What are the Validation Requirements for Individual Code Signing Certificates?
If you’re an Individual software developer or a publisher who develops software and applications, then the requirement for code signing is a little different, as Individual Validated Code Signing Certificates are required. And those keep getting harder to find. Here, the identity of a single developer is verified by a Certificate Authority (CA), instead of the legitimacy of an organization as a legal entity.
To get an IV Code Signing certificate there are three different requirements:
1. Identity Verification
No matter what Certificate Authority (CA) you choose, the first requirement will be Identity Verification.
During this step the CA verifies the personal identity of the applicant, which can be proven by submitting a notarized ID form. The ID form is sent via email by CA and it can even be downloaded at the time of the initial application.
Apart from the ID form, you also have to provide additional documents, though the requirements differ from one Certificate Authority to another.

For DigiCert, Thawte or Symantec:
If you choose to go with DigiCert, Thawte or Symantec, you will have to send one, possibly two forms of ID. Ideally, if you have a valid passport that contains your full name and your photograph, you can get away with just sending a copy of that.
In case if you don’t have a passport, you must submit two forms of ID. The first one must be a Government-Issued identity containing your full name and photograph, such as:
- Driver’s License
- Military ID Card
- National or State ID Card
Apart from this, you also need to provide a second type of ID, along with the Government-Issued ID, which includes your full name. For example,
- Utility Bill
- Social Security Card
- Medical Card
- Student ID Badge
Once you send the notarized form and a passport or two other alternative forms of ID, your requirement will be fulfilled.
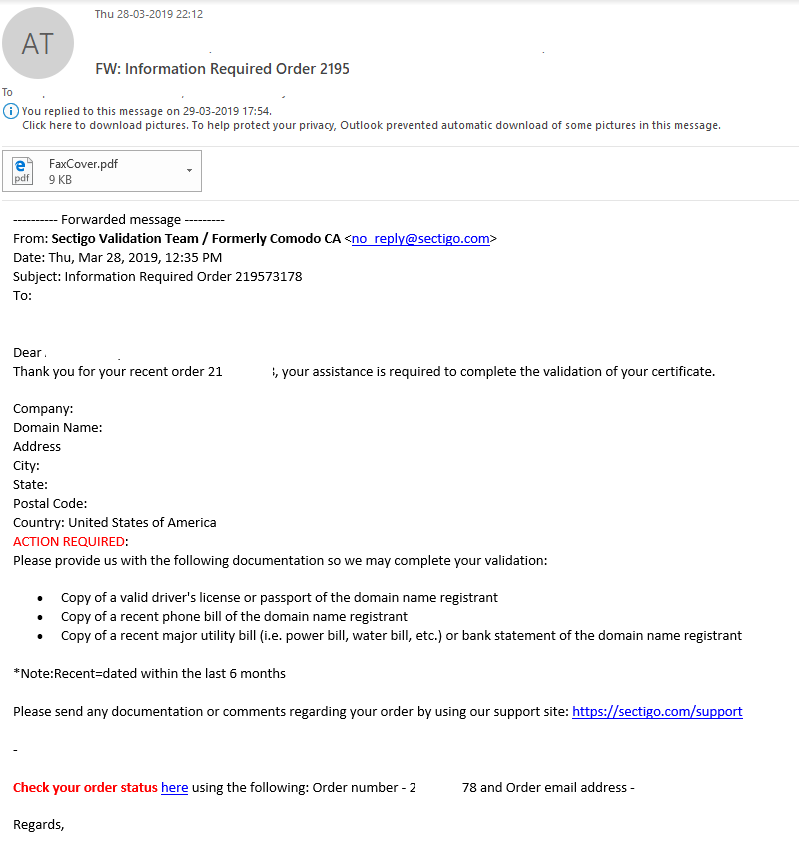
For Comodo/Sectigo:
For its identification verification, Comodo CA/Sectigo has a little more stringent vetting process. Along with Government Issued Identification, you will also have to provide two additional forms as secondary evidence.
Examples of Government-Issued ID:
- Personal ID Card
- Military Card
- Driver’s License
- Passport
Additionally, you will also have to provide a financial document that contains your full name. For example:
- Bank Statement
- Credit Card Statement
- Debit Card Statement
- Mortgage Statement
Lastly, a non-financial document containing your full name. For example:
- Birth Certificate
- Tax Bill
- Utility Bill
- Lease Agreement
Once you provide all the requisite documents and forms (Government-Issued ID and two additional documents), the validation process for Individual Authentication will be satisfied.
2. Telephone Verification
After the completion of the first step, Identity Authentication comes Telephone Verification. Here, you have to prove that your telephone number is valid and active.
Though there’s one thing to note that, only Comodo/Sectigo CA requires Telephone Verification from an accepted third-party telephone directory whereas other CAs, like Thawte and Symantec, will call whichever number you provided during enrollment.
To satisfy ‘Telephone Verification,’ the given Telephone number should be active, listed and registered by an acceptable third-party telephone directory like
- White Pages
- Yellow Pages
containing an active listing of a telephone number with your full name and physical address.
Additionally, if the listing about you is not there is an accepted third-party directory, Comodo/Sectigo also allow you to use a Legal Opinion Letter, also known as a Professional Opinion Letter (POL), a document that is signed by an attorney or accountant, vouching for your personal information.
3. Final Verification Call
The Final Verification Call is the last verification step. As the name implies, you will receive a verification call from someone from the Certificate Authority and you need to handle that call and answer the simple questions asked by them.
If due to any reasons your listed phone number does not connect with you directly there are alternative methods like:
- IVR or Extension:
If the phone system is using any extensions or Interactive Voice Response (IVR) and you have mentioned this in the submitted documents, there will not be any problem and the CA will go through the system to connect with you.
- Alternative Number or Transfer:
If the given number didn’t connect to you directly and goes through an operator or receptionist who can connect the CA with you, there’s no issue as the CA will work through it.
Once this last requirement is satisfied, the CA’s will send you an email within a short period that will include a download link to your code signing certificate.
Lastly, the requirements depend upon the Certificate Authority, for instance, Comodo does a telephone verification whereas Symantec does not, though both try to verify the same thing, that you are a genuine software developer and your code is trustworthy.

Save 21% – Individual Code Signing Certificates
Protect Software Code & Avoid Pesky Warnings


