The “How Tos” of Internet Safety for Kids & Teens
Kids and teenagers today are typically thought of as “digital natives.” They were born a decade or two after the modern internet era began with America Online’s monthly dial-up internet in 1996. However, many of today’s kids and teens don’t know what dial-up is let alone understand the concept of a phishing email. They have an innate trust of technology and the internet in a way that we — their parents, grandparents and teachers — don’t.
As a college professor, Kshetri warns that there’s even an issue with kids and teens — all the way up through college students — feeling overly confident in their technical knowledge.
“Some of them have the idea that they know everything about cybersecurity. They know more about technology than anyone else — their parents, teachers, and professors. But just because they can do texting very fast doesn’t mean that they know a lot about technology, especially about cyber security. I think they are the most dangerous group to be victimized by cybercriminals because their awareness level is really, really low.”
So, how can we teach them about how to be safe? Part of this process involves teaching them about the different threats you’ll find on different platforms. For example, here’s a list of website-related safety threats (listed alphabetically):
- Adult websites,
- Insecure file-sharing websites (like Torrent),
- Malicious sites,
- Phishing websites, and
- Third-party app stores.
Kshetri says that he doesn’t know of much — if any — cybersecurity-related curricula that’s being offered in schools right now. His recommendation to educators is to integrate more cybersecurity-related information into their curriculum to help prepare students for the digital threats they face today and in the future.
How to Browse the Web Safely
One of the most important things you can teach kids and teens is the difference between a website being safe or secure. Don’t these terms mean the same thing? Not really. A website can use a secure (encrypted) connection, but unless you know who is on the other end of that connection, it doesn’t mean that it’s safe.
We say that because you can have an encrypted connection between your computer and a website, but if you don’t know who you’re connecting to on the other end, it’s not safe. Think of it like a spy using an encrypted phone line to share a secret message. Sure, they can share their message, but unless they know who is listening in at the other end, that doesn’t mean the message is safe.
This is why it’s vital that your “mini-mes” know who they’re interacting with online. Understanding how to determine a person or site’s true digital identity is critical to this task.
It’s very easy for a scammer to create a website with the logo
and contact information of a reputable organization.
Check If You’re on the Official Website
Whenever you visit a website, you shouldn’t trust the information displayed on the website itself. It’s very easy for a scammer to create a website with the logo and contact information of a reputable organization. Heck, they can even create website addresses that can trick you into thinking it’s the real deal.
So, how do you verify who created a website?
Learn to Read URLs
Another way to check the legitimacy of a website is to check its website address as well. But in order to do that, your kids and teens need to understand how to “read” a URL in the sense of understanding its five different components.
Here’s a quick breakdown of an example URL:

- Domain name — This is the main part of the URL that’s associated with the company name or brand. Examples include Google, Apple, and Microsoft.
- Top-level domain (TLD) — This is the part of the URL that people most often associate with website addresses. Some examples of common TLDs include .com, .net, .org, .gov, .biz, .co.uk, and .ca.
- Subdomain — The subdomain is an extension of your main domain. It’s a way for businesses to organize their sites in a way that makes it easy for users to navigate. And some websites have multiple “levels” of subdomains. For example, a first-level subdomain could be website.com. A second-level subdomain could be help.login.website.com. The further away from the domain you get (each section is divided by periods), the next level higher a subdomain you have.
- Protocol — The protocol is the channel through which data transmits whenever you visit a website. The insecure protocol HTTP stands for hypertext transfer protocol; the secur version of the protocol is HTTPS (hypertext transfer protocol secure). The first means that your data is transmitting in plaintext (a readable format); the latter means that your private or sensitive data transmits in a secure, encrypted format that no one without access can read.
- File path — This is, essentially, a road map for servers that they can follow to access files or data within a file system. It tells a server precisely where to find a specific page, post, file, or other asset. It’s a combination of the directory and subdirectory.
The subdomain, domain name, and TLD together form the host name.
Now that you understand the different parts of a URL, let’s dive into how to analyze them and what to look out for. We’ll consider Google’s official website as an example. So, when you want to visit the Google website, you want to make sure the URL reads https://www.google.com. If it says something like google.com.someotherdomain.com, it’s a fake (fraudulent) website.
Bad guys love to prey upon people by purchasing websites that look close to the legitimate ones. Some techniques they use include:
- Cybersquatting — This involves someone creating a website that looks visually similar to a legitimate website. However, there might be a difference in the order of the words. For example, “newsfox.com” instead of com.
- Typosquatting — A typosquatting URL is one that a cybercriminal buys to trick users who accidentally mistype or misspell a real website’s URL. An example of this would be “amzon.com” instead of com.
- Homograph attacks — This type of URL uses special characters outside the English alphanumeric system to create fake URLs that appear visually identical to real domains.
Check the Site’s Verified Details
First, look at the web address bar. Do you see a padlock icon (like what you see in the image below)? Cool. That means the website is sending data in a secure way. If not, that means the site isn’t secure and may be dangerous.
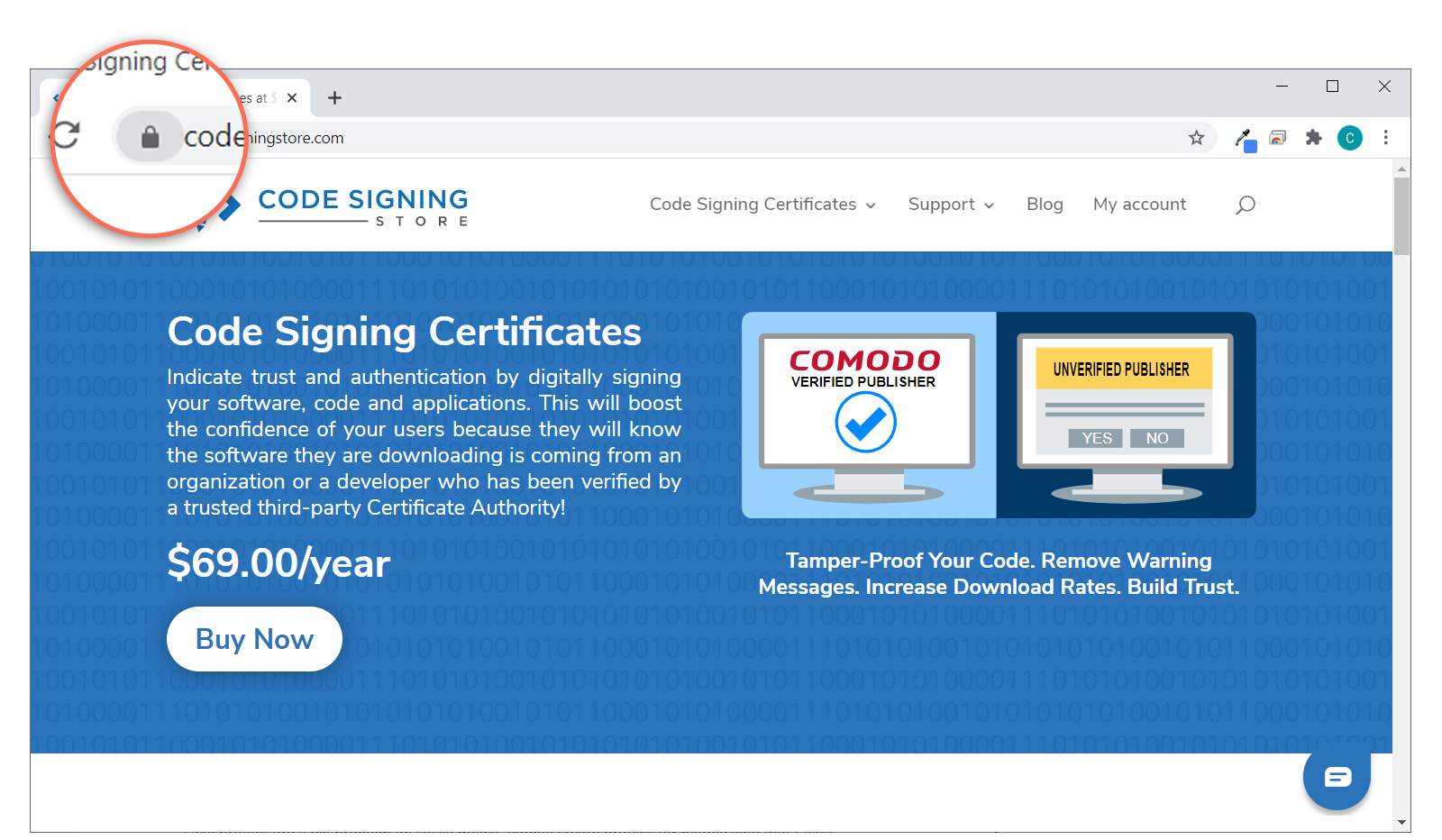
that the website is using a secure, encrypted connection for data transmissions.
