What Is Security as Code & How Can I Implement It?
$6.9 billion: so high are the latest FBI’s estimated potential losses from cybercrime in 2021. Discover how security as a code can help you and your organization prevent breaches, improve security operations, and survive the age of cyber warfare — all without breaking the bank or slowing down your development process
Today, delivering code fast has become a must — often to the detriment of security (unfortunately for everyone). However, as organizations move to the cloud (where most breaches are caused by misconfiguration, security can’t play Cinderella role anymore. Thus, traditional cybersecurity architectures and models are quickly becoming obsolete.
Find out how security as code can effectively replace more traditional (and outdated) security models. Discover how it can enable your organization to achieve a robust, scalable, and agile security program by strengthening the code at its core, right from the beginning. Learn how to get your developers to embrace security and your security specialists to think more like developers. Bring security to the heart of DevOps now.
What Does Security as Code (SaC) Mean?
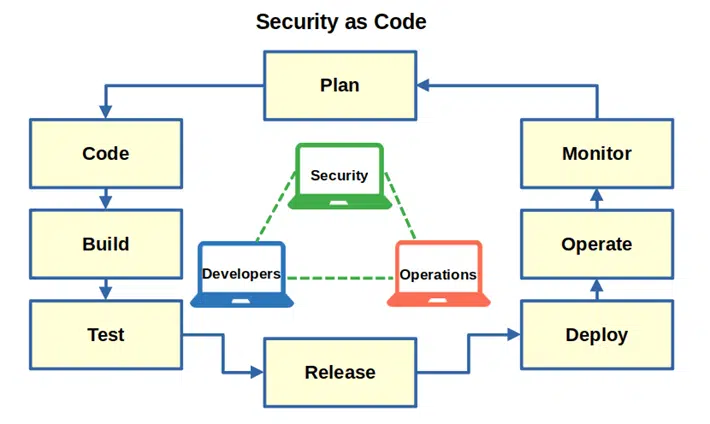
Security as a code (SaC) is the methodology that implements security practices, tests and policies in every step of the software development life cycle (SDLC) shared by development, security and operations teams. How? By:
- Bringing together the development, security, and operations teams (DevSecOps)
- Adding automated security checks, tests, scans, and policies to the process without delaying the product’s release or adding costs
- Implementing security compliance audits and checks as code along with security policies
But what’s the overall goal of security as code? The SaC aims to codify security checks and processes into the SDLC and infrastructure to keep things moving along while also ensuring that the software released is as secure as possible.
Let’s consider this with the analogy of constructing a house. When building a house, the whole process is defined in advance through a series of steps:
- You need to create an approved, documented plan. Having an approved plan in place helps to ensure that everyone involved knows what’s going on and how things should be set up.
- Regular inspections are performed in each stage. Conducting consistent tests and inspections help you keep an eye on things every step of the way. This approach helps to mitigate insurmountable issues further in the construction process by ensuring that things are OK throughout the process.
- When an issue is found, it’s fixed before moving to the next building step. That avoids unknown issues arising after you move in when it’s too late and too expensive for the builder to fix them.
This is much like how security as code works in an organization’s cybersecurity and development processes. With this methodology, security becomes an integral part of the entire software development life cycle (SDLC), right from the very beginning. Thanks to automated checks and tests performed during the whole process, vulnerabilities are identified earlier and quickly fixed. Thus, there aren’t nasty surprises at the time of release to have to deal with at the last moment.
Adopting a security as code approach is considered one of the best ways organizations can increase collaboration, agility, and security across their entire infrastructure by many businesses, including Microsoft and RedHat. All this without impacting quality and speed of delivery. In fact, security as code is considered so valuable and key for secure innovation that it’s been embraced by U.S. government bodies like the Department of Defense. You could even make this approach one of your software development best practices.
This sounds fantastic, right? But it also looks like some work will be needed to implement it so, why should you bother? What are the benefits? Let’s find it out.
Why Implementing a Security As Code Approach Matters
Like Charles Kettering once said, “The world hates change, yet it’s the only thing that has brought progress.”
Changes are never easy and usually don’t happen overnight, above all when involving a cultural shift. And this is exactly what implementing security as code into your software development life cycle (SDLC) is; it’s a drastic change that’ll require you to win the hearts and minds of the teams involved and the leaders of your organization overall.
However, the greater the effort, the sweeter the reward — and let me tell you, implementing security as code comes with a plethora of benefits. Which ones? Well, for a start, security as code:
- Fosters collaboration. Developer, operations, and security teams will start working together on shared issues and on the same code base. No one is left behind, no one is seen as a nuisance, and all teams are working toward the same goal: ensuring the code passes all tests and moves on to the next step.
- Increases visibility. Everyone in the developer, operations, and security teams has access to data, permissions, and policy changes. Need to track or request changes? No problem, it’s easily done.
