers should consider. The best way to do this is by using an automated software composition analysis tool. This kind of tool will analyze your code and show you what libraries, frameworks, databases, and operating systems it uses in order to find vulnerabilities such as the open source bug Heartbleed and Shellshock.
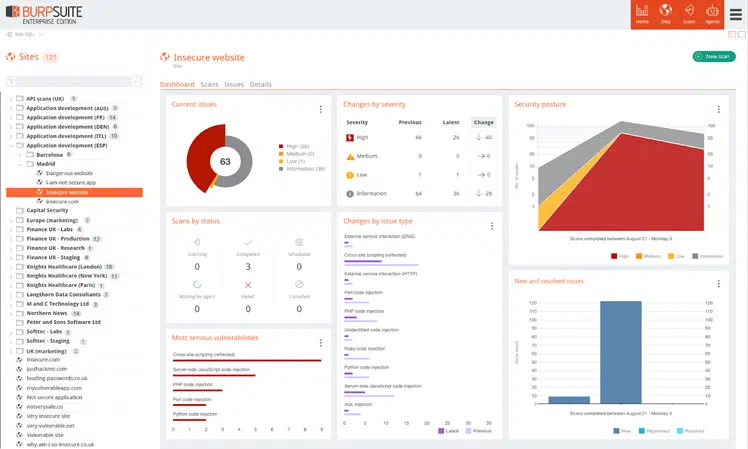
Automated analysis tools are great because they allow you to focus on the development process itself rather than having to go through it manually in order to identify vulnerabilities. This means you can free up a lot of time for yourself while also ensuring that your application is as secure as possible.
Let’s quickly explore a few examples of such tools.
Static Application Security Testing (SAST) Tools
Static code analysis tools scan your code for known vulnerabilities. They work by looking at the source code of your application and report any known bugs or problems with it, such as buffer overflows, SQL injection errors, and command injections.
Static testing differs from dynamic testing because you’ll receive results at the time of the build and not during the execution of your program. It’s also important to note that static tests can’t find all vulnerabilities and they can’t emulate user behavior; this means you should always run both forms of testing for a more accurate result.
Dynamic Application Security Testing (DAST)
Dynamic application security testing tools allow you to test your application as a user would: like a browser, crawler, file uploader, and much more. DAST tools provide the capability to simulate errors and observe an application’s response — all without touching the source code or testing it against known vulnerabilities. This type of tool will allow you to find problems such as cross-site scripting (XSS), SQL injection, and excessive permissions.
Examples of static and dynamic analysis tools include:
- Micro Focus Fortify — This is a static and dynamic analysis tool that scans for software vulnerabilities, such as cross-site scripting and buffer overflows.
- IBM Appscan — This is a static and dynamic analysis tool that scans for web application vulnerabilities, such as SQL injection and cross-site scripting.
- Burp Suite — This is primarily a dynamic analysis tool with limited SAST capabilities that finds security issues in web applications by simulating a user’s interactions.
- Acunetix — This is a static and dynamic analysis tool that scans for web application vulnerabilities, such as SQL injection and cross-site scripting.
7. Don’t Trust User Input — Sanitize User Inputs
Next on our list of application security best practices, we offer a simply warning: no matter how much you want to trust your users, there are always going to be some bad apples in the bunch. These are individuals who will try to send malicious inputs such as SQL injection attacks, cross-site scripting (XSS), and other security vulnerabilities to your application.
Exploiting web application vulnerabilities can give them access to parts of your program that they shouldn’t have access to or even allow them to take control of it.
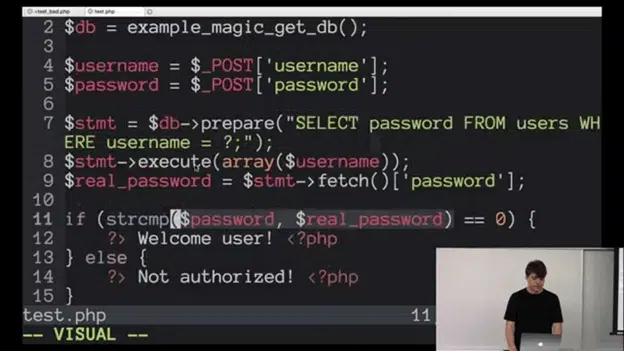
The best way to counter this is by never trusting any form of user input because you cannot predict what it is going to be. For example, if an input field on your page requests a phone number, you should always ensure that it contains only numbers for this input. Otherwise, you run the risk of unscrupulous users trying to pass SQL statements through the phone number field using other characters or unintended inputs to exploit injection-related vulnerabilities.
Sanitizing inputs is the best way to avoid this because it removes any potentially harmful code before storing or using it. This is why it is important for developers to validate all their inputs and escape them properly when displaying them so that they can be displayed correctly without exposing the application to security vulnerabilities.