To find out if the site is registered to a verified, real company, click on the padlock icon. Another window will pop up that looks like this:
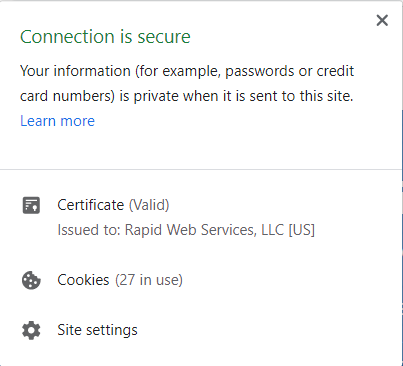
In this case, you’ll see that our website is registered to a company called Rapid Web Services, LLC. This is a company that’s based in the United States. The certificate was issued to www.staging.staging1-codesigningstore.flywheelsites.com and is valid through Jan. 10, 2022.
Of course, you can also look up more specific info about the company as well by clicking on the Details tab. There, you’ll want to select Subject and see all of the organization information that the certificate lists. So, based on the information in the screenshots below, you can see that:
- Our website is registered to Rapid Web Services, LLC.
- This company is based in St. Petersburg, FL.
- It’s a real organization because it’s been verified by the certificate authority that issued the certificate.
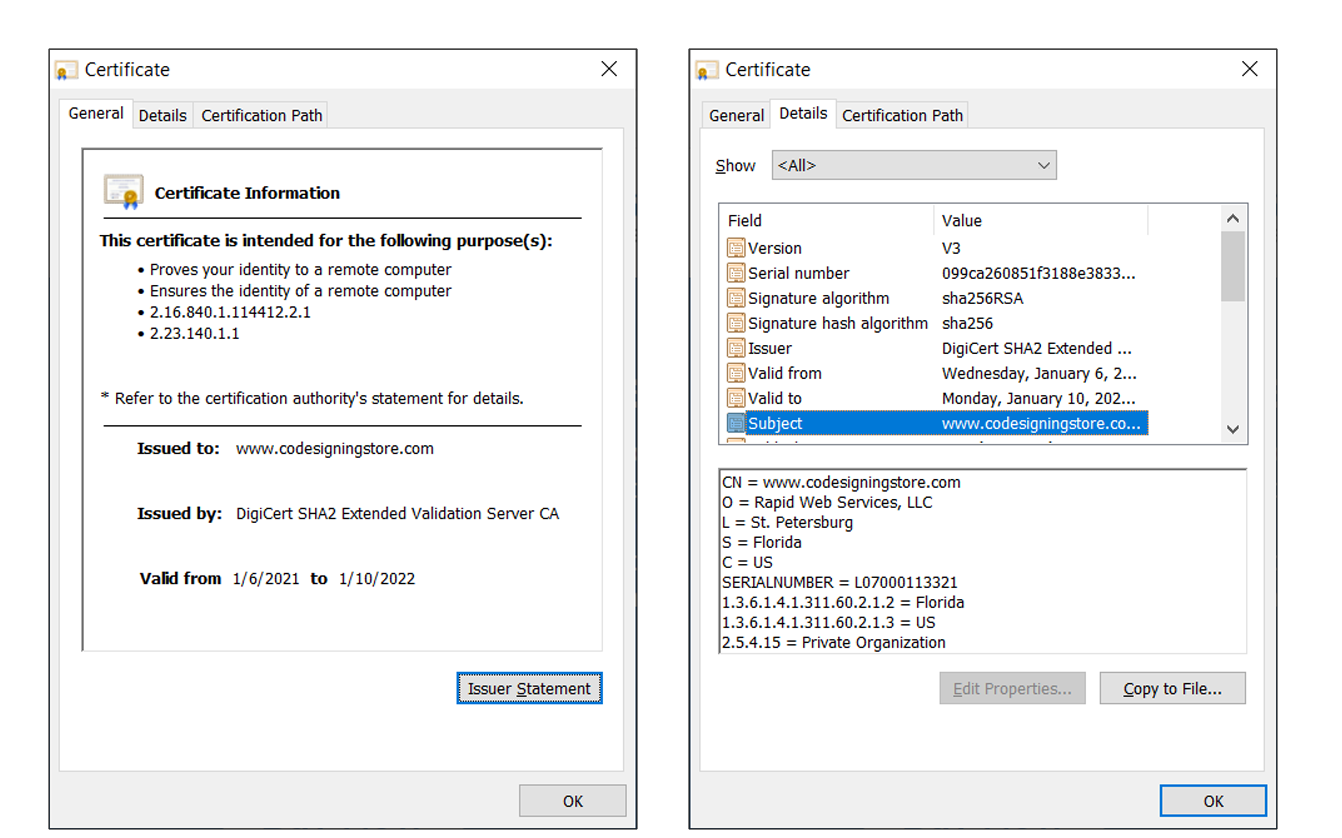
Of course, you can then use these records to check the information against official sources to make sure it matches.
Check the Site’s Trust Seal
Something else you can do also is look for a trust seal (trust badge) on the website. Reputable websites often use trust seals that certificate authorities issue to their website. For example, look at the footer navigation of eBay.com:
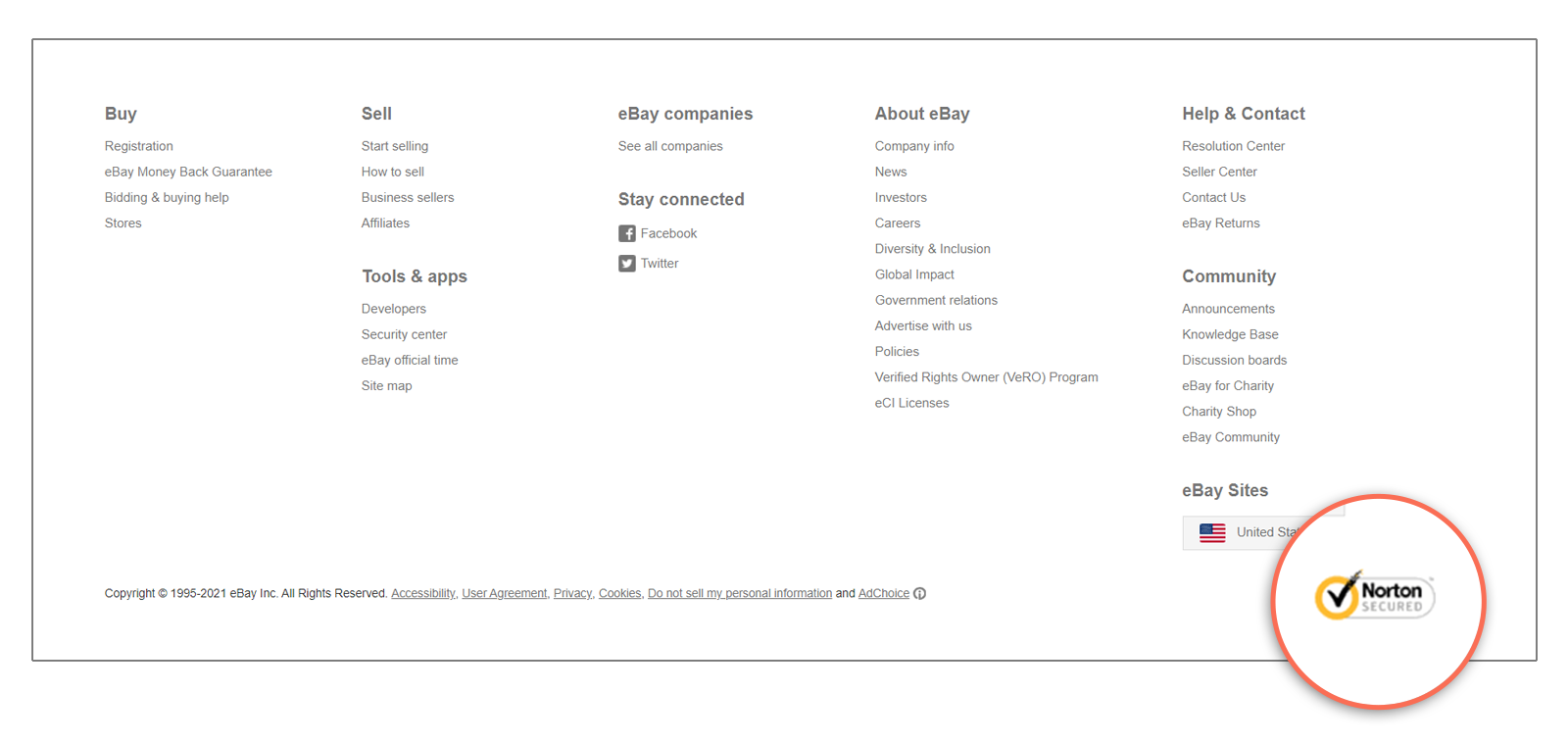
In the bottom-right corner, you’ll notice the Norton Secured site seal. But how do you know a real trust seal from a fake one? How can you
distinguish them?