- Shortens up the release cycle. When you’re integrating security requirements earlier in the design and development phases, issues can be addressed “right here, right now” before they become big problems. This means something that typically requires multiple sprints (often at the end of the deployment) will be resolved much faster, reducing the software’s time until release.
- Improves security and reduces costs. Every little bit helps. Each test, scan, or analysis you run often and continuously helps you identify and address issues at earlier stages. Thus, your application will be more and more secure, and you’ll save money on development costs.
- Boosts your teams’ morale and productivity. Collaboration among teams where everyone has a stake in what must be improved typically positively impacts teams’ morale. And happy employees are usually more productive employees.
- Simplifies the development process and reduces mistakes. Introducing more automated processes not only reduces the amount of manual work, but it also streamlines the SDLC and reduces the possibility of making mistakes.
Not bad, huh? And these are just a few of the key benefits that your organization will be able to enjoy once security as code has been implemented.
Where Can You Use a Security as Code Approach?
Have you ever heard a developer complaining because the security guys came up with a new vulnerability to fix at the last minute? Security is sometimes seen as a pain in the neck by developers and organizations trying to release software as fast as possible. If you’re a developer or project manager, I’m sure you know what I’m talking about.
Imagine if you had a dime every time a piece of code you thought was ready for release had to undergo more back-and-forth between the developer, operations, and security teams. If you’re like most software creators, it’s likely that you’d probably be very rich right now because this back-and-forth exchange frequently happens! (Then you could be sitting on your private island’s beach, enjoying the sunset, and drinking out of a freshly opened coconut.)
Coming back to reality now — wouldn’t it be wonderful if you could avoid such delays? But wait, you can! All you have to do is implement security as code directly into the continuous integration and continuous development (CICD) pipeline. We’ll talk more about CICD and its close relations with security as code in a moment. What’s important now to understand is that security as code will enable you to automatically and continuously detect security vulnerabilities, making things much simpler, faster, and hassle-free. Goodbye, delayed releases!
The cloud environment is another perfect fit for security as code. Have you ever tried to make cloud deployments fit into traditional security processes? If you know a bit about the cloud, you’ll know that it’s basically impossible. Its environment and infrastructure are too complex, and the workload required would be immense.
Once again this is where security as code can come to the rescue: just replace those outdated processes with it and you’ll see the magic happen.
How to Enhance Your Security as Code Process by Using Infrastructure as Code as an Example
One of the characteristics of security as code’s process is automation. As security checks, tests and audits are automated, so is the whole DevSecOps environment. A related concept is known as infrastructure as code (IaC). This entails managing your organization’s IT infrastructure through configuration code instead of setting up each component manually.
As businesses increasingly move to the cloud, the development and operations teams have begun working together as DevOps. They’ve also included IaC in their framework. Why? Because it enables them to create and manage infrastructure using code, thus speeding up things immensely. So long, manually managed servers, databases, operating systems, and such!
Security as code builds upon the advantages brought by IaC, enhancing your development process even further. How? By shifting security to the left in the development life cycle. This is done, in part, by including codes running automated security screening, testing, and feedback loop in each step of the CICD pipelines like:
- Code scanning and analysis. Automatically scanning the source code and containers for vulnerabilities (e.g., cross-site scripting, SQL injections) or performing a source composition analysis (SCA) to identify security issues introduced by third-party code or libraries.
- Security testing. Introducing security testing on each commit or pull request to identify vulnerabilities to attacks or insecure application configurations.
- Security fixes. Fixing vulnerabilities as soon as they’re identified without slowing down the pipeline or delaying the release of the software.
IaC, CI, CD, and security as code work together like the four musketeers (remember? All for one and one for all!). Once smoothly integrated, they’ll take your development life cycle process to the next level. The risk of including security vulnerabilities in your application will decrease, while your customers’ trust in your organization will grow.
How Do I Secure My Code?
Several tactics can help you bring security into your development process without undermining the rapid delivery and collaboration characterizing DevOps. Let’s have a look at the most important ones.
Providing Relevant Training to Key Stakeholders
When everyone is responsible for making applications more secure, all team members should know what’s all about. This doesn’t mean that a developer or an administrator must become security experts. However, they must have the basic security skills that’ll enable them to collaborate and implement security as code. How?
There are several certifications and training to choose from, for developers, administrators, and security professionals alike. Many are available as online courses offered by organizations like the DevOps Institute, Exin, Practical DevSecOp, and GIAC:
- DevSecOps – Integrating Security into DevOps,
- Secure DevOps: A Practical Introduction,
- Cloud Security and DevSecOps Automation,
- DevSecOps Foundation,
- DevSecOps Practitioner,
- Certified DevSecOps Professional,
- Cloud Security Automation, and more.
Choosing and Implementing the Right Tools
Need to do something to enhance collaboration? Or are you looking for a tool that would help developers secure source code through iterative threat modeling? The tools listed below are just a few examples of what is available out there to support your teams in successfully implementing security as code:
- Log management tools. To be used by all teams, an effective log data management like Logstash and LogDNA will improve communication and help to identify trends and weaknesses. It’ll also make the key information easy to find and always available to all team members.