As a developer, it’s important that you identify all user input when it comes in so that you can filter out any spam or fake requests. If you don’t do this, then you’re putting your application and users’ data security at risk because unsanitized input can be used to exploit vulnerabilities in the system.
Say, a user sends in some code through an input box that was created for comments. They could use this to inject their own malicious code into your application that allows them to read other users’ personal information or even inject fraudulent info into your database.
8. Limit Your Application’s Attack Surfaces by Restricting Access
One of the best ways to secure your application is to limit its attack surface. One aspect of this means that you should only allow access to the features that are absolutely necessary for their jobs (or to carry out specific tasks) while hiding any extras. If a function isn’t relevant or should only be usable by admins or other select users, set access restrictions that prevent others from using it. This process also entails limiting permissions that the application runs on your server.
This can be done by limiting the number of entry points into your app and server, which will help keep it secure because you know exactly what requests are being made on different functions. There are a number of ways that you can do this:
- Configuring the web server to only allow requests to selected pages and/or paths
- Hiding debug functions from view
- Restricting access to files and folders through the use of file and user permissions
- Implementing allowlists or blocklists for IP addresses that try to access your web app from specific geographic regions
- Not running your app as root on Linux (if a hacker discovers a vulnerability, they can exploit it to run virtually any command on the server)
Regardless of the method you choose, it’s important you understand how the application works at a core level because this will enable you to secure your product against exploits more effectively.
Limiting entry points also will save you a lot of time because there is always going to be a problem with applications that have too many access points. If you only use a few, then your app will be easier to secure and you won’t have to spend as much time on it.
Follow the Least Privilege Principle
Another thing developers should consider when trying to limit an attack surface area is using the principle of least privilege. This means that you should always run your application or service with the least amount of access possible, so any vulnerabilities will be less severe because they won’t allow attackers to get full control over the system.
9. Keep Third-Party Software In Your Systems Secure
One of the most effective ways to stay on top of application security is by keeping your third-party software up to date. Hackers are always looking for new vulnerabilities in popular applications to exploit; instead of attacking your app directly, they may look at third-party apps tied to your network instead. This is why you need to make sure that you are taking advantage of all the software publishers’ latest updates to keep network and apps safe.
Users should roll out updates at a frequency that makes sense for their business and conforms to the organization’s security policy. Many software publishers release updates on a set schedule, but others will release updates as they become available. This means that users need to be proactive about checking for updates and installing them as soon as possible.
In addition, users should also be sure to keep an inventory of the software they are using and track the updates for each application. This will help ensure that all applications are up to date, and it will also make it easier to identify any applications that need updating when new updates become available.
10. Secure Your Cloud Infrastructure
As we reach the end of our list of application security best practices, it’s time to turn our attention to the cloud. Even if your application lives in the cloud, this doesn’t mean that you don’t need to secure your digital IT infrastructure. As a developer, it’s your responsibility to make sure that everything is configured correctly; you can do this by checking all the configuration files in your environment.
One of the best ways to do this is through automated security scans using software composition analysis tools like Lynis and CIS. If you use these types of tools, then they will help you identify your infrastructure’s security risks and fix any issues that are found. Of course, these tools aren’t the only solution. Other ways of making sure everything is configured correctly include the following:
- Check Your Virtual Private Cloud (VPC) Security Groups — By default, your Amazon VPC is secure. However, there are a few things you should check to make sure that it is locked down correctly. The first thing you need to do is make sure that the security group for your VPC has the correct inbound and outbound rules. You also need to make sure that the group is associated with the correct subnets.
- Check Your EC2 Security, AMI, and Instance Type — You should also check your EC2 security settings to make sure they are locked down correctly. This includes making sure you are using the correct AMI and that your instance type is set to the correct security level.
- Check Your IAM Role and Policy — You should also check your IAM role and policy to make sure they are set up correctly. This includes making sure that you have the correct permissions for your EC2 instances and that your root account is locked down.
- Use a Firewall — You should also use a firewall to protect your EC2 instances. By default, Amazon provides a basic firewall that will protect your instances from most attacks. However, you may want to consider using a more sophisticated firewall like AWS WAF or Amazon GuardDuty.
- Use SSL/TLS — You should also use SSL/TLS to secure the traffic between your users and your applications. This will help protect your data from being intercepted or manipulated by hackers in transit.
This means that you will be better able to protect your application against attacks because these tools help secure the cloud infrastructure that it is hosted on, which can prevent attackers from getting access to sensitive data or disrupting operations.
Final Thoughts on Application Security Best Practices
As a developer, IT pro, or devops engineer, it’s your responsibility to protect your application from attackers through your individual role. This entails securing it against any vulnerabilities that are out there. This can be done by using common security practices like:
- Limiting the number of entry points and access to your servers through applications,
- Performing regular scans throughout the development lifecycle, and
- Ensuring that you configure everything correctly within your cloud infrastructure.
If you follow these security best practices, then your application will be more secure against attacks and you won’t have to worry about attackers disrupting the operations of your business.