When you click on it, it’ll take you to a page that tells you more information about the organization that the seal was issued to (in this case, eBay). In addition to that information, it’ll also provide a timestamp to ensure that the information is current.
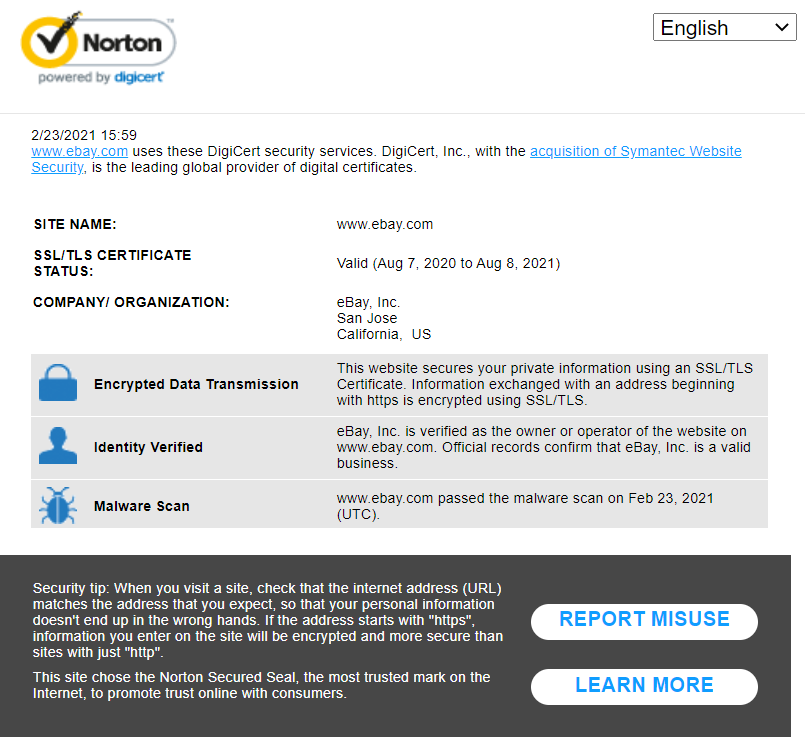
verified website andorganization information as well as how long the SSL/TLS certificate is valid until.
Other Tips for Browsing the Internet Safely
Here are some more quick tips for website surfing safety:
- Never share personal info or images you wouldn’t want your parents or another person seeing.
- Remember that the internet is forever; don’t share information, images, or video that you wouldn’t want your parents or friends to see.
- Always use unique usernames and passwords (never reuse them for other accounts).
- Never share your login credentials with anyone but your parents.
- Only use secure websites when creating profiles, sending emails, or otherwise transmitting personal or sensitive information.
- Avoid the use of public wireless networks. If you have to connect to public Wi-Fi, always use a VPN to protect your data.
How to Use Email Safely
Email has become an integral form of communication for kids, teens, and adults alike. Statista reports that 90% of individuals ages 15-24 use email as of 2019. Kids use it to register for accounts and communicate with friends; teens do the same, but they also use it to apply for colleges, scholarships and jobs.
But what email-related dangers do your kids and teens need to be on the lookout for?
- Phishing emails with malicious links (kids and teens),
- Malicious attachments such as images, PDFs, and Office docs (kids and teens),
- Phishing and malicious websites (kids and teens),
- Phishing and spear-phishing scams (kids and teens),
- Job and college recruiter scams (teens),
- Financial scams (teens),
- Scholarship scams (teens), and
- Sextortion scams (kids and teens).
- Online enticement/online relationships (kids and teens)
Examples of Phishing Emails
Here are a few examples of phishing emails that we’ve received:
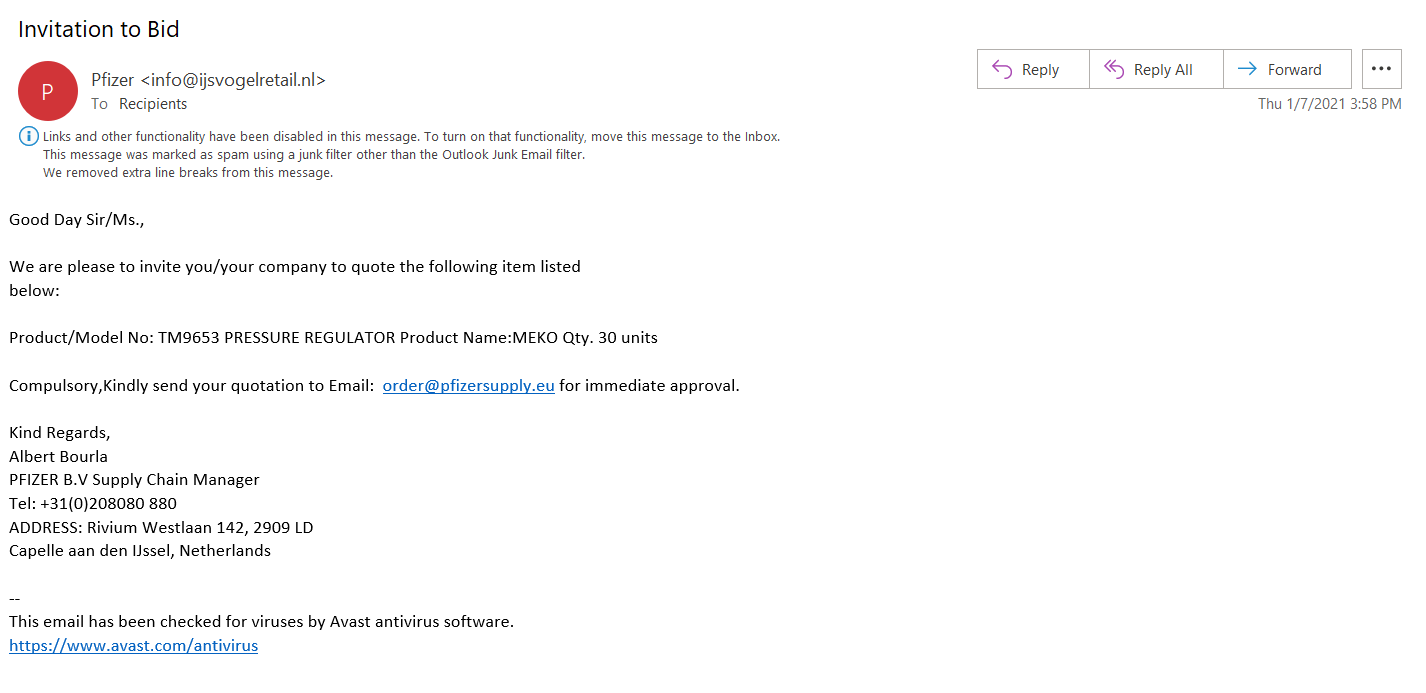
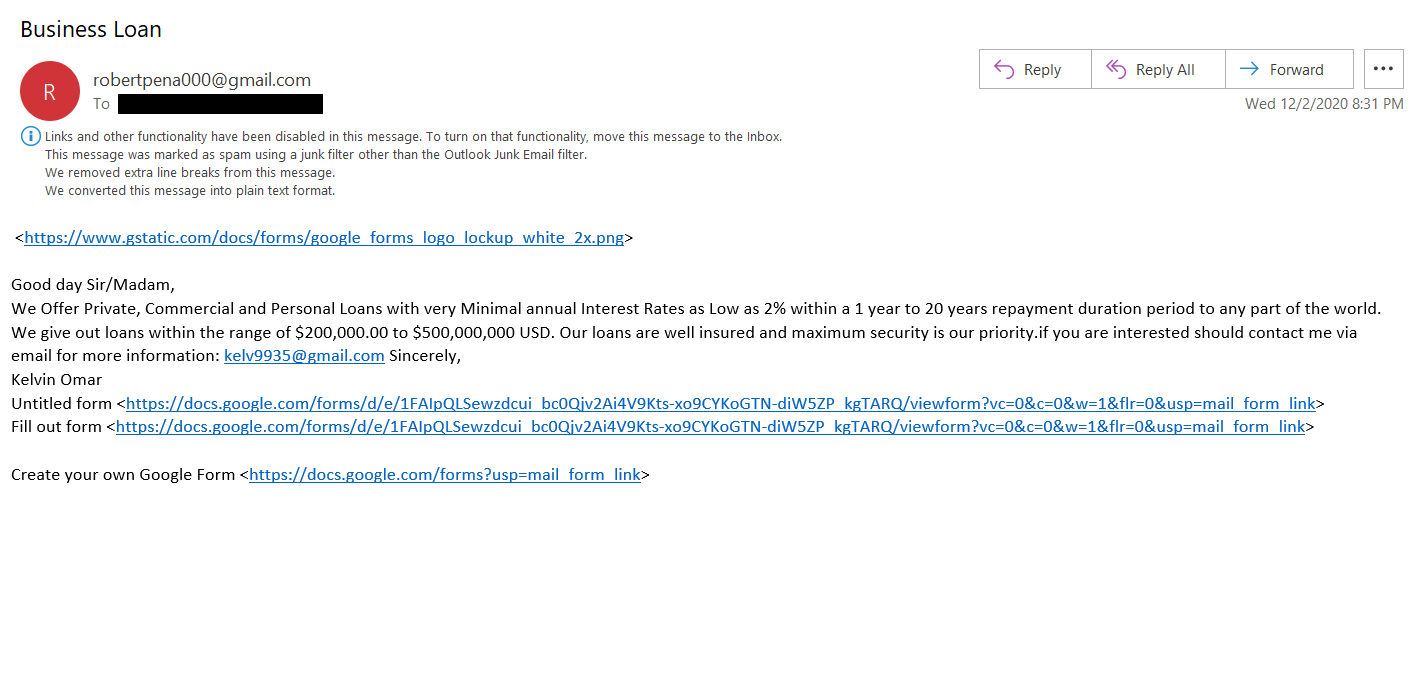
In this first example, you’ll notice that the sender’s display name (Pfizer) and the email address itself don’t match. If the email was from Pfizer, it would come from an email address that matches the company’s domain and not an unknown website like “ijsvogelretail.nl.” The second example email is all over the place. It’s sent from the email address [email protected], but the message says it’s from “Kelvin Omar” and tries to direct you to respond to a completely separate email address.
Needless to say, no legitimate business would ever send emails like this. Also, if the email was legitimate, it would address you by your name. Not “Sir/Ms.,” “Sir/Madame,” or any other generic form of greeting.