- Monitoring tools and dashboards. This is the best way to know what’s happening across your applications, deployments, and infrastructure. Right here, right now. And if you build dashboard monitoring the following items, the chances of issues going unnoticed will be greatly reduced:
- Malicious login attempts,
- Identifying suspicious activity and
- Application errors.
- Alerting tools. There’s no effective monitoring without alerts. (Going through a bunch of event logs isn’t practical, and key data can get lost in all the “noise.”) You’ll get a more efficient response when issues arise if you ensure that the right people are warned on time using tools like:
- Orca Security,
- WhiteSource, or
- tCell.
- Threat modeling. As the adage goes: hope for the best but prepare for the worst. Having the right threat modeling tools at your disposal will help your teams identify, predict, and understand threats and their impacts. They’ll also enable them to figure out how to mitigate risks before they happen using tools like:
- OWASP’s Threat Dragon,
- Microsoft threat Modeling Tool, and
- ThreatModeler.
- Automated testing. Once again, ensure your teams are ahead of the pack and can identify security vulnerabilities before releasing your code. There are many testing tools you can choose from; just pick the ones you need the most to help you achieve the following:
- Code review on pull and commit requests,
- Continuous code inspection,
- Interactive application security testing (IAST),
- Static or dynamic code analysis, and
- Software composition analysis.
- Collaboration tools. Using collaboration platforms can help your teams deliver secure software faster and work more efficiently. Tools like the following examples can help you focus on delivering value while identifying issues more easily:
- GitLab,
- Kubernetes,
- Jira, and
- Jenkins.
Before you start filling in your teams’ toolbox though, make sure you do your research and check with your teams to see if they have recommendations. Then — and only then — select the right tools for your organization. Because remember: one size doesn’t fit all.
Defining and Documenting Your Processes
Having clearly defined and documented processes is crucial as they serve as the basis of your SDLC. Get them wrong and your plan of embedding security into your development process will fail. How can you then create a successful model for sustainable security?
- Adopting a bullet-proof common development process. Three different teams usually mean three different processes. To be successful, you’ll need to find a common process that all three teams will follow. Get these groups together, brainstorm, and put their collaborative ideas on paper. It’s a bit like making three chefs work together to bake a cake: each of them will have his own recipe. But if the goal is to bake a nice cake together, they’ll have to follow a commonly agreed-upon recipe.
- Document your process and make it available to everyone in the teams. To further facilitate cooperation and avoid misunderstandings, make sure the new process is well documented in all its steps and clear to everyone. Once put on paper using tools like Confluence, it will be much easier for new and old team members to follow it. And don’t forget to update it in case of any agreed upon changes.
- Including automation in your process as much as you can. As automatic tools are going to be a fundamental part of your security as code toolbox, automation must be included in your SDLC process. This will ensure that your teams won’t go back to using outdated methodologies or waste precious time on manual tasks that could be automated. Using automation frees up your teams from doing repetitive manual tasks so they can focus on higher-level functions that require their specialized skills and critical thinking capabilities.
- Ensure you have a clear and documented incident management and response process. No matter how hard you work and how perfect your security as code method is, security incidents can (and will) still always occur. A strong incident management and response plan and workflow will ensure that your teams will be prepared to respond quickly and effectively when bad luck strikes.
Changing Your Culture
You can have all the most wonderful technologies, processes, and skilled team members in the world, but if your organization’s culture doesn’t evolve to support the changes you need to make, then those changes won’t be successful. In the beginning, you may encounter a lot of difficulties and resistance from employees. But once the people within your organization understand the benefits coming from these changes, things will likely get easier.
How can you do that?
- Start from the top. Work to gain executive support and engagement so that having strong security becomes tied to business objectives. Present things in terms they’ll understand (i.e., avoid industry jargon) and speak to what they most want to know: how your proposed initiatives will benefit specific objectives (sales and revenue, compliance, brand reputation, etc.).
- Set-up a security champion figure. Adding a security champion to the teams will give them an example to follow and provide them with security expertise and mentorship.
Because with security as code, security becomes a mindset and a goal common to all departments and teams.
Final Thoughts on What Is Security as Code & How Can I Implement It?
Implementing security as code can be a significant shift for most organizations. However, adopting this approach will also help you save time, money, and resources in the long run and help you create more secure products. How? By enabling your teams to:
- Implement a more modern and resilient approach to application development
- Deal with security issues at the forefront of the development cycle, and
- Deliver a final (and more secure) product quickly.
Long gone are those days when security was just an afterthought at the end of the development process. Security as code has now become a fundamental element of application development that empowers you and your teams to ensure a secure and compliant configuration.
So, are you ready to take the next step and switch to security as code? Then don’t miss our next article where you’ll learn some secure coding practices you can immediately implement. And, while you’re waiting, why don’t you find out more about secure DevOps and the difference with DevSecOps?