Tips for Using Email Safely (How to See If an Email is Legit)
In general, no one should open emails from people they don’t know. This is especially true for kids and teenagers. However, we understand that curiosity sometimes gets the best of us and people will wind up clicking on emails from unknown senders anyhow. So, whenever your kids and teens receive an email, remind them to take a few moments to check the following to see if it’s legitimate:
- Ensure the sender’s display name and email address match. This is the biggest red flag to call your attention. If it doesn’t match, mark it as junk and block the sender.
- Make sure the email address itself is accurate and isn’t slightly off. For example, emails from Amazon should come from addresses ending in “amazon.com” and not “amzon.com.”
- Read into the language of the message. Does any of it seem urgent or like it’s pushing you to take immediate action? Teach your kids and teens that if an email seems very demanding or urgent to bring it to your attention.
- Double-check the links. Before you click on a link in an email, be sure to hover your mouse over it first to ensure it’s legitimate. This will allow the true website link to display as an overlay.
- Avoid unusual attachments. If you receive an attachment you didn’t ask for, don’t open it. This is especially true for password-protected files. It’s likely malicious and will infect your device.
- Does the content make sense? Remind your kids to ask themselves, from a logic standpoint, if the message makes sense. Did they apply for a specific scholarship? Why would a coach or teacher send them an email asking for their login information?
If they receive an email that they realize is fake or a scam, it’s important that they flag the message as spam/junk mail and block the sender immediately.
Verify an Organization’s Digital Signature
Businesses and individuals alike can digitally sign and encrypt emails if they have the right tools at their disposal. This tool, known as an email signing certificate, adds a digital signature (basically, a long string of random numbers) to an email that tells your email client (Outlook, Apple Mail, etc.) that it hasn’t been messed with since it was sent. Let’s consider the following email as an example.
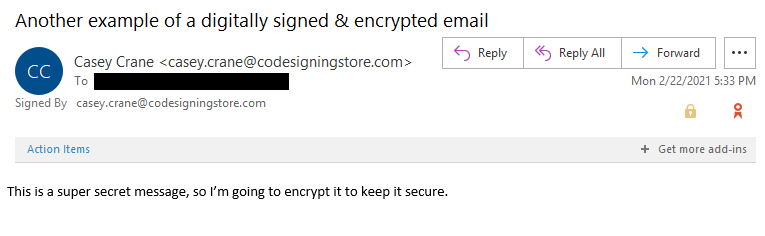
that the email has been digitally signed and secured via an encryption process.
In the screenshot above, you’ll notice that the email features a padlock icon and a badge. This first indicates that the email has been secured via encryption and the latter lets you know that it’s been digitally signed. Of course, you can click on either of those icons to pull up more information about the security of the message.
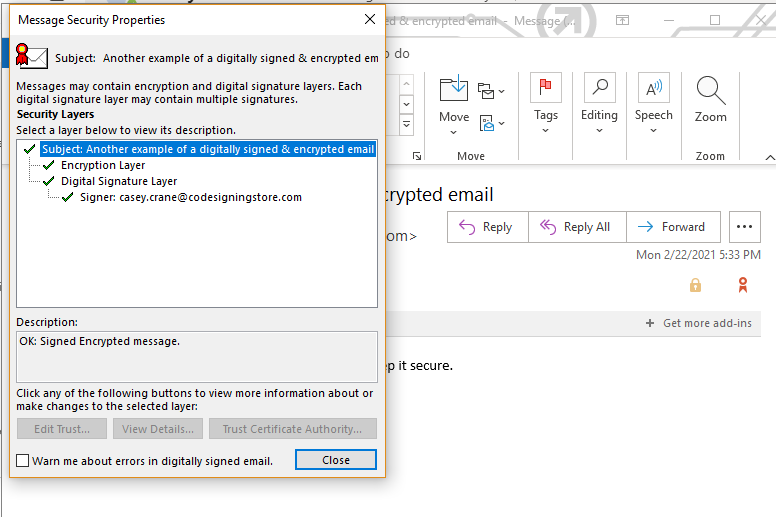
If you click on the checkmark line that says “Signer: [email protected],” you’ll be able to view additional details about the
email’s security.
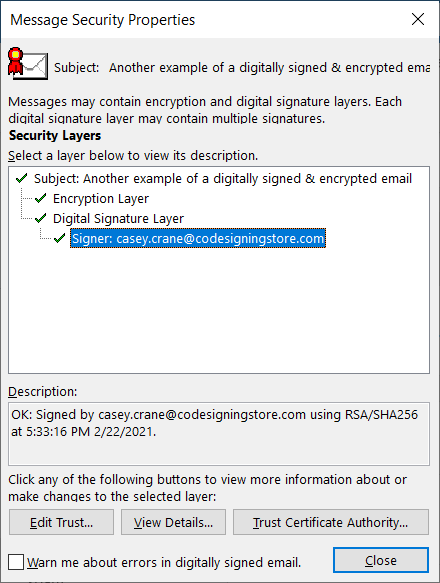
send a digitally signed and encrypted email.
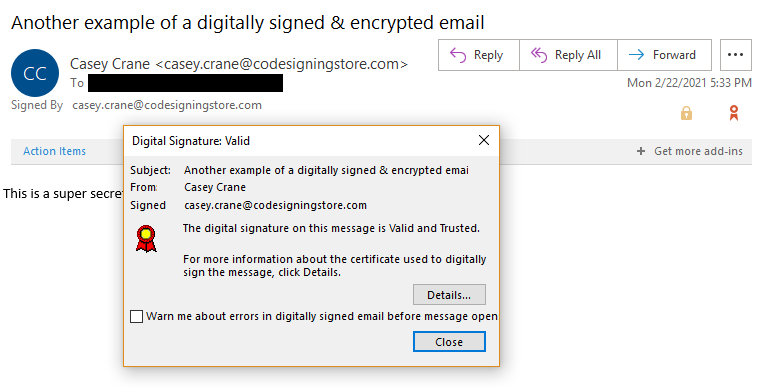
Although checking an email’s code signing certificate information is the best method for verifying emails, the reality is that only a few senders actually use them. The overwhelming majority of the emails that your kids and teens will receive won’t be signed. This is why it’s important that you — and they — use the tips that we covered for how to check the validity of an email.
How to Use Social Media and Chat Apps Safely
Social media and chat apps offer many benefits for kids and teenagers, including a way to keep in touch with friends and family who don’t live nearby. That’s why we’re going to lump them together. However, there are also risks that stem from social media usage, including:
- Exposure to inappropriate or illegal content
- Cyberbullying
- Cyberstalking
- Identity theft
- Phishing scams
- Financial scams
- Malicious ads and links that can install malware
There are plenty of online scams that target kids and teens. Some of the most common include:
- Fake postings about contests and free giveaways.
- Fake ads for free or inexpensive luxury goods.
- Messages about talent searches and modeling opportunities.
- Surveys that ask for seemingly unimportant private information.
- Grant, scholarship, and job opportunities.
- Messages that contain videos or images that are actually malicious (or direct to malicious sites).
Dangerous Apps Your Kids & Teens Should Avoid
Cronister says that some social apps are especially dangerous because they allow people to communicate without providing their personal information to register or saving any records of the conversations. While this is good from a user privacy perspective, it also makes it difficult for law enforcement to gather proof of any illegal activities involving children.
This can be anything from an adult sending a teen or child nude images to human trafficking-related communications. Because of this anonymity and lack of records, some of the potentially most dangerous apps include:
- Discord — What originally started as an app for gamers has morphed into something much bigger. Users can participate in group or direct messages. Although this app does have some privacy and safety settings, there are no parental control settings you can use.
- MeetMe — The point of this app is to create a profile of yourself with the ultimate goal of physically meeting up with someone.
- Snapchat — This messaging service allows users to exchange text messages, photos, and videos that will self-destruct automatically after a set amount of time.
- Telegram — This is another app that allows users to set expiration dates for messages they send. Once a recipient opens a message, it starts a countdown that indicates how long the message will remain before it destructs. While this option isn’t set by default, users can manually enable it.
- WhatsApp — This app chat app now allows users to share disappearing messages that will self-destruct as well.
- Whisper — This anonymous social networking app aims to create as much anonymity as possible by showing little to no identifying information (although it does show a geographic location). While this anonymity may sound good in terms of privacy, it could lead to situations to people posting inappropriate or threatening content that your kids and teens may see and having no way for you or law enforcement to identify the sender. It’s also been used by predators to lure kids for sex.
Facebook, which also owns Instagram, reports that in Q3 2020, 0.05%
of content violated their child nudity and sexual exploitation of children
policy on that platform.
Fake or Duplicate Profiles Are a Big Problem
But just how big of a problem are fake profiles? Let’s just consider the issue on Facebook to give you a little perspective.
Facebook reported in their U.S. Securities and Exchange Commission (SEC) filings report on Jan. 28, 2021 that 11% of their global monthly active users, or MAUs, in Q4 2020 were duplicate accounts. (Meaning that someone created a fake duplicate profile of real people, likely to try to dupe other people.) Considering that the company reports there being “2.797 million” (2.79 billion) active monthly users in December 2020 alone, that equates to roughly 307 million MAUsactive fake profiles.
Facebook also reports on their Transparency site that “fake accounts represented approximately 5% of our worldwide monthly active users (MAU) on Facebook during Q4 2020.” While this may not sound like a lot, but let’s remember that Facebook reports having more than 2.7 billion MAUs. This means that on Facebook (and Facebook messenger) alone, 16% of their accounts are either fakes or duplicates.
Facebook, which also owns Instagram, reports that in Q3 2020, 0.05% of content violated their child nudity and sexual exploitation of children policy on that platform. Basically, this equates to about five out of every 10,000 views containing that type of inappropriate material or content.
So, millions of fake user profiles are on chat and social platforms, and many of those people are up to no good. Here’s how you can find out who you’re really interacting with online.
Learn to Identify Fake & Duplicate Profiles
Fake profiles are a big problem on social media. People create profiles for people who don’t exist — often using stock images or stealing private individuals’ images that they gather through Google Images and other sources — to try to scam or blackmail people.
But how can you tell whether a profile is fake or duplicate?
- You don’t personally know the requester. If you don’t know someone, there’s no legitimate reason for them to try to connect with you.
- They aren’t friends with anyone you know. This concern goes hand-in-hand with the last point.
- You’re already friends with the requestor on a different account. Duplicate profiles are commonplace and involve someone creating a doppelganger profile with the hope that you’ll not realize you already have them on your network.
- The requestor uses poor grammar and spelling. This is often a big giveaway for scammers, many of whom aren’t native English speakers.
- The profile was created recently and contains limited or no information. Cybercriminals often don’t put a lot of effort into creating fake profiles because they know that they’ll have short lifespans. They rush to put profiles together to use for a short period.
- The profile’s images are all recent or limited. This goes along with the last talking point. If the profile has limited or multiple images that have recently been added prior to friend requesting you, it’s a big red flag.
- The requestor asks you to do something with a sense of urgency. Using language that evokes a sense of curiosity, fear, or panic is a tactic cybercriminals use to manipulate victims into doing what they want.
- The location of the person is overseas. A common scam (known as relationship fraud) involves a bad guy pretending to be a doctor or a soldier who is working or serving overseas. (You’ll see a perfect example of that momentarily.)
- A reverse search on Google shows other profiles using the image. Often with fake profiles, if you use Google’s reverse image search tool to check an image, you’ll see that the image has been used elsewhere online, especially on other profiles.
- The person’s social media activity takes place in odd hours for someone from that region. Say, someone says they live in Savannah, GA but all of their profile updates occur between 2 a.m. and 4 a.m. EST. This may indicate that the person doesn’t really live in Savannah.
Here is one such example of a fake profile:
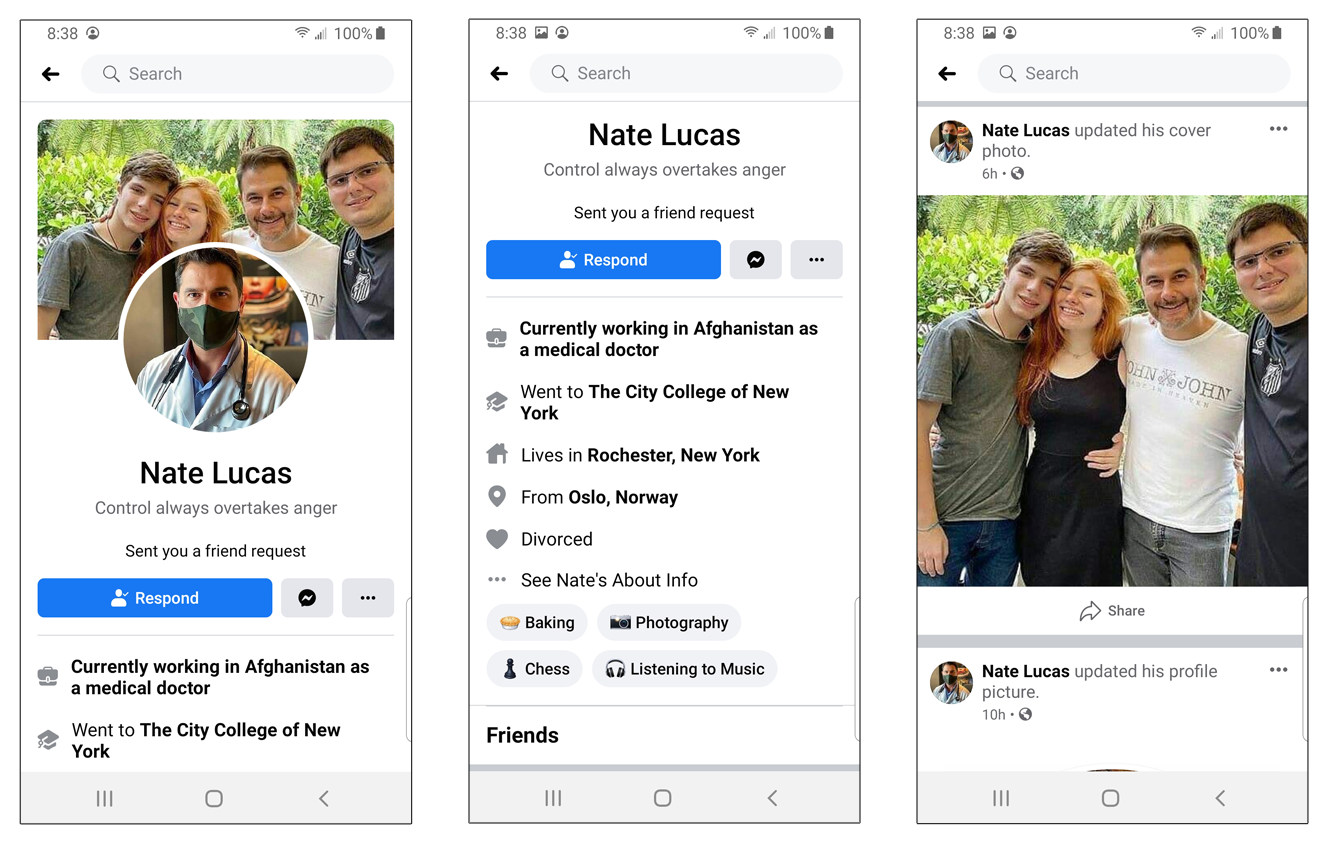
Now, one thing that’s important to note is that some fake profiles aren’t actually people — they’re really bots that spam users with advertisements, phishing links or malicious links. Here’s one such example that one of our employees received on their personal Instagram account recently:
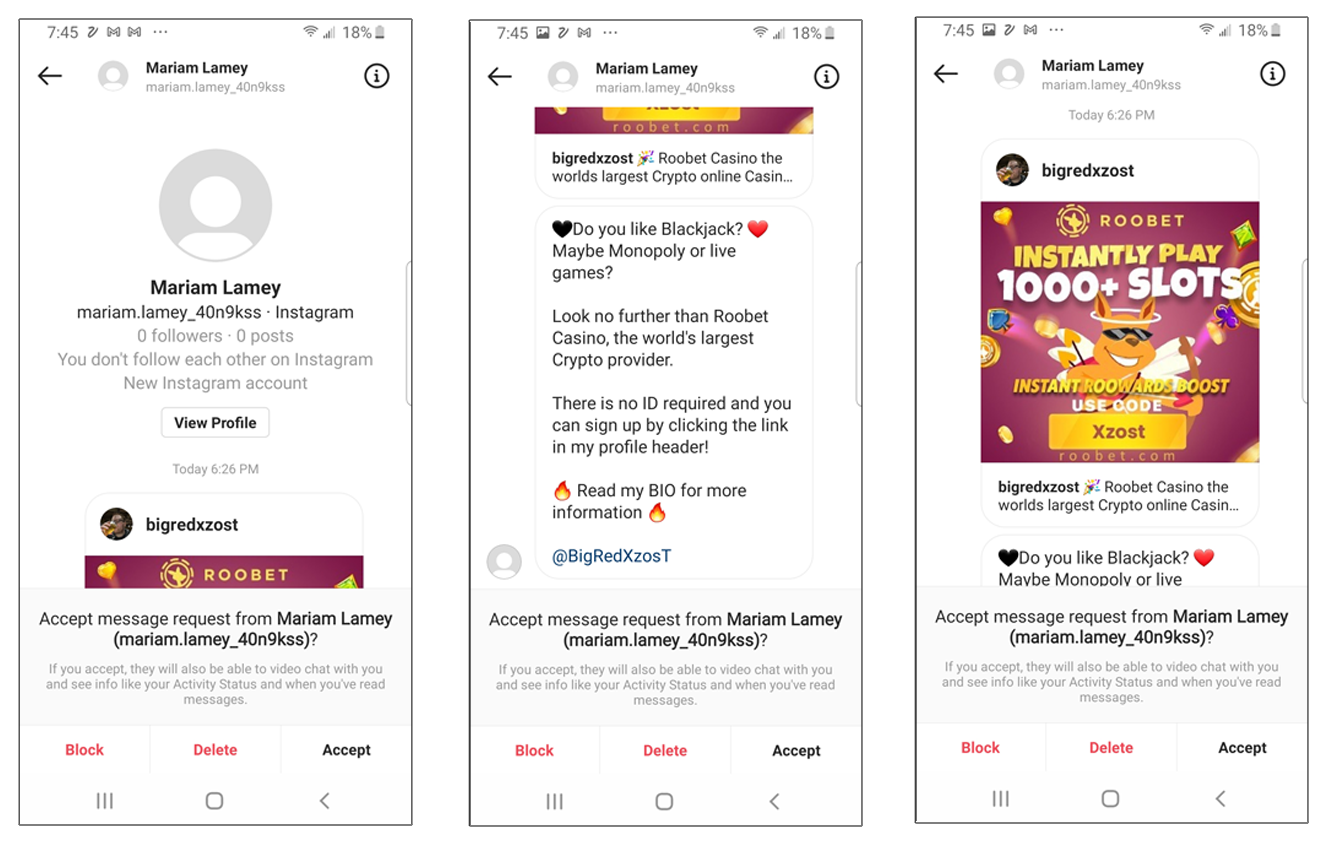
In the example above, you’ll see an unsolicited private message from someone that the recipient isn’t connected with who has no followers or posts. The message itself appears to be spam. However, it may contain a malicious link that could auto-download and install malicious software onto the recipient’s mobile device.
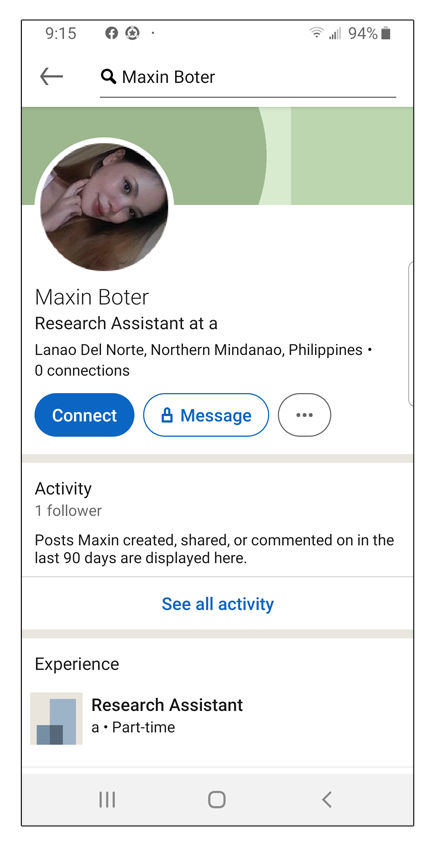
Here’s an example of a fake LinkedIn profile that requested a connection with one of our employees. Notice how the profile has no friends and no real information. This is an indication that the profile is likely fake. Another way to tell is if they have many people they’re following but no connections of their own. This type of profile could be used to gain access to profiles that are set to private for information-gathering purposes.
If you still aren’t sure whether the person you’re talking to is real, another method Cronister recommends is asking them to take a specific picture of themselves doing something. The image would need to be of them doing something specific — ideally, something that’s unusual or silly — or writing a specific unique word on a piece of paper. This prevents the person from using a stock image or an old photo because they’d have to do something specific at that moment.
But what should your kids do when they receive messages from unknown or potentially fake users? A good rule of safety is to think in terms of “stranger danger” for kids — never talk to strangers. This counts in both offline and online environments. So, what they should do is report any suspicious profiles to the platform (Facebook, Snapchat, etc.) and block ‘em!
Limit the Information They Share on Social Media
This is a big one. Kids and teens are often more open and trusting — or, in some cases, overly confident. This may make them more liberal and open in terms of sharing their personal information online. This is a dangerous mindset, Cronister warns:
“Most offenders are crafty enough to ‘friend’ or ‘follow’ children for long enough that the child becomes comfortable before attempting to victimize or groom them. They are oftentimes posing as kids themselves.”
Some other app privacy settings and considerations include:
- Setting their profiles to private to limit access to their images and information to only their network.
- Checking each social platform’s security settings and disabling unnecessary permissions.
- Not allowing other apps or platforms to connect to your kids’ or teens’ social media profiles.
- Reminding kids to not complete or publish surveys that ask for private information.
How to Use Mobile Devices Safely
Although we’ve already covered chat and messaging apps in the previous section, there are other threats that exist on mobile devices to talk about. This list includes:
- Other types of malicious applications
- SMS phishing text messages
- Vishing, or voice phishing
- Sexting
Malicious apps are a big issue as more kids and teens use mobile devices. Depending on their device permissions and settings, mobile apps can allow companies unfettered access to devices’ microphones, cameras, locations, images, and other files. This is not only a privacy concern but could also lead to safety concerns if someone chooses to use these capabilities to track, stalk, or spy on your child or teen.
SMS phishing text messages are those that appear to come from a specific brand and contain links to unknown sites. These scams may offer free or significantly discounted items to entice users to click on the links, which then take them to phishing or malicious websites.
Voice phishing is a growing issue for anyone with a phone number regardless of their age. A vishing phone call involves someone calling and pretending to be from a government, brand, or other organization. The caller uses social engineering to ty to manipulate you into doing something you shouldn’t or providing some type of personal or financial information. Some common vishing scams include people pretending to be from:
- The FBI or law enforcement,
- The Internal Revenue Service (IRS),
- Medicare or Medicaid,
- A car warranty company, and
- A well-known hotel chain.
Phone Settings and General Mobile Safety Considerations
Here’s a quick list of mobile privacy & security settings to turn on (or turn off):
- Set and enforce rules about phone and app usage.
- Give your child a phone with limited internet access.
- Turn on parental controls in the device’s settings.
- Enable “prevent changes” to stop your child from changing their password or data plan without your knowledge.
- Turn on web filtering on the device’s browsers.
- Turn on the “ask to buy” setting on an iPhone to ensure your kid can’t buy anything without your approval.
- Turn off location sharing for images.
- Turn on parental control settings on the device.
- Use parental control apps and services to monitor devices and apps, filter web search results, and set screen time & access restrictions.
- Restrict your kids and teens to using their devices during set hours or in open areas of the home.
- Remind them about the dangers of sharing sensitive and inappropriate information and images.
Malware can be anything from computer games to photo editing software
that kids and teens can use for their social accounts.
How to Download Apps Safely (For Computers & Mobile Devices)
Malicious applications are a concern whether you use a desktop computer, tablet, or a smartphone. Malware enables cybercriminals to carry out attacks, steal your passwords, change your security settings, and even record audio and video — all without your knowledge or approval. These apps are often disguised as legitimate apps or add malicious properties to legit apps.
Malware can be anything from computer games to photo editing software that kids and teens can use for their social accounts. So, how do you know what apps are safe to download? The answer is tricky because it’s difficult to know with 100% certainty whether an app is legitimate or has been compromised in some way. For example, a fake version of FaceApp circulated online that tricked users into downloading malware.
It’s for these reasons (as well as others) that it’s important you, as well as your kids and teens, know how to identify safe apps from potentially malicious ones. Here are a few good rules to go by when downloading apps onto computers or mobile devices.
Check the URL of the Site You’re Downloading From
If you’re downloading an app directly from a website, carefully review the website address. If it doesn’t match the official website of the organization, look elsewhere.
Only Download Apps from Trusted Sources
We can’t overstate the importance of using trusted sources on any device. For mobile apps, use trusted app stores like Apple’s App Store, Google Play Store, or Amazon’s Appstore. Never download software or apps from file-sharing sites like Torrent or third-party app stores.
While they do host some legitimate apps, these sources are notorious for hosting compromised apps and other malicious files. So, why risk eating one of many poisoned apples in a barrel just to find one or two legitimate ones? Simply put, the risk isn’t worth the reward.
Read the Reviews and Ratings
If an app has a lot of 1- and 2-star ratings or a lot of negative reviews, do not proceed with the download. Even if the app is legitimate and from a legitimate publisher, it may have a lot of unaddressed vulnerabilities that will leave your device at risk to hackers and other cybercriminals. Instead, it might be better to go with another legitimate app that has better reviews.
Ensure the Publisher and File Name Match
When preparing to download software on a PC, always check to make sure the software is digitally signed by a verified publisher. In Google Play, for example, read the publisher information and research them online. Run searches like “PublisherName app legit,” “PublisherName scam,” “AppName scam,” and “AppName legitimate.”
Also, when downloading the app, also be sure to review the security warning. If it includes verified publisher information, that’s generally a good sign. But if it says that the app publisher isn’t verified, or if it tries to publish an app name in place of a verified publisher, beware.
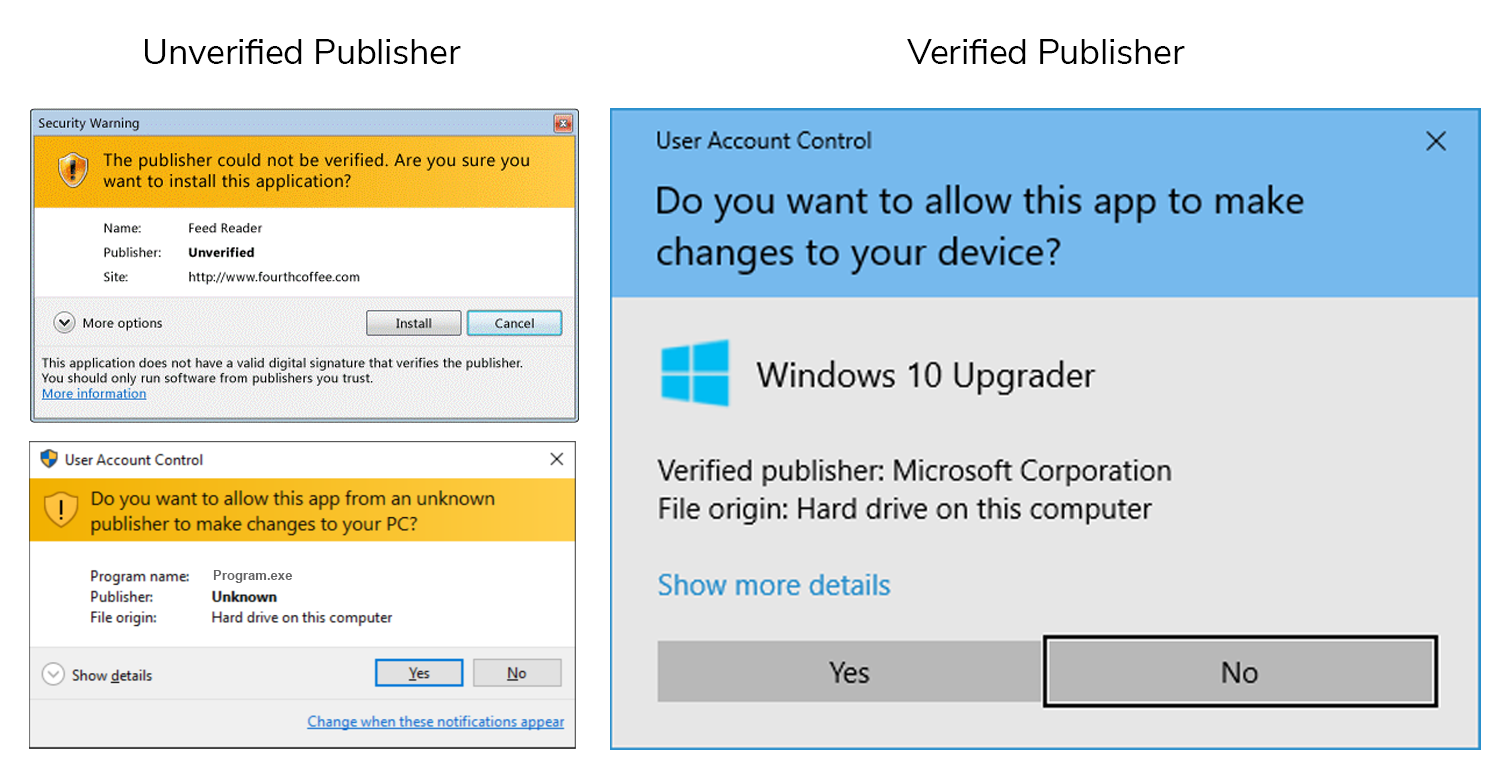
messages that inform you about verified and unverified/unknown publishers.
Where to Find an Organization’s Digital Identity When Downloading Apps
Whenever you download an app onto your computer, be sure to read the Windows security window that pops up carefully. Let’s consider the following example of a Windows 10 Upgrader installation window.
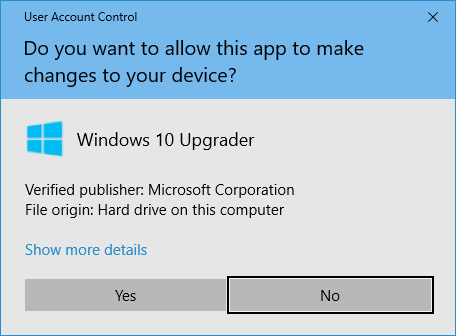
or reject an app’s ability to make changes to your device.
Here, you’ll see that Windows has verified that Microsoft Corporation digitally signed the app. It also tells you where the file came from — in this case, your hard drive. However, this may sometimes display a website address instead off where the app’s downloader files are hosted.
If the window displays a message saying “Publisher: Unknown,” teach your kids and teens that it’s best to proceed with caution and that they should come get you. This may be a warning that the file, which hasn’t been digitally signed, could be malicious.
For example, this is what verified publisher information looks like in Google Play:
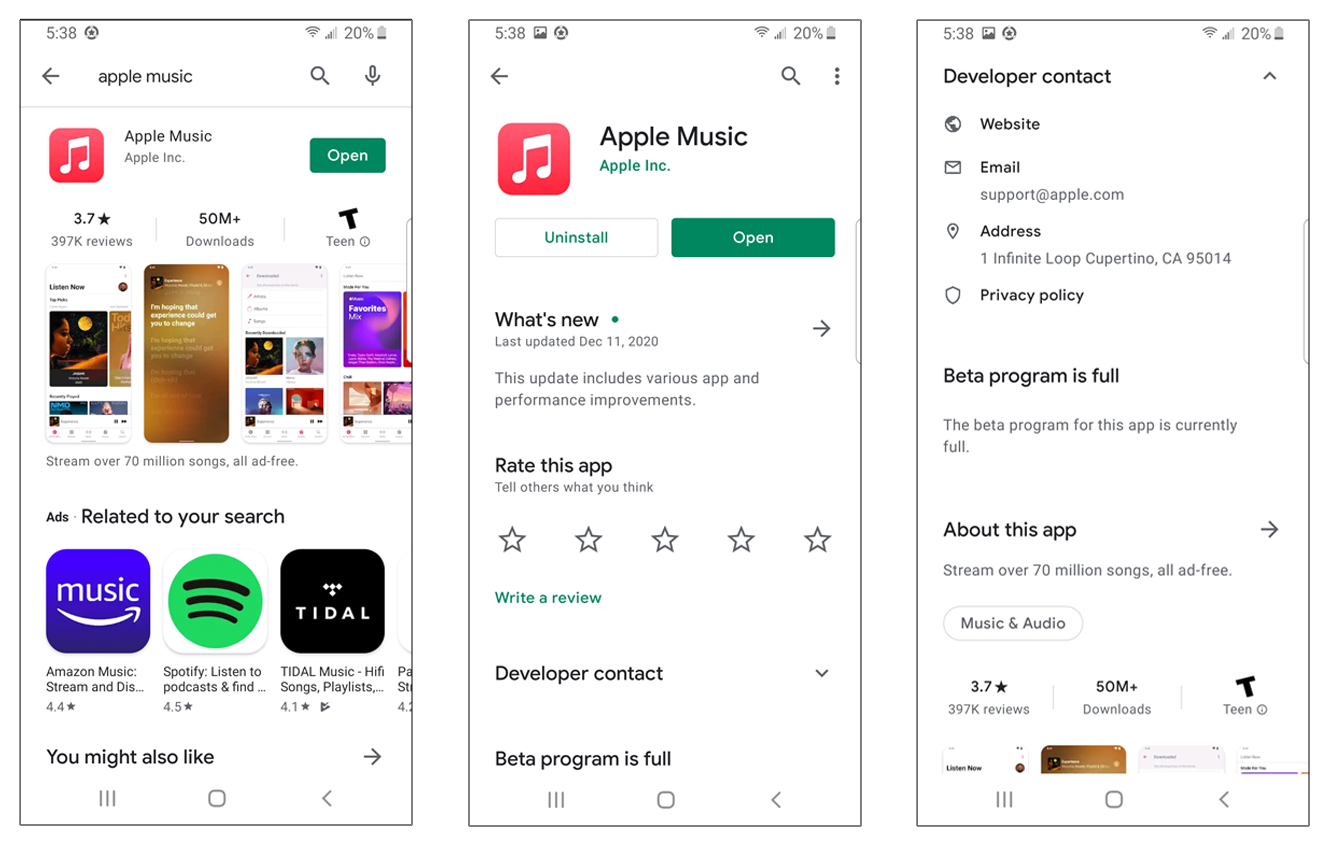
Avoid Unnecessary Downloaders and Installers
If you try to download a software program or app and a message tells you that you first need to download a separate program or installer, run the other way. This is often a scam to trick you into downloading potentially unwanted programs (PUPs) and adware. Virtually every operating system has the tools it needs to unpack and install software and apps on their own — or the apps themselves have the necessary tools pre-loaded that enable their installation.
Run Antivirus and Malware Scans
You can’t be too careful when it comes to checking the security and safety of apps. Another great recommendation is to always run apps through antivirus and anti-malware scans after downloading but before installing them onto your device. This allows you to check for any known malicious code or malware. It’s better to be safe than sorry.


